*Published: 2024-06-14*
Microsoft software is everywhere in the business world—making any new vulnerability in their products a big deal. In early 2024, security researchers and Microsoft disclosed CVE-2024-26214, a serious remote code execution (RCE) vulnerability in the Microsoft WDAC SQL Server ODBC Driver. If you’re running SQL Server databases or using applications that connect through ODBC, this affects you.
Let’s break it down in a way anyone can understand: what’s the risk, what’s exploitable, and how could someone actually launch an attack?
What is CVE-2024-26214?
CVE-2024-26214 is a vulnerability found in the way the Microsoft WDAC SQL Server ODBC Driver processes specially crafted network packets sent to it. If an attacker successfully exploits this bug, they can execute their own code on the server—potentially getting complete control.
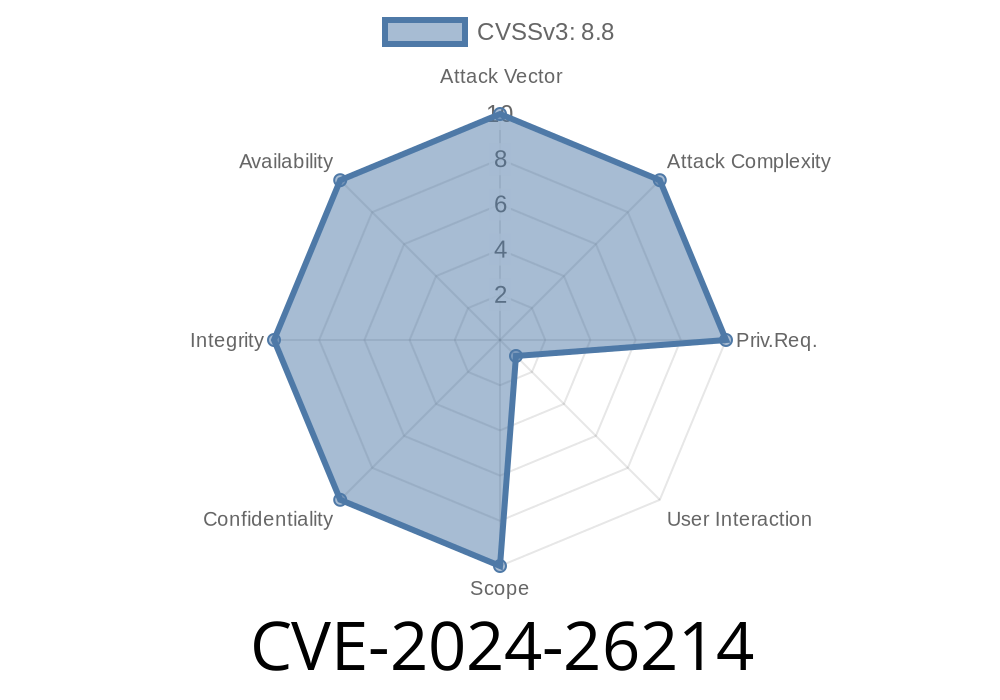
Security Impact:
Microsoft ODBC Driver 18 for SQL Server (before 18.3.2)
- Windows platforms with WDAC/SQL Server modules enabled
Reference:
- Microsoft Security Update Guide: CVE-2024-26214
- CERTIF Blog
How Does It Work?
The vulnerability is caused by improper input validation in the ODBC driver. When the ODBC driver parses certain fields sent from a remote connection—especially in authentication or data exchange—it does not correctly check the boundaries or format. That can lead an attacker to send a 'malicious payload' (a specially crafted packet or query) that triggers memory corruption, often allowing them to run arbitrary code.
Simple Example Scenario:
Example Exploit Code
Below is a simplified proof-of-concept (PoC) showing how a network connection might exploit this flaw by sending malicious data to the ODBC port (usually TCP 1433). This is a basic illustration; real-world exploits will be more complex.
import socket
target_host = '192.168.1.100' # Replace with actual server IP
target_port = 1433 # Default SQL Server port
exploit_payload = b'\x12' * 512 # Fuzzed data (for demonstration)
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect((target_host, target_port))
s.sendall(exploit_payload)
# On vulnerable systems, this data could trigger the bug
response = s.recv(1024)
print(f"Received: {response}")
Warning:
This code is for educational purposes only—do not use it against systems without explicit permission. Running such PoC code against production infrastructure is illegal and unethical!
Initial access: Attacker gets network access to a SQL Server ODBC port.
- Craft packet: They build a data packet that causes a buffer overflow or memory corruption in the ODBC driver.
- Achieve execution: By carefully crafting input, the attacker can control where and how the server jumps in memory (e.g., execute a reverse shell).
- Persistence: With code execution, attacker can deploy malware, escalate privileges, or move laterally inside the network.
Mitigation and Patching
Microsoft’s Official Patch:
Microsoft has issued updates fixing this vulnerability.
Update your ODBC Drivers:
- ODBC Driver 17 download
- ODBC Driver 18 download
Original References
- Microsoft Security Guide - CVE-2024-26214
- NVD CVE Entry
- SQL Server ODBC Driver home
- CERT/CC Vulnerability Note VU#815946
In summary
CVE-2024-26214 is a high-severity vulnerability that could let attackers remotely run code on your Microsoft SQL Servers—just by sending crafted connection packets. The patch is available, and it’s critical to update as soon as possible to protect your servers. Never underestimate the risk: ODBC vulnerabilities often become a favorite target of ransomware crews and APTs alike.
Always stay updated and audit your network regularly!
If you want more in-depth details or help patching your systems, check out Microsoft's guide here.
Timeline
Published on: 04/09/2024 17:15:40 UTC
Last modified on: 04/10/2024 13:24:00 UTC