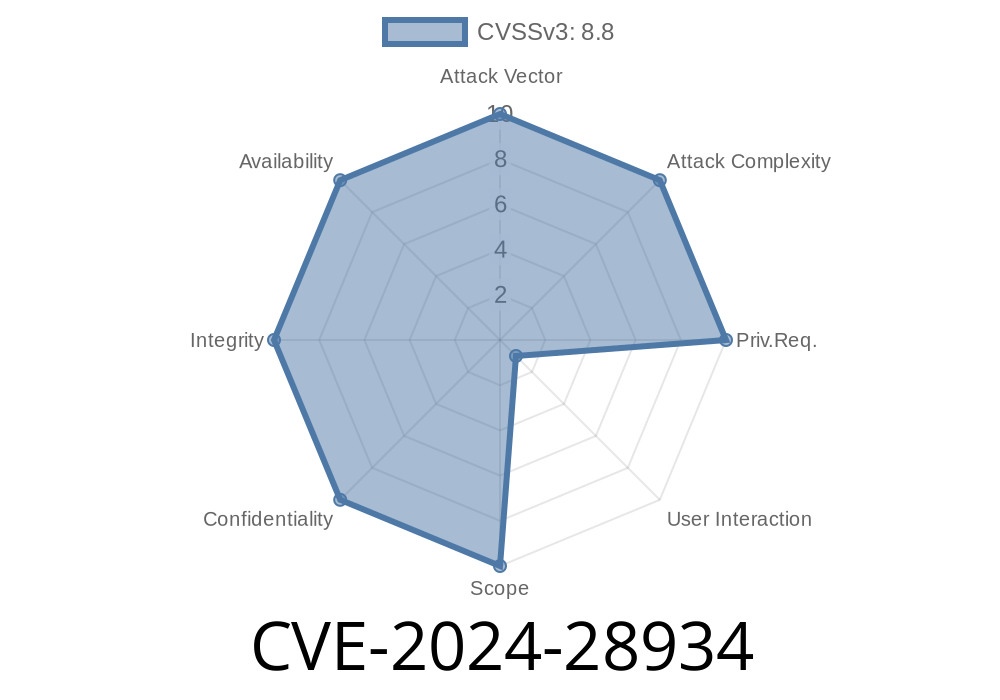
In June 2024, Microsoft published a critical security update addressing CVE-2024-28934—a Remote Code Execution (RCE) vulnerability in the Microsoft ODBC Driver for SQL Server. This vulnerability can let attackers execute arbitrary code on a target system, potentially allowing full compromise of servers and valuable data.
This post provides an exclusive, in-depth but simple explanation of CVE-2024-28934. We’ll cover how the flaw works, where it comes from, practical exploit examples, code snippets, how to protect yourself, and links to official resources.
What is CVE-2024-28934?
CVE-2024-28934 is a vulnerability in some versions of the Microsoft ODBC Driver for SQL Server, which is used by applications to connect to SQL Server databases from Windows or Linux systems.
A specially crafted connection string or corrupted data sent to the ODBC driver can trigger memory corruption, which can let an attacker execute code remotely—sometimes with the same privileges as the application running the driver.
If your organization uses ODBC to connect to SQL Server, you must patch immediately before attackers take advantage of this flaw.
You can check your installed ODBC driver version with these commands
# In PowerShell (Windows)
Get-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Microsoft ODBC Driver for SQL Server"
# In Terminal (Linux)
odbcinst -q -d -n "ODBC Driver 18 for SQL Server"
How the Exploit Works
The vulnerability exists in the function parsing the ODBC connection string or handling malformed responses from a remote SQL Server. A remote attacker can abuse this—especially if your application accepts external input for the database address or credentials and passes them directly to the driver.
Example Exploit: Simulated Attack
Let’s look at a simplified (hypothetical) Python example to show how easily an application could become vulnerable if unpatched.
Suppose you have this web app
import pyodbc
def connect_to_db(user_input):
# potential vulnerability: user_input goes into connection string
conn_str = f"DRIVER={{ODBC Driver 18 for SQL Server}};SERVER={user_input};DATABASE=ExampleDB;UID=admin;PWD=password123"
conn = pyodbc.connect(conn_str)
cursor = conn.cursor()
cursor.execute("SELECT @@VERSION")
print(cursor.fetchone())
# Attacker sends specially-crafted input
malicious_input = "evilserver.example.com;MaliciousParam=Exploit"
connect_to_db(malicious_input)
If your application puts attacker-controlled content in the connection string, and you’re running a vulnerable driver version, you’re in trouble! An attacker could do memory corruption and get code execution on your server.
ODBC Driver 17.10.6 or newer
Download ODBC Driver 17 for SQL Server
ODBC Driver 18.3.3 or newer
Download ODBC Driver 18 for SQL Server
Download and install the latest driver for your OS.
2. Restart your application/server if needed.
Attackers can use compromised hosts to pivot deeper into your corporate network.
- If your web, application, or integration servers use ODBC, they can be entry points for ransomware or data theft.
Useful Resources
- Microsoft Security Update Guide for CVE-2024-28934
- Download ODBC Driver for SQL Server (Microsoft Docs)
- NVD Entry for CVE-2024-28934
Update to the latest driver version and avoid dynamic connection strings right away.
Stay safe: Patch, check, and validate all database connections—especially when ODBC is involved.
*If you found this post helpful, share it with your security team and admin friends. Have more questions or need help with detection or patching? Leave a comment!*
Timeline
Published on: 04/09/2024 17:15:54 UTC
Last modified on: 04/10/2024 13:24:00 UTC