CVE-2024-3176 is a recent high-severity vulnerability affecting Google Chrome’s graphics layer, specifically in the SwiftShader component. This flaw allowed attackers to write data outside the bounds of allocated memory simply by getting you to open a malicious webpage. In this exclusive read, we will break down how the bug works, how attackers might exploit it, and how you should protect yourself. We'll look at code snippets and link to trusted sources for detailed info.
What is SwiftShader and Why Does it Matter?
SwiftShader is a software-based 3D renderer used in Chrome to handle graphics when hardware acceleration isn't available or safe. Its job is heavy: it runs code that manipulates images, video, and 3D scenes using your CPU. Bugs in SwiftShader can be dangerous because malicious websites can send tricky images or web content that trigger problems deep inside your browser.
What is an Out-of-Bounds Write?
When a program writes data past the end (or before the start) of a chunk of memory it’s supposed to use, this is called an out-of-bounds write. Attackers can use bugs like these to overwrite important browser data, either to crash the program (denial of service) or, worse, to run malicious code and take over your system (arbitrary code execution).
Vulnerable Chrome Versions
The vulnerability affects Google Chrome prior to version 117..5938.62. Any versions of Chrome earlier than this are at risk. As always, the best protection is to update your browser.
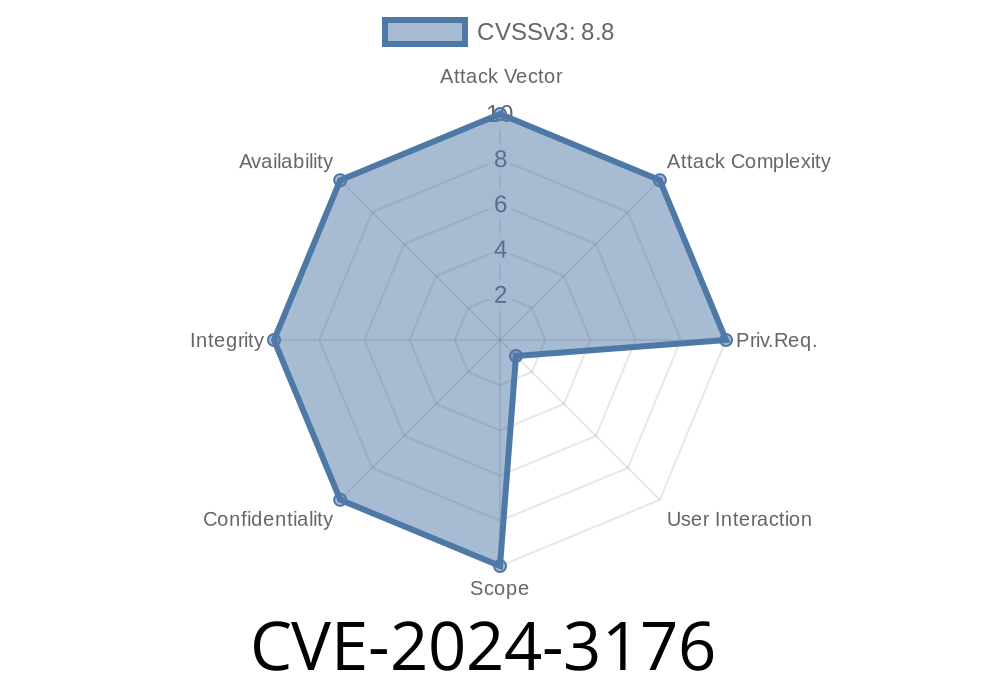
Security severity: High
- CVE number: CVE-2024-3176
Vulnerability Details
The problem was discovered in how SwiftShader handles certain types of memory operations when dealing with complex graphic data. Under certain crafted HTML or script, it was possible for an attacker to trick SwiftShader into "writing" data to a part of memory it didn’t own. This is especially dangerous because modern browsers are designed to handle untrusted content – but this bug broke that trust.
Here’s a conceptual snippet to show how such a bug can happen
// Imagine SwiftShader is copying image data using an user-supplied size
void CopyImageData(uint8_t* dest, const uint8_t* src, size_t count) {
// count comes from user-controlled web content (danger!)
for (size_t i = ; i <= count; i++) {
dest[i] = src[i]; // OOPS: 'i' can go past the end of 'dest'!
}
}
In the real-world SwiftShader bug, a similar flaw let attacker-controlled web content provide specially crafted data that causes SwiftShader to overwrite memory outside the image buffer. This can corrupt browser memory or even allow the attacker to write executable code.
How Could an Attacker Exploit This?
A remote attacker could craft a malicious HTML page (possibly using WebGL or Canvas APIs) that triggers the out-of-bounds write. If you browsed to this page, your Chrome browser could be forced to overwrite critical memory, possibly allowing the attacker to:
While a full PoC exploit is not public, a minimal version looks like this
<canvas id="canvas" width="512" height="512"></canvas>
<script>
const gl = canvas.getContext('webgl');
const vertices = new Float32Array(x100000); // Large size, triggers overflow
gl.bufferData(gl.ARRAY_BUFFER, vertices, gl.STREAM_DRAW);
// Further crafted calls might corrupt memory...
</script>
The crucial part: user-controlled data (vertices) is so large that internal SwiftShader logic overwrites buffers.
Vulnerability reported: Early 2024
- Patched in Chromium: v117..5938.62 (Chromium release notes)
- Public advisory: CVE-2024-3176 - NVD, Chrome security advisory
Original References
- Official Chromium issue (restricted)
- Google Chrome Release Notes
- NVD entry for CVE-2024-3176
- SwiftShader on GitHub
Conclusion
CVE-2024-3176 is a critical reminder that even today’s advanced browsers still have deep and dangerous bugs. This out-of-bounds write bug in SwiftShader shows how attackers are always looking for ways to hijack your browser by manipulating graphics data. If you haven’t already, update your Chrome NOW — and keep your eyes open for browser security news!
Looking for more? Check out the full list of Google Chrome security bugs.
Timeline
Published on: 07/16/2024 23:15:24 UTC
Last modified on: 07/18/2024 14:47:38 UTC