A recent vulnerability, CVE-2024-34123, has been discovered in Adobe Premiere Pro versions 23.6.5, 24.4.1, and earlier. This flaw could let attackers execute arbitrary code on your system if you interact with a malicious file. The root problem is with the way Premiere Pro searches for certain files—attackers can take advantage by placing their own harmful files where Premiere Pro will find and run them before the legit files.
In this article, we’re breaking down how this vulnerability works, how it can be exploited, and what you can do to stay safe. At the end, you’ll find code snippets for demonstration, actual references, and an example scenario.
What Is CVE-2024-34123?
This is what’s called an Untrusted Search Path vulnerability. Basically, when software like Premiere Pro needs to load an extra part (like a DLL or plugin), it doesn’t always check in the safest way. Instead, it just scans certain folders in a specific order and loads the first matching file it finds. If an attacker plants a fake, malicious file in one of those folders, Premiere Pro might run that instead—without you knowing.
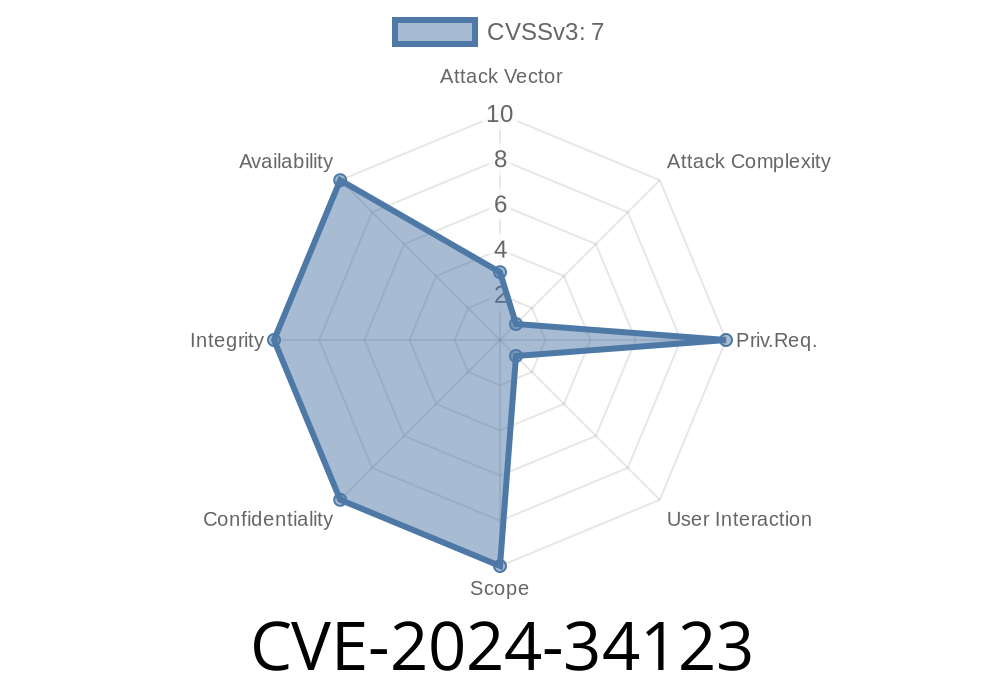
Impact: Code execution with user privileges
- User Interaction Required: Yes (user must open a specially prepared file, or work in a compromised folder)
- Attack Complexity: High (attacker needs to get a malicious file onto a trusted path and have the user interact)
How Does the Attack Work?
Let’s say Premiere Pro needs to load a DLL file (for adding a feature like a video effect). By default, Windows checks the current folder, then system folders, then others. If an attacker manages to add their own DLL into the folder where Premiere Pro is loading a file (for example, the same folder as a project file), Premiere Pro might pick up and run that harmful DLL.
Attacker sends you a ZIP folder with a Premiere project file and a malicious DLL.
2. You open the Premiere project from inside the folder you unzipped (so Premiere Pro’s “current working directory” is the attacker-controlled folder).
Code Example: Malicious DLL
Let’s say an attacker makes a simple DLL that launches Calculator (just to prove it can run arbitrary code):
// attacker_dll.cpp
#include <windows.h>
BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved)
{
if (ul_reason_for_call == DLL_PROCESS_ATTACH) {
system("calc.exe"); // launches Windows Calculator
}
return TRUE;
}
They compile this file as a DLL (let’s say, example.dll) and place it in the same folder as a .prproj file.
If Premiere Pro tries to load example.dll and picks up the attacker's version, the calculator will pop up—proof the code is running in Premiere Pro's context.
For this vulnerability to be exploited
- The attacker needs to place a malicious DLL file in a folder where Premiere Pro will look for it.
- The victim must open a Premiere project or otherwise run Premiere Pro while its working folder is the one containing the malicious DLL.
If both conditions happen, the attacker's code runs with the user's permissions.
This usually means this vulnerability is most dangerous with file sharing (like when you download and open ZIP files or projects sent over email, Discord, or file-sharing services).
If you use Premiere Pro
- Update Premiere Pro to the latest version immediately. Adobe has patched this vulnerability—don’t wait!
- Never unzip and open Premiere projects from folders you don’t control or from untrusted sources.
Keep your antivirus up to date—most AVs will block or warn about known bad DLLs.
- Be careful with files from the internet, especially if they come with extra DLLs or EXEs in the same folder as your project.
Adobe Security Bulletin:
https://helpx.adobe.com/security/products/premiere_pro/apsb24-45.html
NIST NVD entry:
https://nvd.nist.gov/vuln/detail/CVE-2024-34123
MITRE Description:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-34123
Windows DLL Search Order explained:
https://learn.microsoft.com/en-us/windows/win32/dlls/dynamic-link-library-search-order
Conclusion
CVE-2024-34123 is a perfect example of how software can be tripped up by trust issues with file locations. If you work with Premiere Pro, or any software that loads plugins and DLLs, always think twice before opening projects from random sources. Update your software, stay alert, and help others do the same.
Stay safe and up-to-date!
*This post is prepared for educational purposes. For questions or collaboration, reach out!*
Timeline
Published on: 07/09/2024 19:15:11 UTC
Last modified on: 07/11/2024 13:06:13 UTC