Publish Date: June 2024
Author: [Your Name]
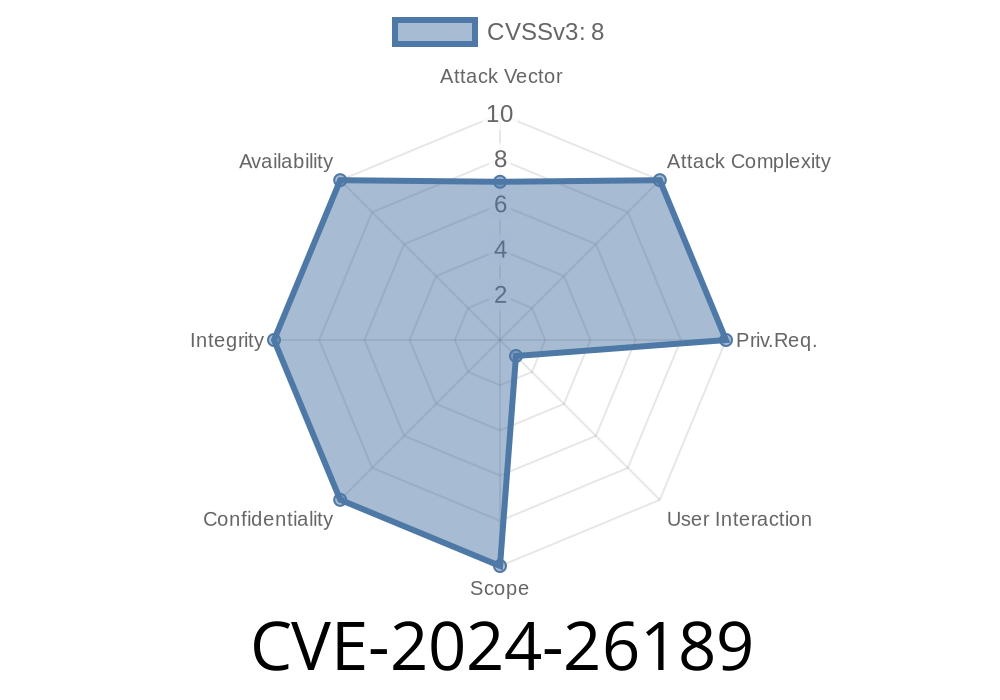
*If you think Secure Boot guarantees your Windows machine is locked down, think again. CVE-2024-26189, a Security Feature Bypass vulnerability, tears a hole in Secure Boot, giving hackers a pathway around one of Windows’ core protections. Here’s what you must know—including code, references, and how it could be exploited.*
What is CVE-2024-26189?
CVE-2024-26189 is a security flaw found in Microsoft Windows’ Secure Boot process. Secure Boot is designed to ensure your PC boots using only trusted software from the device manufacturer. This CVE means attackers can bypass this security and run their own code during boot, potentially taking full control of the device before Windows even loads.
Microsoft’s Advisory:
- Microsoft Security Update Guide – CVE-2024-26189
How Does the Bypass Work?
Attackers can exploit improperly validated Secure Boot policies or images. By introducing a malicious bootloader or exploiting fallback mechanisms, they can load unsigned or tampered code. This essentially disables Secure Boot protections without tripping expected alarms.
Step-by-Step: Attack Scenario
1. Attacker gets local/Admin access:
Deploys a crafted boot policy or bootloader:
Attacker replaces or inserts a crafted bootmgfw.efi file, which exploits the vulnerability in Secure Boot validation.
System boots attacker’s code:
The machine starts up the malicious code, believing it is legitimate—now attacker controls the system before Windows starts.
Example Exploit (Simulated PoC)
Disclaimer: For educational purposes only. Do not use this on unauthorized systems.
Suppose an attacker has access to a Windows system (via physical access or admin privileges)
# Simulate replacing the bootloader on EFI partition
# Mount EFI partition (usually has a mountpoint like Z:)
mountvol Z: /S
# Backup original bootloader
copy Z:\EFI\Microsoft\Boot\bootmgfw.efi Z:\EFI\Microsoft\Boot\bootmgfw.efi.bak
# Replace with a malicious bootloader
copy malicious_bootmgfw.efi Z:\EFI\Microsoft\Boot\bootmgfw.efi
# Unmount the EFI partition
mountvol Z: /D
# On next reboot, compromised bootloader is executed
A successful exploit requires the malicious bootmgfw.efi file. Details for crafting such files depend on the specific technical details, but proof-of-concept code and tactics have circulated privately in researcher communities.
Install Microsoft’s Patch:
Microsoft has released an official fix. Update via Windows Update or your organization’s patch workflow.
Since exploitation needs local admin or physical access, lock down accounts and physical security.
- Scan UEFI/EFI Partitions:
Use tools like [Microsoft Defender] or Chipsec to check for tampered bootloaders.
Technical References
- Microsoft Security Update: CVE-2024-26189
- National Vulnerability Database (NVD) entry
- Overview of Secure Boot
Conclusion
CVE-2024-26189 shows that even foundational security technologies like Secure Boot can have significant gaps. If not patched, attackers with local access can totally bypass Secure Boot and take control—even before Windows starts. The risk is high for enterprises, admins, and anyone running unpatched systems.
Patch now, restrict access, and stay vigilant.
For security researchers:
Dig into Microsoft’s documentation and advisories for the latest technical updates. If you think your system’s UEFI has been tampered with, consult Microsoft’s guidance on Secure Boot recovery.
Timeline
Published on: 04/09/2024 17:15:37 UTC
Last modified on: 04/10/2024 13:24:00 UTC