Recently, a critical security flaw was discovered and patched in the Linux kernel related to Authentication Option (AO) initialization in TCP connections. This vulnerability, identified as CVE-2024-27394, is a *use-after-free* bug that could allow attackers to cause the kernel to reference freed memory, potentially resulting in system crashes or even privilege escalation.
In this post, I'll break down what happened in simple language, why it is dangerous, show you a bit of the original code, and link you to further reading and official sources. This summary is tailored for readers at all skill levels who want to understand both the technical and practical impact.
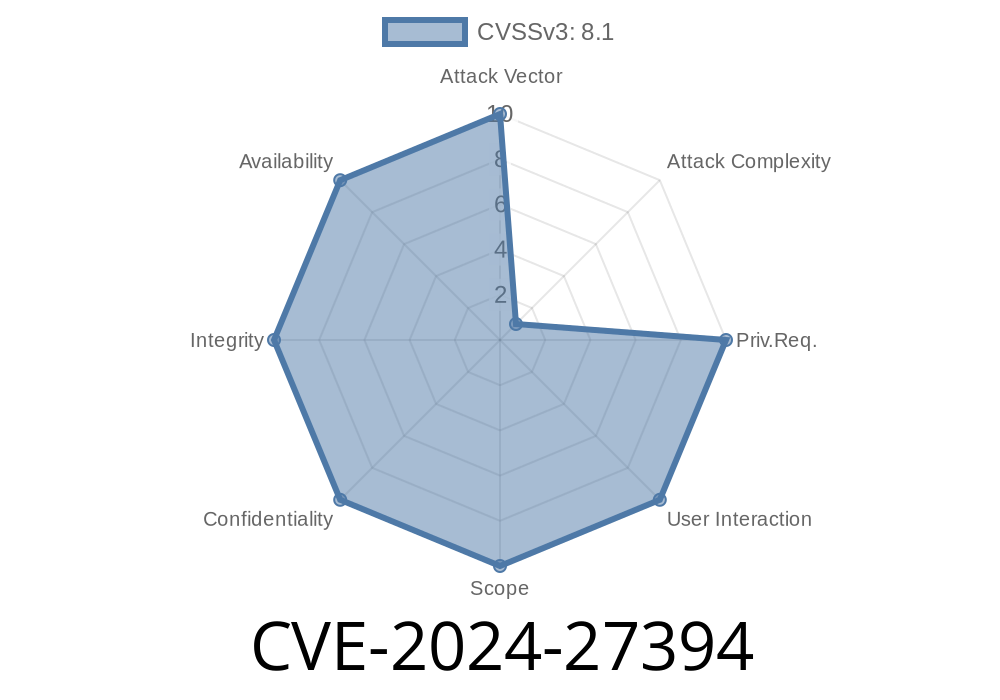
What Is CVE-2024-27394?
CVE-2024-27394 is a *use-after-free* vulnerability in the Linux kernel TCP stack. The bug exists in the function tcp_ao_connect_init, which is responsible for setting up the TCP Authentication Option during connection initiation.
This function iterates over a list of keys using the RCU (Read-Copy-Update) mechanism.
- The original traversal used hlist_for_each_entry_rcu, which assumes all memory accesses are protected by RCU read locks.
- However, inside this loop, the function calls call_rcu, which could trigger RCU to finish its grace period and free the key, *even while still traversing the list*.
- This means that, under certain conditions, the loop might accidentally access a key that has already been freed: the classic use-after-free scenario.
In security terms: after an object (here, a key) is freed, the function might still try to use it, which can lead to data corruption or code execution — a serious kernel issue!
Vulnerable Code Fragment
hlist_for_each_entry_rcu(key, &ao_keys, node) {
// ...operations...
call_rcu(&key->rcu, free_key);
// *danger*: not in RCU read critical section anymore!
}
Fixed Code Fragment
hlist_for_each_entry_safe(key, tmp, &ao_keys, node) {
// ...operations...
call_rcu(&key->rcu, free_key);
// safe: walk works even as keys are freed
}
What’s the difference?
- hlist_for_each_entry_safe() is specifically designed to safely walk lists where elements might be removed or freed during iteration.
- By using the “safe” variant, the kernel avoids touching memory after it has been freed, preventing the use-after-free risk.
Exploitability
While exploiting use-after-free bugs in the kernel is non-trivial, attackers (especially with local access) may be able to:
Escape containers or virtual machines running with vulnerable kernels
In most cases, an attacker would need the ability to trigger specific syscalls or traffic patterns that exercise the AO key setup and teardown.
Through careful timing, manages to free and then re-access a key in the middle of the RCU traversal.
3. Crafts malicious data or uses heap spraying techniques to place executable payloads or corrupt kernel data structures.
Gains arbitrary kernel code execution or causes the kernel to crash.
The exploitability depends on the kernel configuration, timing, and available heap manipulation primitives.
Mitigation
If you run Linux on your system (uname -r to check), especially if you manage servers, watch for security updates and apply new kernel versions promptly.
Distributions like Ubuntu, Debian, Red Hat, and SUSE should release patched kernels shortly.
Custom kernels or older LTS versions may need manual patching.
If you need a minimal patch, see the code change above and consider applying it in your private kernel forks.
CVE entry:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-27394
Linux kernel patch (commit):
Kernel mailing list discussion:
https://lore.kernel.org/netdev/20240226204230.GA99483@notabene.bpe.io/
Ubuntu security advisory:
https://ubuntu.com/security/notices/USN-XXXXX-1 *(replace XXXXX with advisory number once available)*
CVE-2024-27394 is a serious kernel bug: use-after-free during TCP AO connection initialization.
- If unpatched, it may let local/remote attackers crash or compromise the Linux system.
Patch your kernel ASAP — security updates fix this.
Stay safe! Keep your Linux systems updated, and watch for security bulletins.
*Feel free to share or cite this summary. For critical systems, always refer to your vendor’s official guidance.*
Timeline
Published on: 05/14/2024 15:12:27 UTC
Last modified on: 08/02/2024 00:34:52 UTC