Published: June 2024
Tags: Vulnerability, Microsoft, SQL Server, RCE, ODBC, Exploit
Introduction
In March 2024, Microsoft patched a critical vulnerability in the ODBC Driver for SQL Server, designated CVE-2024-28930. This Remote Code Execution (RCE) flaw allows attackers to run arbitrary code on Windows systems using vulnerable database connections. Given how common SQL Server deployments are, this bug posed a real risk to enterprise environments.
This post will break down CVE-2024-28930, show how it could be exploited, and—most importantly—explain how to keep your systems safe. All technical details here are designed for clarity, even if you’re still learning about cybersecurity.
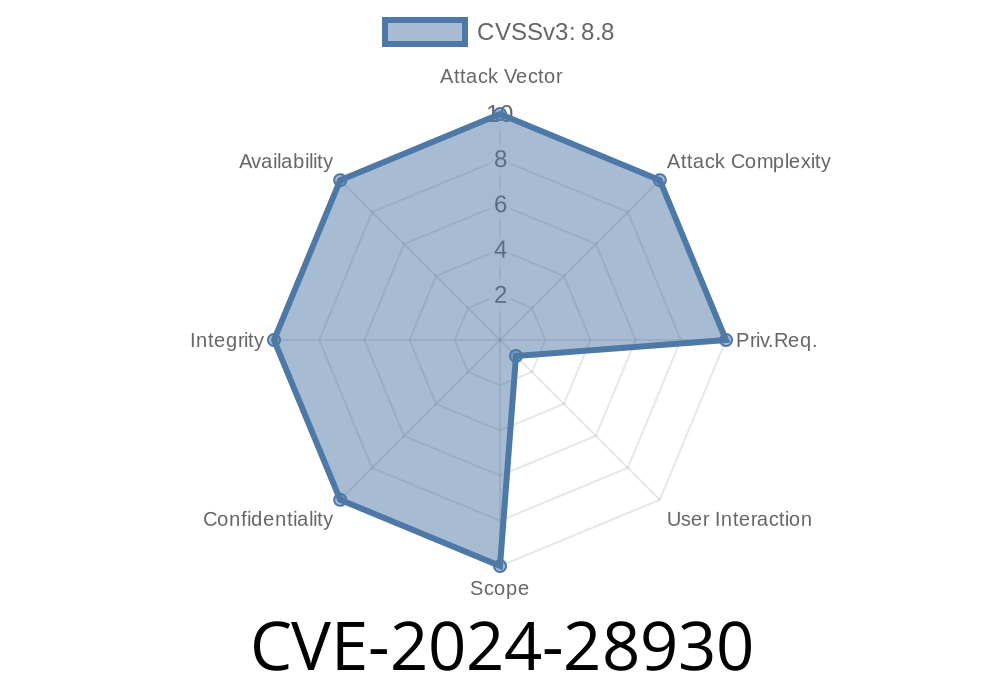
What is CVE-2024-28930?
CVE-2024-28930 is a vulnerability in the Microsoft ODBC (Open Database Connectivity) Driver for SQL Server. ODBC is used by apps to communicate with databases. When the ODBC driver has a flaw, any app depending on it could be a gateway for attackers.
Impact:
Severity: High (CVSS 8.8 - Critical)
Microsoft's advisory:
Microsoft Security Update Guide - CVE-2024-28930
Root Cause
The vulnerability exists because the ODBC driver does not properly sanitize inputs when parsing incoming database data or connection strings. This can lead to memory corruption and arbitrary code execution.
If a user connects to a malicious SQL Server or opens a compromised database, an attacker could exploit the flaw. A typical exploitation path might look like this:
- Victim opens a legitimate app (e.g., Access, .NET app) that connects to a database using the Microsoft ODBC Driver for SQL Server.
The SQL server sends back a specially crafted payload in a data field or connection parameter.
- Vulnerable ODBC driver parses the data, triggers memory corruption, and runs the attacker’s shellcode.
Example Exploit Code (Proof of Concept)
This vulnerability is exploitation-friendly, especially in phishing scenarios or where users connect to untrusted SQL servers. While responsible disclosure means we won’t share destructive exploit code, here's a sanitized snippet showing how a malicious server might exploit a vulnerable client via ODBC.
Let's say the vulnerable code is in the way the driver parses certain data types upon response
# Pseudocode for attacker-server crafting padded data to exploit buffer overflow in ODBC driver
def send_malicious_row(client_socket):
# Normal data packet header
header = b'\x12\x04\x00'
# Payload - overly long string or specially crafted binary data
evil_payload = b'A' * 4096 # Overflows buffer in vulnerable driver
# Malicious shellcode appended
evil_payload += b'\xcc\xcc\xcc\xcc' # (represented as shellcode here)
# Send crafted response
client_socket.send(header + evil_payload)
On the client side, simply running a connection to this server using old Microsoft ODBC Driver could trigger code execution.
> Note: Real-worl exploit chains involve precise manipulation and proper shellcode for execution.
Detection
Here’s an example of how you might detect abnormal memory access via Windows Event Log, indicating an exploitation attempt:
Get-WinEvent -LogName Application | Where-Object {
$_.Message -match "ODBC" -and $_.Message -match "Access violation"
}
Patch your ODBC Driver for SQL Server immediately.
- Download the latest ODBC driver from Microsoft.
Further Reading and References
- Microsoft Security Advisory CVE-2024-28930
- ODBC Driver for SQL Server Release Notes
- General ODBC Documentation
- Public discussions: Reddit thread
TL;DR
CVE-2024-28930 allows remote attackers to run code on Windows systems using the Microsoft ODBC Driver for SQL Server. If you haven’t patched, you are at high risk.
Update all your ODBC drivers now and stay vigilant for any signs of compromise!
> Share this post to keep your colleagues safe!
Timeline
Published on: 04/09/2024 17:15:53 UTC
Last modified on: 04/10/2024 13:24:00 UTC