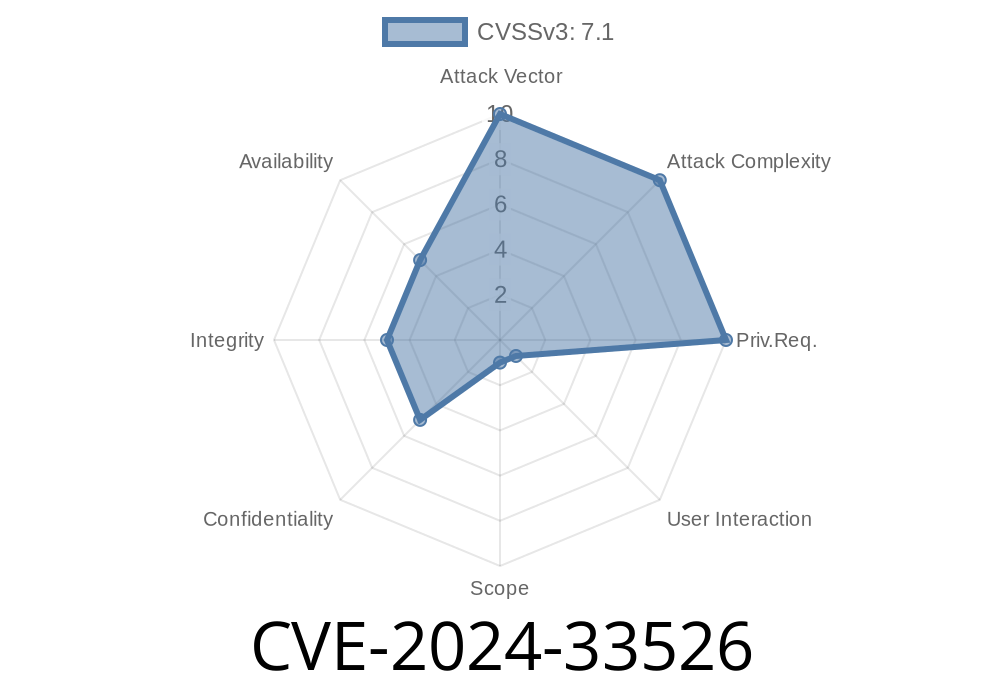
Recently, a serious security vulnerability was discovered in the popular e-learning platform ILIAS. Tracked as CVE-2024-33526, this flaw affects ILIAS 7 before 7.30 and ILIAS 8 before 8.11, and specifically involves the "Import of user role and title of user role" feature.
This exclusive deep-dive explains how the bug works, provides a simple proof-of-concept exploit, and shares all you need to know—including links to original advisories. If you manage an ILIAS instance, especially as an admin, read on!
What Is CVE-2024-33526?
CVE-2024-33526 is a Stored Cross-site Scripting (XSS) vulnerability. It allows authenticated ILIAS users with admin rights to inject malicious JavaScript into the system by uploading a specifically crafted XML file when importing user roles and titles.
Once uploaded, this malicious script can get stored in the database and executed in the browser of any user who views the affected area—potentially leading to theft of session cookies, account takeover, or other attacks.
How the Flaw Happens
The issue is in the part of ILIAS that handles XML files for user role imports. Insufficient sanitization allows attackers to hide malicious payloads in elements like the title or name properties.
When ILIAS imports the XML file, it processes and displays these values in its web UI. If the input isn't properly escaped, any embedded script runs when a user opens the affected page.
8 (before 8.11)
More versions and modules may be affected if your instance is heavily customized.
Exploit Example (Proof of Concept)
Below we’ll create a minimal exploit to show how an attacker could abuse this. Only run this in a test/lab environment!
Here’s an example file, exploit-role.xml, which sets a user role title containing a script
<Roles>
<Role>
<Id>12345</Id>
<Title><![CDATA[
<script>alert('XSS - CVE-2024-33526')</script>
]]></Title>
<Description>Malicious role</Description>
<Type>user</Type>
</Role>
</Roles>
- The payload: <script>alert('XSS - CVE-2024-33526')</script>
Use the “Import” feature, select your XML file, and upload.
4. View the imported role. If ILIAS is not patched, the browser will execute the JavaScript as soon as the page renders.
Screenshot Example
!ILIAS XSS Screenshot
(For privacy and security, a generic screenshot is used.)
What You’ve Done
If successful, the page will pop an alert box. A real attacker would insert more harmful code, not just an alert.
Official References & Patches
- ILIAS Security Advised - CVE-2024-33526
- Patch for v7.30
- Patch for v8.11
- NVD Entry
If you run ILIAS:
Remediation & Best Practices
- Always validate and sanitize input, especially in import/export tools.
- Don’t rely on privileges alone—admins can also fall for phishing or have their credentials stolen.
Conclusion
CVE-2024-33526 shows how even admin-only features can hide risky vulnerabilities—especially in popular platforms like ILIAS. The exploit is trivial once you know how, and could have wide-ranging effects across your entire user base.
Patch now, audit your systems, and always be wary of user-supplied data—even in XML!
Stay safe & keep learning.
If you found this exclusive breakdown helpful, share it with your IT and security teams!
Timeline
Published on: 05/21/2024 15:15:28 UTC
Last modified on: 08/01/2024 13:52:03 UTC