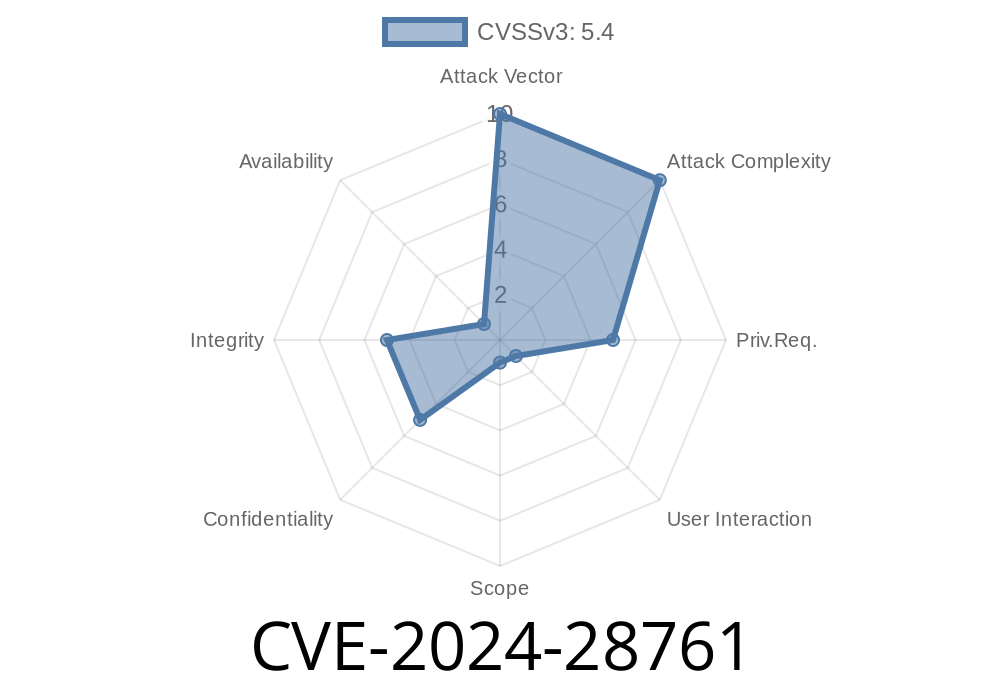
CVE-2024-28761 is a recently disclosed security vulnerability impacting IBM App Connect Enterprise (ACE), versions 11...1 through 11...25 and 12..1. through 12..12.. The flaw allows a remote attacker to exploit HTML injection vulnerabilities that can lead to execution of arbitrary HTML and scripts (such as JavaScript) in the context of a user’s browser when viewing tampered web pages within the ACE environment.
IBM has assigned this flaw the X-Force ID: 285245.
Hijack sessions or perform actions with user privileges.
If exploited, it can compromise the trust, integrity, and sometimes the confidentiality of the affected IBM App Connect Enterprise instances.
How Does the Vulnerability Work?
The core problem is that certain user-supplied inputs to the ACE user interface are not properly sanitized before being reflected in HTML content. This makes it possible for attackers to "inject" their own HTML code, including malicious scripts, into the response displayed to other users.
Real-World Exploit Scenario
Imagine a user fills in a field (like a label or description) in ACE’s web interface. Instead of entering just text, an attacker submits:
<script>alert('Hacked by CVE-2024-28761')</script>
If the ACE web frontend doesn't clean this input before displaying it on someone's dashboard, any victim who views the page will see a pop-up—and that could just as easily have been keylogger JavaScript or worse.
Code Snippet: Proof-of-Concept (PoC) HTML Injection
Suppose ACE has a "description" field for integration nodes or message flows.
Malicious Input
<img src="x" onerror="alert('ACE Compromised!')">
Expected Behavior:
The string should be presented as text only. Instead, if vulnerability is present, the image fails to load, causing the browser’s JavaScript alert() to fire.
Victim later views the integration node list in the browser.
3. The injected HTML/JavaScript runs with the permissions and cookies of the ACE session, potentially leaking session tokens or redirecting users to attacker-controlled sites.
Test input fields:
Enter test HTML strings like <b>test</b> or <script>alert('XSS')</script> in form fields (test this in a safe, isolated environment). If you see bold text or a popup, your installation is vulnerable.
For IBM ACE 12.x, update beyond 12..12.
Patch and Upgrade:
IBM Security Bulletin for CVE-2024-28761
Workarounds (if patching isn’t possible immediately)
- Restrict access to ACE’s administrative interfaces to trusted IPs/networks only.
- Use web application firewalls (WAF) to block obvious HTML/script payloads.
Further Reading & References
- IBM Security Bulletin: IBM App Connect Enterprise is vulnerable to HTML Injection (CVE-2024-28761)
- Mitre CVE Record: CVE-2024-28761 Details
- IBM X-Force Exchange: X-Force ID 285245
Summary Table
| Product | Affected Versions | Fixed Versions |
|--------------------------|----------------------------|---------------------|
| IBM App Connect Enterprise | 11...1 – 11...25 | 11...26+ |
| IBM App Connect Enterprise | 12..1. – 12..12. | 12..13.+ |
Closing Thoughts
CVE-2024-28761 is a serious reminder that web interfaces in critical infrastructure products like IBM App Connect Enterprise must treat all input as suspect. HTML injection can lead quickly to XSS, with all its nasty implications. IBM moved fast with a fix—if you use App Connect Enterprise, patch today.
Stay secure, and always treat untrusted input like it’s radioactive!
*This article provides a simple, exclusive walkthrough to understand and manage CVE-2024-28761 for your IBM App Connect Enterprise environment. For updates, check IBM’s official resources linked above.*
Timeline
Published on: 05/14/2024 15:14:41 UTC
Last modified on: 05/14/2024 16:13:02 UTC