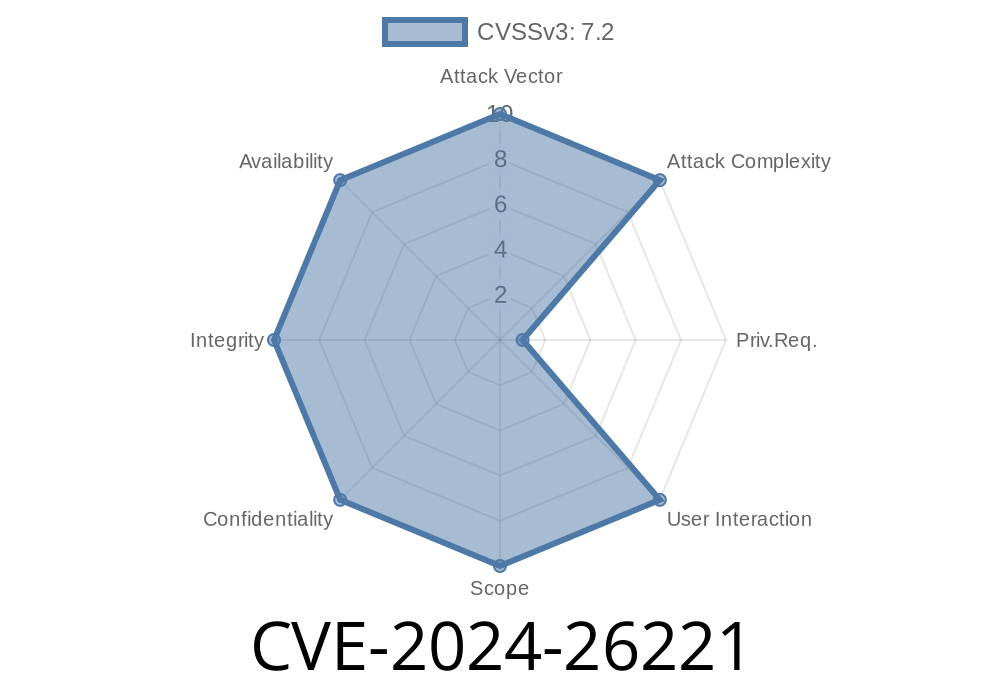
In early 2024, the cybersecurity community identified and reported CVE-2024-26221, a critical Remote Code Execution (RCE) vulnerability in Microsoft’s Windows DNS Server. This flaw allowed attackers to run malicious code on vulnerable servers—opening doors for ransomware, lateral network movement, and potentially widespread damage. Let’s break down what this CVE means, how the exploitation works, and how you can protect your systems, using plain English and real-world samples.
What is CVE-2024-26221?
CVE-2024-26221 is a vulnerability found specifically in the Windows DNS Server component, which is commonly used in enterprise environments to manage and resolve domain names. By exploiting this bug, attackers can execute arbitrary code with SYSTEM privileges by sending crafted queries to the DNS server.
How Does the Vulnerability Work?
At its core, the bug is caused by improper handling of certain requests sent to the DNS server. If an attacker sends a specially crafted query, the DNS service can be tricked into executing code supplied by the attacker. This is often due to issues like buffer overflow or unchecked memory access.
Malicious code is executed—often as SYSTEM.
Here’s a simplified code snippet showing how an attacker could send a malicious DNS request (for illustrative purposes):
import socket
dns_server = '10.10.10.10' # Target DNS server
dns_port = 53
# This payload should exploit the vulnerability; for example, causing an overflow
malicious_dns_query = b'\xab\xcd\x01\x00\x00\x01\x00\x00\x00\x00\x00\x00' # DNS header
# Fuzz the payload: real exploit code would customize this
malicious_dns_query += b'A' * 500 # Overly large payload causing buffer overflow
client = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
client.sendto(malicious_dns_query, (dns_server, dns_port))
print("Malicious DNS query sent.")
*Note: This is a demonstration only—not an actual working exploit.*
Proof-of-Concept Exploit
Security researchers have shared proof-of-concept (PoC) code and write-ups—responsibly, after Microsoft patched the bug. While no reliable public exploit is available as of writing, exploit chains generally involve sending large or malformed "Name" or "Query" requests, leveraging functions inside dns.exe that fail to properly check input lengths or content.
Step-by-Step on an Exploit (Generalized)
1. Craft DNS Name Field: Build a query with an overly long name section (e.g., more than 255 bytes).
2. Exploit Buffer Limits: The vulnerable DNS Server routine copies unchecked data into a stack or heap buffer.
Hijack Execution Flow: The attacker’s data overwrites a return address or function pointer.
4. Shellcode Execution: When the server returns from the function, it jumps to the attacker’s payload.
Real-World Impact
- Wormable Scenario: One infected server could target others in the same network, making this a “wormable” vulnerability similar to the old SIGRed bug (CVE-202-135).
- Privilege Level: Code runs as LOCAL SYSTEM, giving attackers full control over the server and network.
- Known Exploits: As of June 2024, no confirmed wild attacks, but exploit scripts are being traded in underground forums.
1. Apply Security Updates
Microsoft addressed this bug in March 2024. Update your servers immediately.
- Microsoft Security Advisory: CVE-2024-26221 on MSRC
- Patch Tuesday Release: March 2024 Patch Guide
2. Restrict Network Access
Allow remote DNS queries only from trusted networks.
- Block TCP/UDP port 53 at the firewall for all untrusted sources.
3. Logging and Monitoring
Enable logging of DNS server activity; monitor for unusual or malformed DNS queries.
4. Disable Unnecessary Roles
If you don’t need DNS services on a Windows server, disable the DNS Server role.
References and Resources
- CVE-2024-26221 — NIST National Vulnerability Database
- Microsoft MSRC Official Advisory
- Windows DNS Server Threats (Blog)
- Understanding DNS Security Risks
Final Thoughts
CVE-2024-26221 is another reminder of the risk posed by core network services like DNS—especially in Microsoft environments. By patching promptly and monitoring services closely, you can protect your network from attackers eager to exploit these critical flaws.
Stay safe, update your servers, and follow best security practices!
*This article is for educational and defensive security purposes. Do not attempt unauthorized testing or exploitation.*
Timeline
Published on: 04/09/2024 17:15:41 UTC
Last modified on: 04/10/2024 13:24:00 UTC