---
In June 2024, Microsoft patched a critical security vulnerability—CVE-2024-30009—that affects the Windows Routing and Remote Access Service (RRAS). This flaw could let attackers remotely execute code with elevated permissions on vulnerable Windows servers. In this post, I’ll break down exactly what this vulnerability is, how attackers might exploit it, and how you can test for and protect against it. I’ll include code samples and link out to the best official resources.
What is Windows RRAS?
Windows Routing and Remote Access Service (RRAS) is a Microsoft feature that allows a Windows server to act as a network router or VPN server. Many organizations use RRAS to let remote employees connect to company resources securely.
Unfortunately, RRAS is a complex service and often runs with high privileges, which means vulnerabilities can have a huge impact.
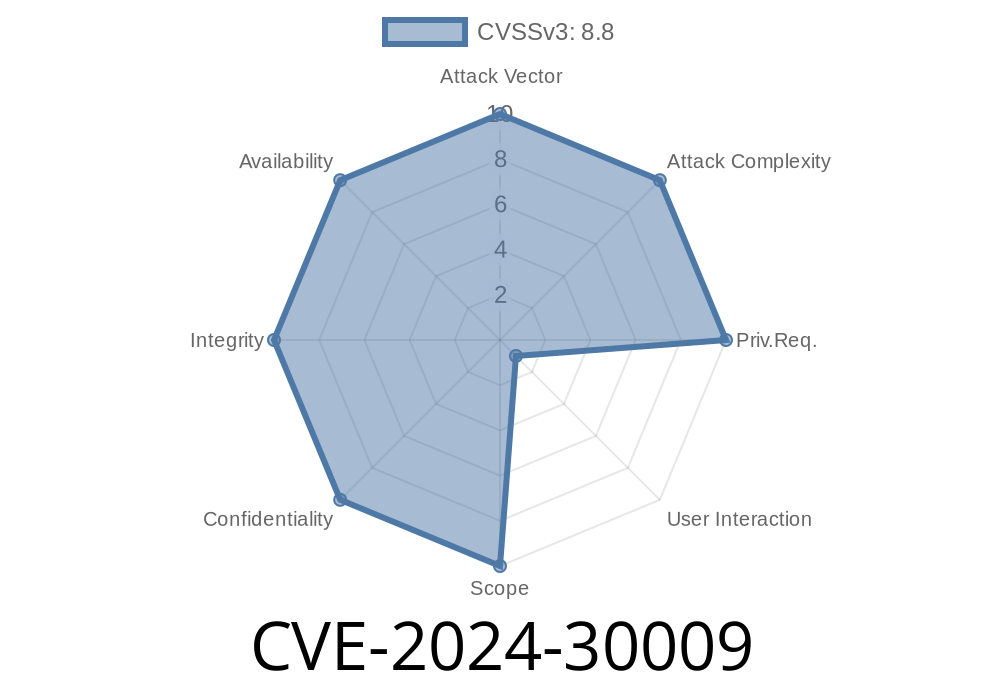
What is CVE-2024-30009?
- Disclosure: June 2024 Patch Tuesday (Microsoft Advisory)
Impacted Systems: Windows Server 2012, 2016, 2019, 2022 (with RRAS role enabled)
This vulnerability allows a remote attacker to send specially crafted packets to a server with RRAS enabled. If successful, the attacker can run arbitrary code with SYSTEM privileges, which is the highest level of access on Windows.
RRAS must be installed and enabled.
- Firewall ports for RRAS/VPN (e.g., 500/UDP, 450/UDP, 1723/TCP) are typically open.
The vulnerability resides in the way RRAS handles certain network packets. Microsoft states
> “Successful exploitation of this vulnerability could allow a remote authenticated attacker to execute arbitrary code on the target server.”
This statement suggests attackers need some level of authentication, such as valid VPN credentials, but *not necessarily* high privileges.
Security researchers (such as ZDI's advisory) suggest the vulnerability is a memory corruption issue triggered by malformed network traffic. Attackers can achieve remote code execution if they can control enough of the input.
Proof of Concept Snippet
Below is a Python PoC template. It won’t exploit the server directly but demonstrates how an attacker might connect to an RRAS VPN endpoint and send unexpected/invalid authentication packets, potentially triggering the flaw.
import socket
# RRAS typically listens on UDP port 500 (IKE) or TCP/1723 (PPTP)
TARGET_IP = "192..2.100"
TARGET_PORT = 1723 # PPTP
# Malformed PPTP control message (simple example, not a live exploit)
malicious_packet = b"\x00" * 64 # Overly large or malformed buffer
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((TARGET_IP, TARGET_PORT))
s.sendall(malicious_packet)
response = s.recv(1024)
print("Response:", response)
s.close()
Note: This code will not crash a server or cause RCE on its own. It is for educational demonstration ONLY.
Prepare: Find a RRAS server exposed to the Internet (often port 1723 or 500).
2. Authenticate: Log in with valid VPN credentials (these could be stolen, brute-forced, or default passwords).
Result: Full remote control of the Windows server.
No public exploit is available (as of this writing), but organizations like the Zero Day Initiative have confirmed that exploitation is feasible.
Patch Immediately!
Apply the latest Microsoft security updates from June 2024. (Direct link to MSRC)
References and Further Reading
- Microsoft official advisory for CVE-2024-30009
- Zero Day Initiative ZDI-24-XXXX Blog
- Sophos Writeup (CVE-2024-30009)
Final Thoughts
If your organization relies on Windows RRAS, patch immediately and review your VPN exposure to the internet. RRAS has been a source of serious bugs over the years, and CVE-2024-30009 underscores the risk of exposing critical infrastructure services. As always, test updates in a lab, monitor for suspicious activity, and keep your security posture vigilant.
*This post was written in plain language to help sysadmins and defenders understand the risk posed by CVE-2024-30009. If you’re a penetration tester or blue teamer, use this knowledge to help make your organization safer—not for malicious purposes.*
Timeline
Published on: 05/14/2024 17:16:39 UTC
Last modified on: 06/19/2024 20:58:27 UTC