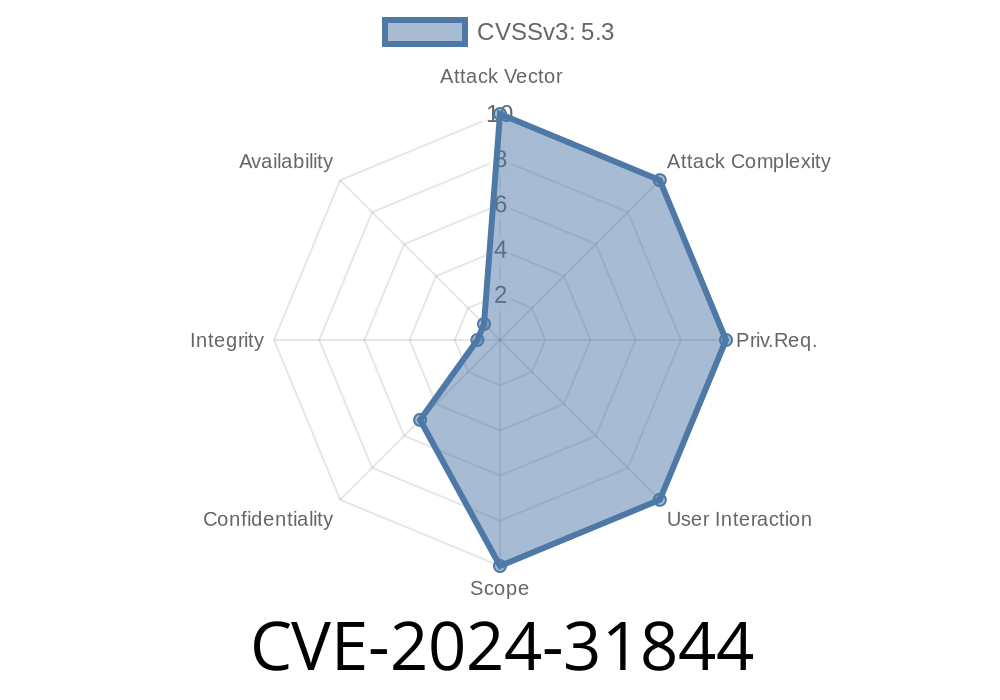
In April 2024, the security community identified a new vulnerability tracked as CVE-2024-31844 that affects Italtel Embrace version 1.6.4. This vulnerability occurs because the server does not properly handle application errors. As a result, unauthenticated attackers can trigger errors and receive responses that leak sensitive internal information, such as absolute filesystem paths.
In this post, we’ll explain what CVE-2024-31844 is, go through how the exploit works, show a simple code snippet, and link to original references. This article is written in plain language for IT staff, security professionals, and interested readers looking to understand this vulnerability at a practical level.
What is CVE-2024-31844?
CVE-2024-31844 is an information disclosure vulnerability found in Italtel Embrace version 1.6.4. The problem is with the way the application handles unexpected errors. If something goes wrong on the server side—like a request for a resource that doesn’t exist or is wrongly formatted—the server replies with error messages that sometimes include the absolute file paths of source code files or other sensitive details.
This leak can provide clues to attackers about the structure of your system, which files are in use, and where to aim other, more dangerous attacks.
How the Exploit Works
The flaw exists because the server doesn't sanitize error messages before sending them back to the user. If an error occurs, an attacker can get a stack trace or detailed message that tells them exactly which file, and the path to that file, had the problem.
If the application expects a JSON object but gets malformed data, it might respond like this
HTTP/1.1 500 Internal Server Error
Content-Type: application/json
{
"error": {
"message": "Unexpected token at line 1",
"file": "/var/www/html/embrace/app/controllers/ApiController.php",
"line": 45
}
}
The attacker now knows
- The server is running Linux/Unix (from the path style)
Example Code Snippet
Let’s look at how an attacker might trigger this bug by sending a purposely malformed API request. We'll use curl, a common command-line tool.
curl -X POST \
-H "Content-Type: application/json" \
-d '{"invalid_json": ' \
http://target-server.com/api/resource
Because the JSON is broken (missing closing }), the server will return an error. If the server is vulnerable, the attacker may see a response like:
{
"error": "Syntax error in /var/www/html/embrace/app/controllers/ApiController.php on line 45"
}
Why Does This Matter?
Absolute paths and internal filenames shouldn’t be revealed publicly. Even if the attacker can’t directly exploit something yet, this information can:
If you’re running Italtel Embrace 1.6.4
- Upgrade to a patched version as soon as possible (check with Italtel support or advisories)
Original References and Further Reading
- NIST NVD Entry for CVE-2024-31844
- Italtel Embrace Product Page
- OWASP Error Handling Cheat Sheet
Conclusion
CVE-2024-31844 is a simple but dangerous example of how even innocent-looking errors can leak valuable clues to hackers. By always sanitizing error messages and keeping software up to date, organizations can protect themselves from information leaks and related attacks.
Timeline
Published on: 05/21/2024 16:15:26 UTC
Last modified on: 07/26/2024 18:21:23 UTC