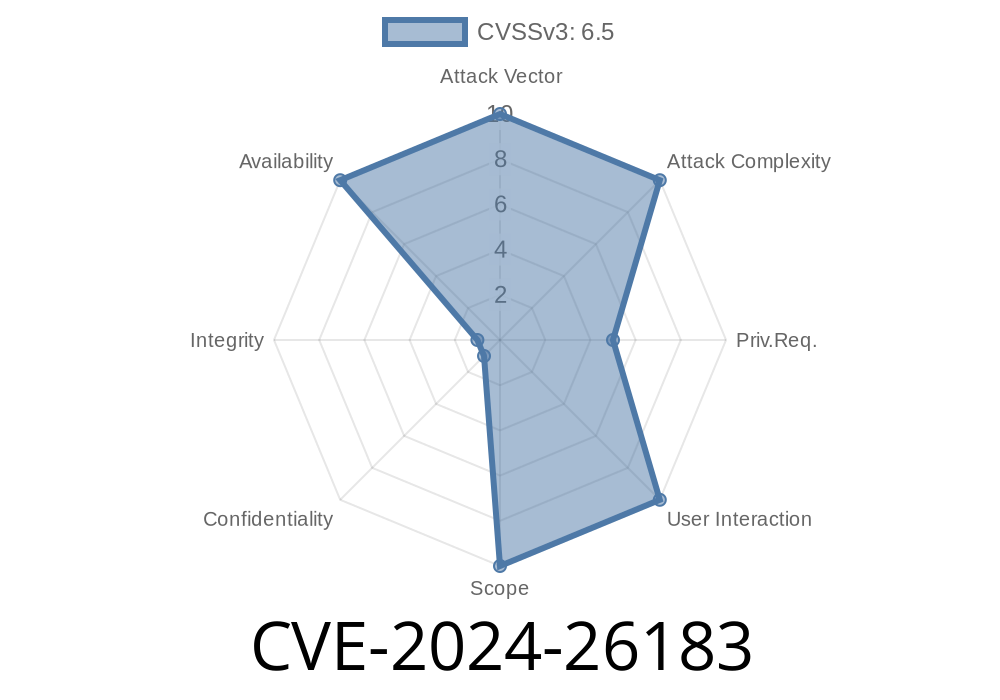
If you use a Windows computer in any sort of business environment, chances are you rely on Kerberos authentication every day, even if you don’t know it. In February 2024, Microsoft released information about a significant vulnerability, tracked as CVE-2024-26183, which affects the Windows implementation of Kerberos. If this vulnerability is exploited, it can cause a denial of service (DoS) attack, bringing authentication services to a halt and potentially locking users out of corporate resources.
In this post, we’ll break down what CVE-2024-26183 is, how it works, see some code examples, and show you where to read more.
What is Kerberos?
Kerberos is a network authentication protocol used in Windows domains. It lets users prove their identity securely over unsecured networks. It relies on tickets and a trusted key distribution center (KDC), usually a Domain Controller in the Windows world.
What is CVE-2024-26183?
CVE-2024-26183 is a denial of service vulnerability found in the way Windows processes Kerberos authentication requests. An attacker who can send crafted Kerberos requests to a vulnerable Domain Controller can cause the Kerberos service to stop responding. This can lock out users who try to log in or access resources on the network.
Risk: Denial of Service (DoS), which can halt logins and access to systems
- Affected platforms: Many supported Windows Server editions (see Microsoft Security Advisory)
How Does the Attack Work?
The attacker sends specifically crafted Kerberos packets to the Key Distribution Center (KDC). Instead of being processed normally, these packets hit a bug in the Windows Kerberos KDC process and cause it to crash or hang, denying service to all legitimate requests.
While proof-of-concept code has not been released by Microsoft, security researchers have described the issue as an improper input validation leading to a crash.
Sample Exploit Code Snippet
> WARNING: This snippet is for educational purposes only.
> Never run exploit code on networks you do not own or have permission to test.
A simplified version in Python might look like this
import socket
def send_crafted_kerberos_packet(target_ip, port=88):
# Craft an intentionally malformed Kerberos packet (pseudo code)
# Real exploit would require deeper protocol abuse
malicious_packet = b'\x00\x00\x00\x10' + b'A' * 16 # Not a real Kerberos message
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target_ip, port))
s.sendall(malicious_packet)
print(f"Sent crafted packet to {target_ip}:{port}")
s.close()
except Exception as e:
print(f"Error: {e}")
# Usage (example: attacking a DC at 192.168.1.10)
send_crafted_kerberos_packet('192.168.1.10')
Note: The actual exploit may require deep knowledge of ASN.1 encoding and Kerberos protocol, and different crafted data.
Patch Now: Microsoft released a patch in February 2024. Update all Domain Controllers!
2. Firewall: Restrict KDC traffic. Make sure only trusted IPs can send to TCP/UDP port 88.
Microsoft Security Advisory:
NIST National Vulnerability Database:
Kerberos Protocol (Wikipedia):
https://en.wikipedia.org/wiki/Kerberos_(protocol))
Patch Download Page:
Summary
CVE-2024-26183 is a classic example of how one weakness in a critical system service like Kerberos can ripple through an entire enterprise. If left unpatched, it could be used to disrupt business operations and deny users access to resources. Always patch promptly, limit exposure, and keep an eye on your critical infrastructure.
If you want to dig deeper or have seen suspicious Kerberos behavior, check the Microsoft and NIST entries above—and keep your systems up-to-date!
Timeline
Published on: 04/09/2024 17:15:36 UTC
Last modified on: 04/10/2024 13:24:00 UTC