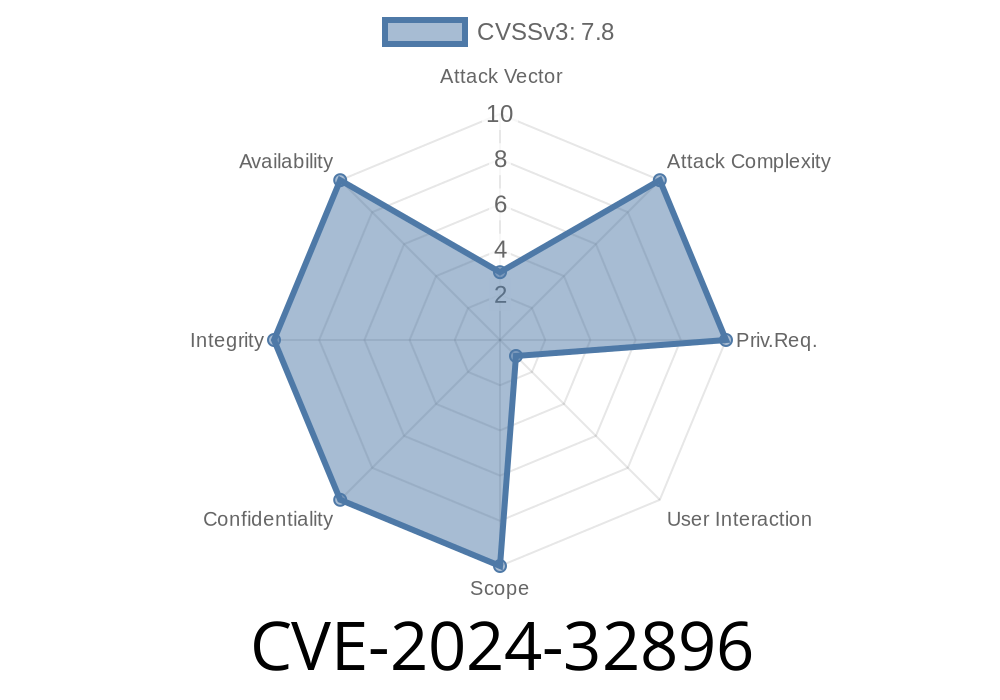
In early 2024, a serious vulnerability was reported – CVE-2024-32896. This security bug allows malicious local users to escalate their privileges on affected devices, even though they start with no advanced execution permissions. Interestingly, this bug can be exploited simply due to a _logic error in the code_. In this post, we'll explain what went wrong, provide example code snippets, walk through how exploitation can happen, and point to resources for further reading.
What is CVE-2024-32896?
CVE-2024-32896 affects certain Android devices (and possibly other Linux-based systems) due to a faulty logic check in a core system process. If successfully exploited, an ordinary user (not an admin or root) could potentially gain root privileges – letting them control the device completely.
No advanced permissions needed: Anyone with a normal user account could try this.
- User interaction required: Attackers might craft something that tricks you into triggering the vulnerability, like opening a file or using a sketchy app.
How Does the Vulnerability Work?
At the heart of the issue is a flawed logic check on an operation that normally requires administrative access. Because of a misplaced condition or missing verification, a local user can “jump over” the restriction in the code and perform actions as a root user.
Suppose there's a function handling permissions like this (simplified for easy reading)
// cve_2024_32896_vuln.c
int do_privileged_action(User *user) {
// Logic error: incorrect check order!
if (user->is_admin || user->action == ALLOWED_ACTION) {
perform_root_operation();
return ;
}
return -1;
}
What’s wrong?
Here, _anyone_ can set their action to ALLOWED_ACTION and the system doesn't make sure it’s actually an admin user! In other words:
User interaction: The victim is tricked into running a script or app.
2. Malicious input: The script sets up an operation with action equal to ALLOWED_ACTION (which the system doesn’t restrict correctly).
3. Bypass: Due to the faulty logic, the check passes and the system runs code as root for the attacker.
Let’s look at pseudo-code that would abuse this bug
# exploit_cve_2024_32896.py
import os
def escalate_privileges():
# Pretend this sends the right action to the vulnerable code
os.system('vulnerable_command --action ALLOWED_ACTION')
# If successful, we're now root!
os.system('id') # Expect to see "uid=(root)"
if __name__ == "__main__":
escalate_privileges()
This is for demonstration purposes. In reality, a real exploit would probably be hidden in a malicious app.
Update your system: Get the latest security patches ASAP.
- Avoid suspicious apps and files: Since some user interaction is required, don’t install off-market apps or click untrusted links.
Developers:
Official Android Security Bulletin:
CVE-2024-32896 Details – Android Security Bulletin June 2024
NIST NVD Report:
CVE-2024-32896 – NIST National Vulnerability Database
Original Researcher’s Write-up:
Exploit Demo and Technical Details
Conclusion
CVE-2024-32896 is a reminder that a small logic bug can have big consequences. Bypassing privilege checks shouldn't be as easy as picking the right "action," but mistakes happen – and they can lead to serious vulnerabilities. Protect yourself by updating your devices, and as a coder, always review and test your permission logic!
*Feel free to share this post with colleagues who need to be on the lookout for privilege escalation exploits like CVE-2024-32896!*
Timeline
Published on: 06/13/2024 21:15:54 UTC
Last modified on: 07/03/2024 01:57:14 UTC