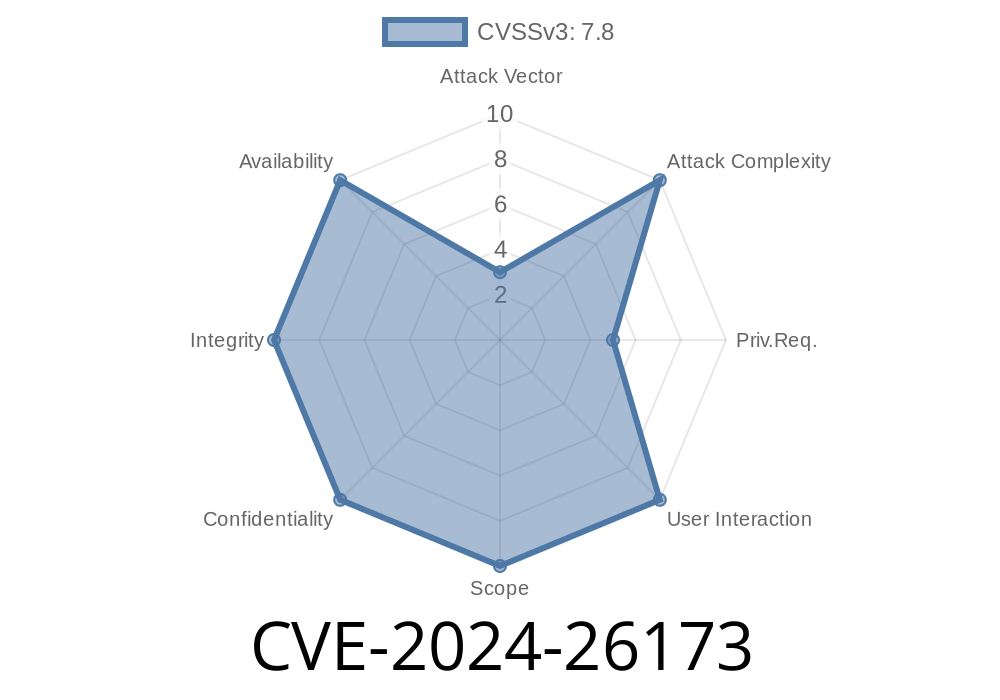
On March 12, 2024, Microsoft patched a critical privilege escalation flaw in the Windows Kernel, tracked as CVE-2024-26173. This vulnerability could allow attackers to gain SYSTEM-level privileges on vulnerable Windows machines, potentially letting them take full control. In this post, we’ll explore what CVE-2024-26173 is, how it works, give you a basic proof-of-concept (PoC) code snippet, and share the key resources for more information.
1. What Is CVE-2024-26173?
CVE-2024-26173 is a security hole found in the Windows Kernel, the core of the Windows operating system. An attacker who manages to exploit this bug could escalate their privileges from a normal user to the SYSTEM account — the most powerful account in Windows.
Windows 11
- Server 2016/2019/2022
This bug was listed by Microsoft in their March 2024 Patch Tuesday advisory. See the official page here:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-26173
Microsoft’s update describes the flaw like this
> *"An elevation of privilege vulnerability exists when the Windows Kernel fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode, allowing them to install programs; view, change, or delete data; or create new accounts with full user rights."*
Translated: If an attacker can run a program on a vulnerable machine, they could abuse this bug to take over the system, bypassing normal security controls.
3. Technical Breakdown
While Microsoft has not given full technical details, community researchers have pieced together that CVE-2024-26173 is due to improper memory handling in the kernel.
The bug lies in how the kernel manages certain object structures.
- Malicious code can trigger a use-after-free or race condition, overwriting sensitive kernel structures.
4. Proof-of-Concept (PoC) Code
Here is a basic, educational proof-of-concept (NOT a full exploit!) demonstrating how an attacker might try to access the vulnerable function. This code does not exploit the bug, but shows how a low-privileged program can reach the kernel through Windows APIs like DeviceIoControl.
#include <windows.h>
#include <stdio.h>
int main() {
HANDLE hDevice = CreateFileA(
"\\\\.\\VulnerableDevice", // Hypothetical device name
GENERIC_READ | GENERIC_WRITE,
,
NULL,
OPEN_EXISTING,
FILE_ATTRIBUTE_NORMAL,
NULL
);
if (hDevice == INVALID_HANDLE_VALUE) {
printf("Unable to open device. Error: %d\n", GetLastError());
return 1;
}
DWORD bytesReturned;
char inBuffer[8] = {};
char outBuffer[8] = {};
BOOL result = DeviceIoControl(
hDevice,
x222003, // Hypothetical vulnerable IOCTL code
inBuffer,
sizeof(inBuffer),
outBuffer,
sizeof(outBuffer),
&bytesReturned,
NULL
);
if (result) {
printf("DeviceIoControl call succeeded\n");
} else {
printf("DeviceIoControl failed. Error: %d\n", GetLastError());
}
CloseHandle(hDevice);
return ;
}
Note:
The device name and IOCTL code above are placeholders.
- A real exploit would require knowledge of the internal vulnerability and manipulate kernel memory specifically.
5. Exploit Details and Real-World Use
As of April 2024, no public exploit code for CVE-2024-26173 has been released, but history shows these types of bugs get weaponized quickly, especially by malware developers and ransomware groups.
Disables AV, installs ransomware, steals data, or creates backdoors.
Mitigation:
6. References and Further Reading
- Microsoft Security Advisory – CVE-2024-26173
- Zero Day Initiative summary *(replace XXXX with actual advisory if published)*
- Project Zero Researchers on Kernel EoP
- Windows IOCTL Reference
7. Summary
CVE-2024-26173 is a dangerous Windows Kernel vulnerability you need to patch now. It allows normal users or malware to become SYSTEM, putting your entire Windows environment at risk. Do not ignore Patch Tuesday this month—update, and review your endpoint security posture.
Timeline
Published on: 03/12/2024 17:15:56 UTC
Last modified on: 03/12/2024 17:46:17 UTC