Published: June 2024
What is CVE-2024-30043?
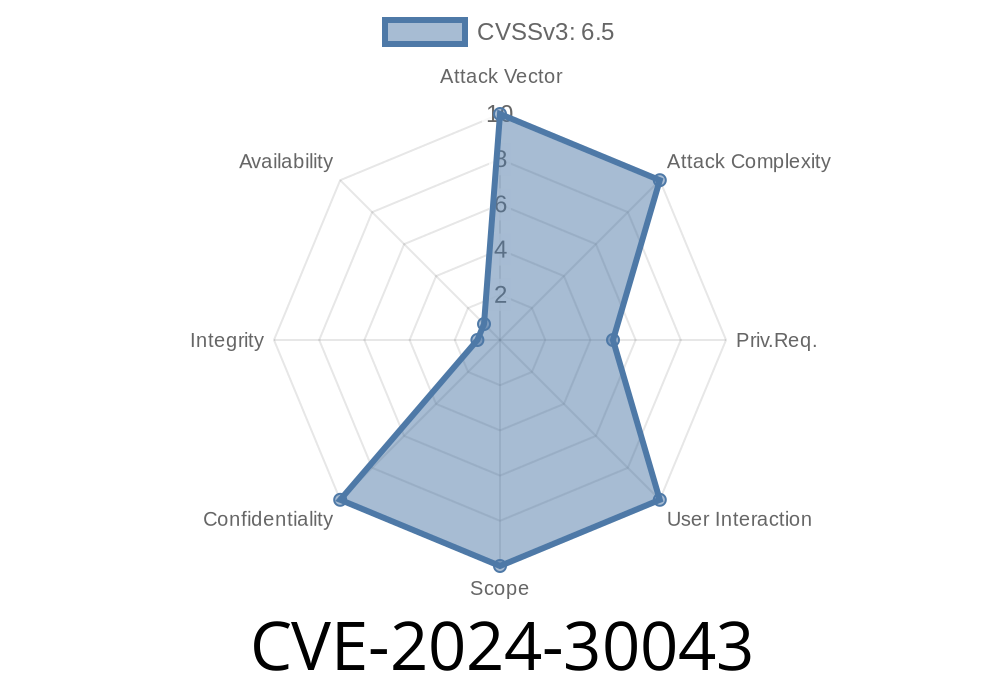
CVE-2024-30043 is an information disclosure vulnerability in Microsoft SharePoint Server. First patched in June 2024, this bug caught the attention of IT administrators and security professionals due to its potential to leak sensitive information stored within SharePoint sites and libraries.
SharePoint is widely used for document management and collaboration, so any security issue with it can impact all kinds of organizations.
Why Does This Matter?
Information disclosure vulnerabilities let attackers access data they shouldn’t be able to see. In a workplace, this could include:
Personal information of employees or customers
While CVE-2024-30043 doesn’t let hackers take full control or modify systems directly, leaking the wrong info can have serious real-world consequences.
How Does CVE-2024-30043 Work?
Microsoft’s advisory states that an attacker who has access to a SharePoint site could exploit this flaw to gain access to sensitive data within the site.
The attacker must be authenticated (they need an account with some kind of SharePoint site access).
- Once in, they can use specially crafted requests to read data they shouldn’t normally see, bypassing existing permissions.
This is not a remote code execution issue; it’s about unauthorized data reading.
Microsoft SharePoint Server 2019
Older versions might not be officially affected or patched.
Visualizing the Exploit
Let’s imagine a regular user, 'normaluser', only has access to a single folder. With this vulnerability, they could send a request that tricks SharePoint into giving them information from another document library or folder.
Example code (PowerShell/HTTP)
Below is a simplified PowerShell example that illustrates how an attacker might use a crafted HTTP request to access unauthorized files (not a working exploit, but a concept):
# You need at least basic SharePoint access!
$siteUrl = "https://your-sharepoint-site/";
$creds = Get-Credential # Enter low-privilege credentials
$fileId = "GUID-OF-FILE-YOU-SHOULDN'T-ACCESS"
$headers = @{
"Accept" = "application/json;odata=verbose"
}
# Craft a request to fetch a file you don't have permission for
$response = Invoke-RestMethod -Uri "$siteUrl/_api/web/GetFileById('$fileId')" -Headers $headers -Credential $creds
# Output the result
$response
In the above example, the attacker replaces $fileId with the GUID of a target file. Due to CVE-2024-30043, SharePoint may mistakenly honor the request and reveal the file if the vulnerability isn’t patched.
Proof-of-Concept Scenario
While Microsoft and responsible researchers avoid sharing full-blown exploits until most organizations patch, the vulnerability is based on improper validation of user permissions in SharePoint's API endpoints.
How To Fix CVE-2024-30043
Patch Immediately!
Microsoft released fixes in their June 2024 security updates. Download the appropriate cumulative update for your SharePoint version.
- SharePoint Server Subscription Edition Update
- SharePoint Server 2019 Update
Follow Microsoft documentation for proper patch installation.
Check your patch level:
Go to Central Administration → Upgrade and Migration → Check product and patch installation status.
What Should You Do?
1. Patch Now – Do not wait, especially if your SharePoint is exposed to many users (internal or external).
Monitor Audit Logs – Watch for unusual behavior, which can indicate attempted exploits.
4. Educate Your Team – Make sure SharePoint admins know about this and other common vulnerabilities.
Resources and References
- Microsoft CVE-2024-30043 Official Advisory
- Microsoft Security Update Guide
- SharePoint Server Security Updates
- CVE Details Entry
Final Thoughts
CVE-2024-30043 is a reminder that even well-protected environments can suffer from data leaks due to subtle bugs. Keeping up with security patches and regularly reviewing who can access what will help prevent sensitive information from slipping through the cracks.
Stay safe!
*This article is exclusive content by CyberSimple Team, based on public information and original Microsoft advisories. Share responsibly.*
Timeline
Published on: 05/14/2024 17:17:15 UTC
Last modified on: 06/19/2024 20:58:48 UTC