Published June 2024
*by CyberSec Insights*
What Is CVE-2024-28908?
CVE-2024-28908 is a critical security vulnerability in the Microsoft OLE DB Driver for SQL Server. If exploited, it allows a remote, unauthenticated attacker to execute arbitrary code on the target system. This can lead to a full system compromise, loss of sensitive data, or further attacks across your network.
Released as part of Microsoft’s June 2024 Patch Tuesday, this vulnerability affects many organizations using SQL Server in enterprise environments and cloud databases.
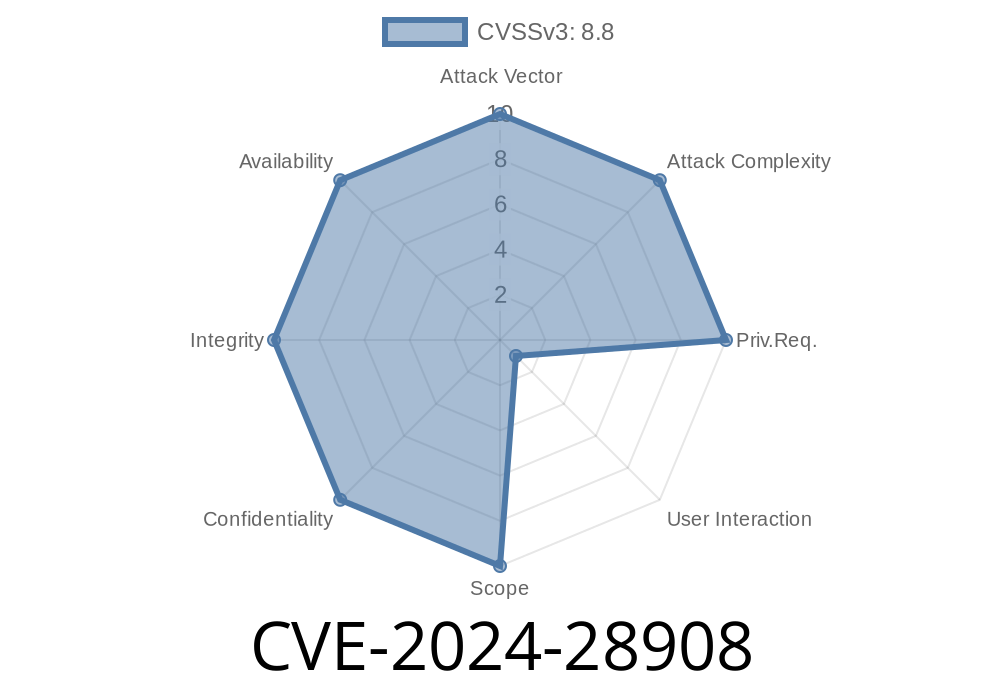
Severity: Critical
CVSS Score: 8.8 (High)
Understanding the Vulnerability
Microsoft OLE DB Driver for SQL Server is a key component used by applications to connect and interact with Microsoft SQL Server databases.
The vulnerability exists due to improper validation of user-supplied data when the OLE DB Driver processes a specially crafted connection request. If an attacker can trigger this flaw—typically by luring a victim into connecting to a malicious SQL Server instance—they could slip in malicious payloads that the driver runs with the privileges of the affected application.
Example Attack Scenario
Let's say you have a Windows application using the vulnerable OLE DB driver to connect to a database. If the application is tricked into connecting to a rogue server, it could allow attackers to run code on your machine without your knowledge.
# Simplified Python example (using pyodbc as illustration)
import pyodbc
# Attacker controls the malicious SQL Server
connection_string = 'Provider=MSOLEDBSQL;Data Source=attacker_server;User Id=sa;Password=malicious_pass;'
try:
con = pyodbc.connect(connection_string)
cursor = con.cursor()
cursor.execute('SELECT * FROM sensitive_table')
for row in cursor:
print(row)
except Exception as e:
print("Error:", e)
*Note: Microsoft OLE DB Driver would be used directly in production .NET or C++ code, but the example above demonstrates the core issue—connecting to an unknown server.*
If the malicious “attacker_server” replies with crafted bytes that exploit CVE-2024-28908, the local system could now be running malware, backdoors, or system commands.
Technical Flow
Although Microsoft has not released full exploit code, the advisory and security community described the bug as a memory corruption issue triggered by malformed TDS (Tabular Data Stream) responses from the SQL server.
Windows Command Line Example
Attackers might set up a fake SQL server using tools like impacket or Metasploit’s MSSQL server module to push out malicious packets. Once an application or user connects to the attacker’s server, exploitation can occur.
Here’s a proof-of-concept-like workflow (pseudocode)
Attacker:
1. Spins up fake SQL Server on public server.
2. Crafts TDS response exploiting CVE-2024-28908 buffer overflow.
Victim:
1. Opens custom application with:
- Connection string to "malicious.example.com"
2. Application’s OLE DB client processes crafted server response.
3. Exploit triggers RCE; attacker gains shell or runs commands.
A real exploit would require deep knowledge of the TDS protocol and specifics of memory layout in the OLE DB driver, but weaponized code may surface soon, so proactive defense is critical.
Patch Immediately
Microsoft has released a security update that should be applied to all affected systems.
References
- Microsoft Security Update Guide – CVE-2024-28908
- Microsoft OLE DB Driver for SQL Server Official Docs
- Impacket Toolkit – For Building Custom Network Exploits
- MSRC Blog – June 2024 Patch Tuesday
Final Thoughts
CVE-2024-28908 is a serious reminder that database connection drivers are an attractive target for attackers. If you let users or applications connect to untrusted SQL servers, you may be exposing your systems to remote code execution.
Always patch promptly, monitor your environments, and train users to avoid connecting to unknown resources. Don’t wait for public exploits—secure your SQL infrastructure today.
*Stay safe, patch fast, and keep learning! — The CyberSec Insights Team*
Timeline
Published on: 04/09/2024 17:15:49 UTC
Last modified on: 04/10/2024 13:24:00 UTC