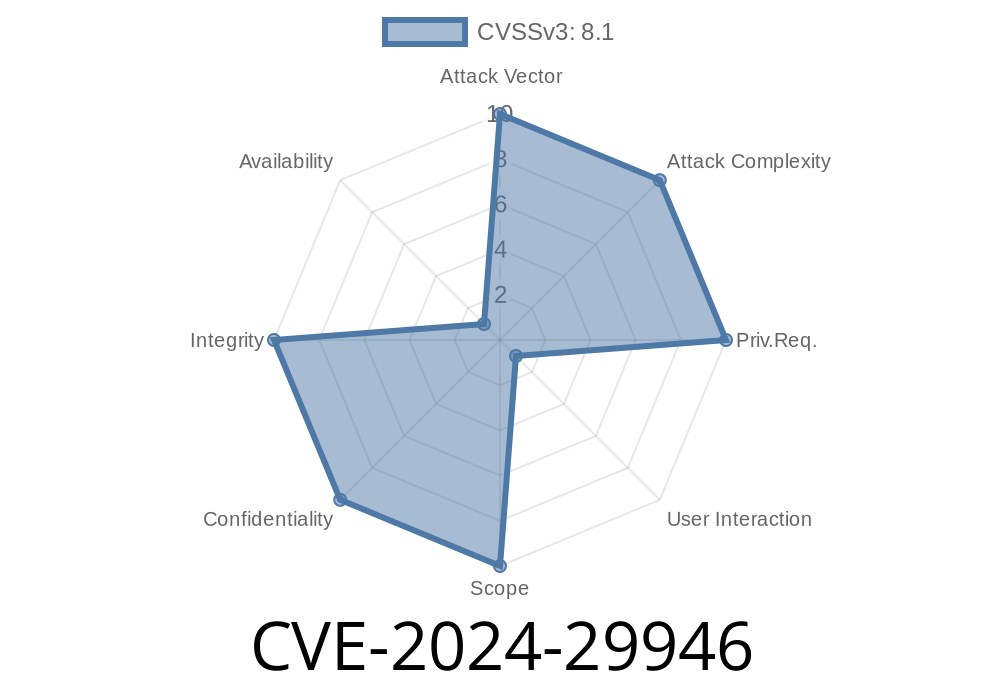
In the ever-evolving world of cybersecurity, even enterprise giants like Splunk sometimes face headline-worthy vulnerabilities. Enter CVE-2024-29946—a recently patched bug that could have let attackers run dangerous SPL commands right under your nose, just by getting an unsuspecting user to click the wrong link.
9..9
The issue? The Dashboard Examples Hub (a feature that shows off dashboard functionalities) failed to restrict certain risky Search Processing Language (SPL) commands. Normally, these commands are tightly controlled—imagine "delete" or "rest," which could irreparably change or leak your logging data. However, within the Examples Hub, an attacker could slip those forbidden SPLs right past Splunk’s usual checks.
How Does the Attack Work?
To succeed, an attacker would have to phish a victim. In basic terms: trick someone with Splunk access into clicking a cleverly crafted link, or otherwise making a request in their browser session. If the victim is logged in and has the Dashboard Examples app enabled, the risky SPL runs with their permissions.
Suppose a malicious actor crafts a special URL pointing to the Examples Hub, embedding an SPL like
| delete from main where source="critical_logs"
This SPL is typically blocked in dashboards. But thanks to CVE-2024-29946, the Examples Hub doesn’t enforce the same guardrails. If a logged-in user activates the link, Splunk executes the SPL as if the user typed it themselves.
Let’s see how the exploit might look in practice. An attacker could send an email like this
<a href="https://splunk-enterprise.example.com/en-US/app/launcher/dashboard_examples?search=%7Cdelete%20from%20main">Check out this cool dashboard!</a>
If the victim has Splunk open and is authorized, clicking this executes the risky SPL.
*Important: The actual mechanics may vary based on how the Examples Hub parses and executes SPL parameters, but this demonstrates the general risk.*
Splunk Security Advisory:
NVD Entry:
Splunk Release Notes:
Splunk Enterprise Release Notes
Why Is This a Big Deal?
- Risky SPL Exposure: Commands that delete events, access REST endpoints, or export data could be run by a regular user, with zero extra privileges for the attacker.
Upgrade ASAP:
Get your Splunk Enterprise up to 9.2.1, 9.1.4, or 9..9 immediately. This closes the hole for good.
User Education:
Remind users not to click untrusted links, especially if they’re already logged into sensitive systems.
Conclusion
CVE-2024-29946 is a reminder that even non-core features like example hubs can be weak spots. Attackers love these overlooked entry points—your defenses should cover them, too. Patch regularly, stay alert for phishing, and keep a close watch on sensitive features in your environment.
Stay safe, and spread the word—vigilance beats vulnerability every time.
Timeline
Published on: 03/27/2024 17:15:54 UTC
Last modified on: 04/10/2024 01:15:18 UTC