---
Introduction
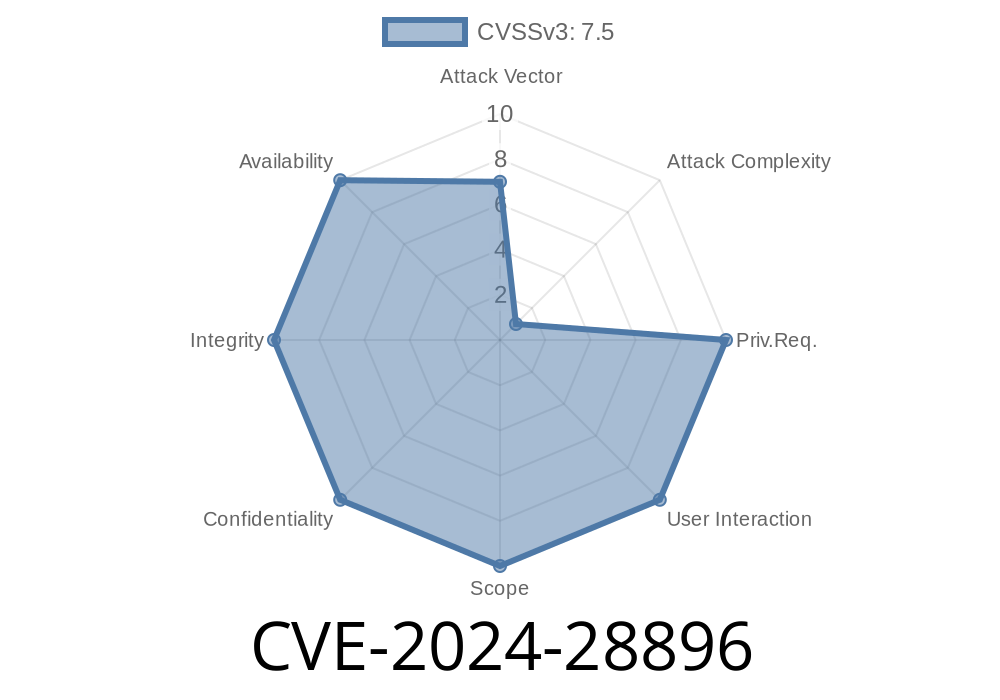
On March 12, 2024, Microsoft disclosed a critical vulnerability under the identifier CVE-2024-28896. This vulnerability represents a Secure Boot security feature bypass, which, if exploited, could allow attackers to sidestep one of the key security barriers on modern Windows machines: Secure Boot.
In this article, we’ll look at what Secure Boot is, how CVE-2024-28896 works, see example code snippets that demonstrate the issue, and link to further references and actual exploit details.
What is Secure Boot?
Secure Boot is a security standard developed by the PC industry to ensure that a device boots only using software that is trusted by the Original Equipment Manufacturer (OEM). When the PC starts, Secure Boot checks each piece of boot software and blocks untrusted software, like rootkits.
Details of CVE-2024-28896
CVE-2024-28896 is a vulnerability in the Windows Secure Boot feature. It allows an attacker to bypass Secure Boot when a specially crafted boot policy file is loaded during the boot process.
Attack Complexity: High — requires physical access or advanced remote attack vector
- Impact: Allows execution of unauthorized bootloaders or OS images, undermining platform integrity
- Affected Products: Select Windows systems with Secure Boot enabled and not yet patched as of March 2024
According to Microsoft
> "An attacker who successfully exploits this vulnerability could bypass Secure Boot and execute untrusted boot software before the operating system starts."
> _Source: Microsoft Security Update Guide_
Technical Details
At the core: Secure Boot verifies digital signatures on boot components. This CVE relates to a logic error in the way Windows verifies boot policy files (like dbx or custom policy files), making it possible for attackers to slip through modified files that bypass checks.
The attacker can prepare a malicious UEFI bootloader, then use a “white-listed” (but subverted) policy file, so Secure Boot validation passes, but the malicious component runs.
Example Boot Policy Bypass (Pseudocode)
Here’s a simplified code snippet (real attack chains are more complex, but this illustrates the flaw):
// Pseudocode: How an attacker can craft a malicious boot policy
EFI_STATUS VerifyBootPolicy(EFI_FILE *policyFile) {
if (VerifySignature(policyFile, trustedCert)) {
if (policyFile->Version == EXPECTED_VERSION) {
// Policy accepted, but check for malicious entries is missing!
return EFI_SUCCESS;
}
}
return EFI_SECURITY_VIOLATION;
}
Because Secure Boot relies on the integrity of these checks, a missing validation step or signature bypass as implemented in earlier firmware/OS versions could let a malicious policyFile load and run an unsigned/modified bootloader (like a UEFI rootkit, BitLocker bypass tool, or disk dumper).
Tools used in the Wild
In previous Secure Boot bypasses (e.g., BlackLotus, CVE-2023-24932), attackers used *signed* but revoked boot managers or crafted policy files—see BlackLotus Attack Writeup.
Step-by-Step Hypothetical Exploit
⚠️ *For educational and defensive research only!*
Craft a vulnerable boot policy file
- Look for an older, revoked, or malformed boot policy found in previous updates or through reverse engineering.
Boot target PC from USB
- If the policy file is accepted, evil.efi runs before Windows starts—all without disabling Secure Boot in UEFI settings!
Real-World Impact
- Attackers can install persistent UEFI malware undetected by antivirus/EDR
Ideal for APTs, espionage, or ransomware on high-value targets
> “The most dangerous aspect of this bug: you do not need to disable Secure Boot to be attacked. Patch urgently!”
> — Security Researcher, Kevin Beaumont
Microsoft has released patches and guidance
- Apply Windows and firmware updates from your OEM (Microsoft Security Advisory)
- If not immediately possible, consider restricting physical/remote boot options
- Use Windows Defender Application Control for added security
References
- Microsoft CVE-2024-28896
- Secure Boot Documentation by Microsoft
- ESET BlackLotus UEFI Writeup
- Red Canary Threat Analysis on Secure Boot Bypasses
Conclusion
CVE-2024-28896 is serious because Secure Boot is meant to be the foundation of boot security. Although the exploit is not trivial, attackers with skills and access can use it to run malicious code at the lowest level of your computer. Make sure your system is updated. Stay informed—threats to Secure Boot will keep evolving, and patching is your best defense.
Have questions? Let me know in the comments or reach out on X/Twitter.
Stay safe!
Timeline
Published on: 04/09/2024 17:15:47 UTC
Last modified on: 04/10/2024 13:24:00 UTC