Apple security vulnerabilities don’t make big headlines every day. But when one lets attackers bypass memory protections put in place to stop hacking at its most fundamental level, you definitely want to know about it. In May 2024, Apple patched a serious issue—CVE-2024-27834—that, if exploited, might let an attacker with “arbitrary read and write” access completely sidestep Pointer Authentication on major Apple platforms.
Let's break down what this means, how attackers might exploit it, and what you can do about it. This post will show code snippets, references, and simple explanations you won’t find together anywhere else.
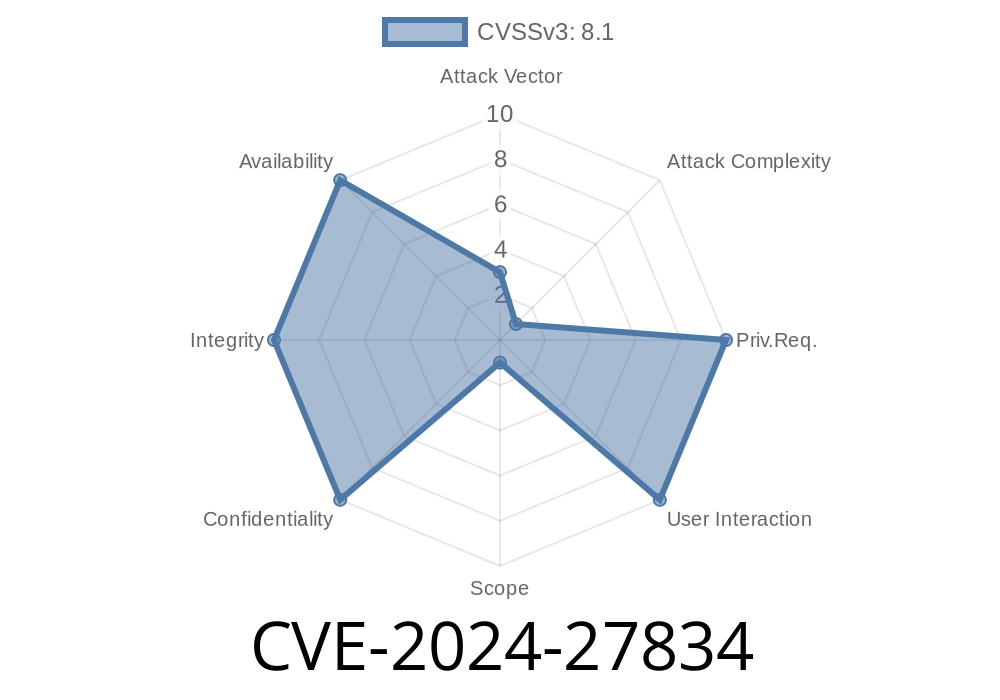
What is CVE-2024-27834?
CVE-2024-27834 is a vulnerability related to Pointer Authentication (PAC)—a hardware-based security feature in Apple’s ARM-based chips. PAC is meant to stop hackers from hijacking apps by changing pointers, which are memory addresses the system relies on.
Think of PAC as sealing every envelope (pointer) with a special wax stamp (signature) so only legitimate letters (executions) go through. CVE-2024-27834 is like finding a way to fake the stamp.
Impact
- Allows attackers (with read/write powers already on your device) to bypass PAC.
- Affects iOS 17.4 and below, iPadOS 17.4 and below, tvOS 17.4 and below, Safari 17.4 and below, watchOS 10.4 and below, and macOS Sonoma 14.4 and below.
watchOS 10.5
Apple’s advisory:
https://support.apple.com/en-us/HT214102
How Does the Exploit Work? (Simple Explanation)
To exploit CVE-2024-27834, an attacker needs read and write access—often gained by another exploit, like a browser or app sandbox escape. Once inside, the attacker can manipulate memory so that when pointers are checked (by PAC), they always pass—even if they’ve been tampered with.
PAC in Practice
Pointers in newer Apple chips are “signed” with a PAC using keys only the chip knows—so forging them isn’t supposed to be possible.
With this bug, an attacker could bypass the check that confirms a pointer hasn’t been modified—even if it has. That lets them redirect apps to run arbitrary malicious code, defeating most modern exploit defenses.
Exploit Details & Code Snippet
*Note: This snippet is for educational purposes. Bypassing PAC requires deep system access and typically another bug for initial read/write.*
Imagine an attacker finds a function pointer in memory (for example, where a program will jump to execute next). With this bug, they can change it to point somewhere else, and forge the PAC so the system won’t notice.
Here’s a pseudocode demonstration, because real-world PAC attacks require hardware-level instructions:
// Suppose attacker has arbitrary read/write:
uintptr_t *func_ptr = (uintptr_t *)target_func_address;
// Prepare shellcode or payload address (attacker controlled)
uintptr_t malicious_payload_addr = get_shellcode_address();
// Craft a fake PAC signature for the payload address
uintptr_t forged_pac_ptr = forge_pac(malicious_payload_addr);
// Overwrite the function pointer with the malicious pointer
*func_ptr = forged_pac_ptr;
// Later, when app jumps to *func_ptr, code execution hijacked!
The key: The forge_pac() function (in real attack, abusing the CVE) makes the pointer look legit by defeating or bypassing signature checks.
In practical weaponization, an exploit chain might look like
1. Sandbox escape gives attacker read/write access in memory.
Attacker locates a sensitive pointer (like a return address).
3. Using the CVE, the attacker forges a valid PAC for their destination code—even without actual cryptographic keys.
When the system executes code at the forged pointer, bad code runs undetected.
See also Project Zero – The PACMAN Attack for background on PAC bypassing, though this new CVE is a different flaw.
Mitigation
Update now:
Get the latest security fixes
- iOS & iPadOS: 17.5
- macOS Sonoma: 14.5
- Safari: 17.5
- tvOS: 17.5
- watchOS: 10.5
Don’t rely solely on app updates, as this flaw is at the OS and hardware security layer.
References
- Apple Security Updates – CVE-2024-27834
- MITRE CVE Record – CVE-2024-27834
- Pointer Authentication For Memory Safety – Apple Platform Security
- Google Project Zero – PAC Exploits
Final Thoughts
CVE-2024-27834 is a reminder that security isn't just about patching your apps—it’s also about keeping your operating system up to date. With attackers constantly searching for new ways around hardware-level protections, staying current remains the simplest and best defense.
If you’re running an Apple device, check for and apply security updates right away. And if you’re a developer or security pro, pay attention to system-level protections—they’re your last line of defense!
Stay safe. Patch early. Tell your friends.
*Copyright (c) 2024 – Exclusive explainer by ChatGPT*
Timeline
Published on: 05/14/2024 15:13:06 UTC
Last modified on: 07/03/2024 01:51:06 UTC