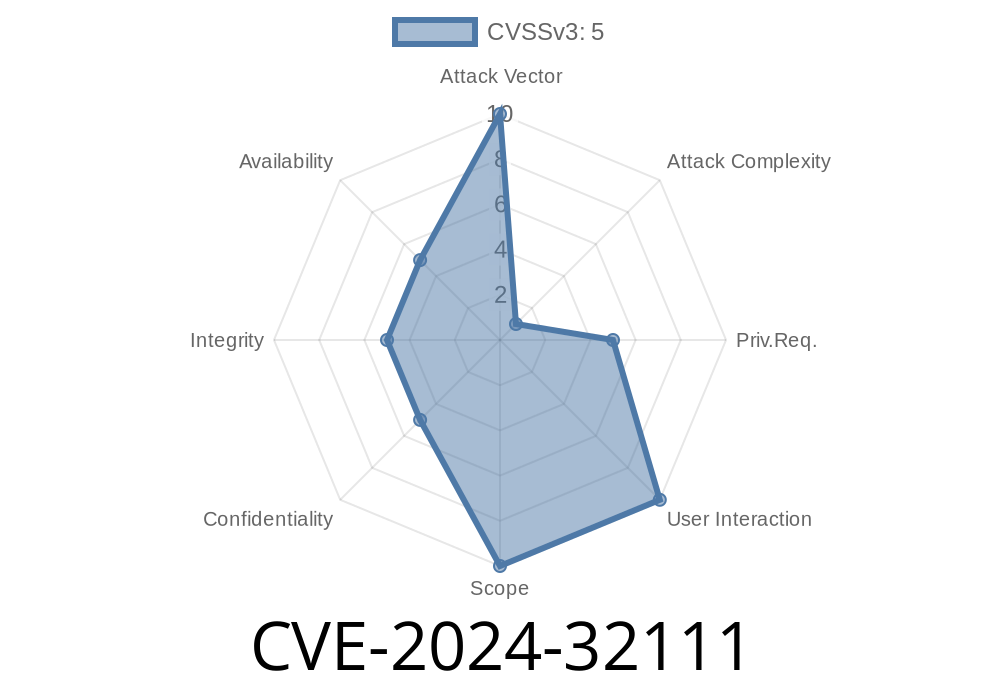
WordPress is the backbone of over 40% of all websites, so any security issue in its core sets off alarm bells for millions of site owners. CVE-2024-32111 is a newly discovered vulnerability in WordPress’s handling of file paths. It lets attackers access files outside allowed directories—a dangerous class of bug called Path Traversal or Directory Traversal.
Affected Versions:
WordPress 4.1 through 6.5.4 (essentially every major version in recent years, see complete list below).
If you run a WordPress site and haven’t updated in June 2024, read on—your site may be at risk right now.
What is Improper Limitation of a Pathname? (‘Path Traversal’)
Path traversal happens when software fails to properly check user input for file and directory paths. It’s often exploited with sequences like ../ (dot-dot-slash), which move “up” in the folder structure.
Imagine a site with a file download feature like this
GET /download.php?file=report.pdf
A malicious visitor could change the file parameter
GET /download.php?file=../../wp-config.php
If the server doesn’t block this, it may reveal wp-config.php—which contains database credentials and other sensitive info.
Official References
- NVD – CVE-2024-32111
- WordPress Security Advisory
The Root Cause: Directory Traversal in User-Controlled Paths
WordPress lets users—especially admins, authors, or even lower-privileged users in some misconfigs—upload, list, or interact with files on the server. A piece of the WordPress core failed to fully block ../ and similar tricks in some file handling functions.
Attackers could use crafted file paths to escape the intended directory, reading arbitrary files on the server (within PHP’s open_basedir or OS permission limits).
Imagine there’s a WordPress endpoint that lets an authenticated user fetch theme files for editing
$file = $_GET['file'] ?? '';
$theme_dir = get_template_directory();
$full_path = $theme_dir . '/' . $file; // unsafe join
if (file_exists($full_path)) {
echo file_get_contents($full_path);
}
Attacker Input
Suppose the attacker sets file=../../wp-config.php, then
$full_path = /var/www/html/wp-content/themes/mytheme/../../wp-config.php
That collapses to /var/www/html/wp-config.php—outside the theme directory!
Realistic Exploit (Proof of Concept)
Given an endpoint like /wp-admin/theme-editor.php?file=../../wp-config.php, an attacker with editing rights (sometimes less) can retrieve the main WordPress config, which may have hardcoded secrets.
Note: WordPress tries to restrict such access, but this bug shows a gap in the checks.
Curl Proof-of-Concept
curl 'https://target.site/wp-admin/theme-editor.php?file=../../wp-config.php'; \
-b "wordpress_logged_in=YOUR_SESSION_COOKIE"
If vulnerable, the request will return the contents of wp-config.php—containing your DB password!
*Replace with your session cookie; unauthenticated attacks are rare but possible if a plugin exposes the path elsewhere.*
What Did WordPress Fix?
A patch checks for traversal patterns like .. and normalizes user input before joining with sensitive paths.
Patched Code Example
$file = $_GET['file'] ?? '';
$file = wp_normalize_path($file);
if (strpos($file, '..') !== false) {
die('Invalid file path');
}
$full_path = $theme_dir . '/' . $file;
if (file_exists($full_path)) {
echo file_get_contents($full_path);
}
Update WordPress core to 6.5.5 (or latest)
Add server-level restrictions
- In nginx.conf or .htaccess, block requests that contain ../
Resources & References
- CVE-2024-32111 NIST Entry
- WordPress Security Updates
- OWASP Path Traversal Definition
Conclusion
CVE-2024-32111 is one of the most serious WordPress core bugs in recent memory, affecting every supported version and some long-outdated ones. The consequences range from leaked database credentials to complete site compromise.
If you run WordPress, update right now!
Stay secure. Share this post with anyone running a WordPress site—digital safety is a team sport.
*Got questions or want help testing your site? Leave a comment below!*
Timeline
Published on: 06/25/2024 14:15:11 UTC
Last modified on: 06/27/2024 19:20:35 UTC