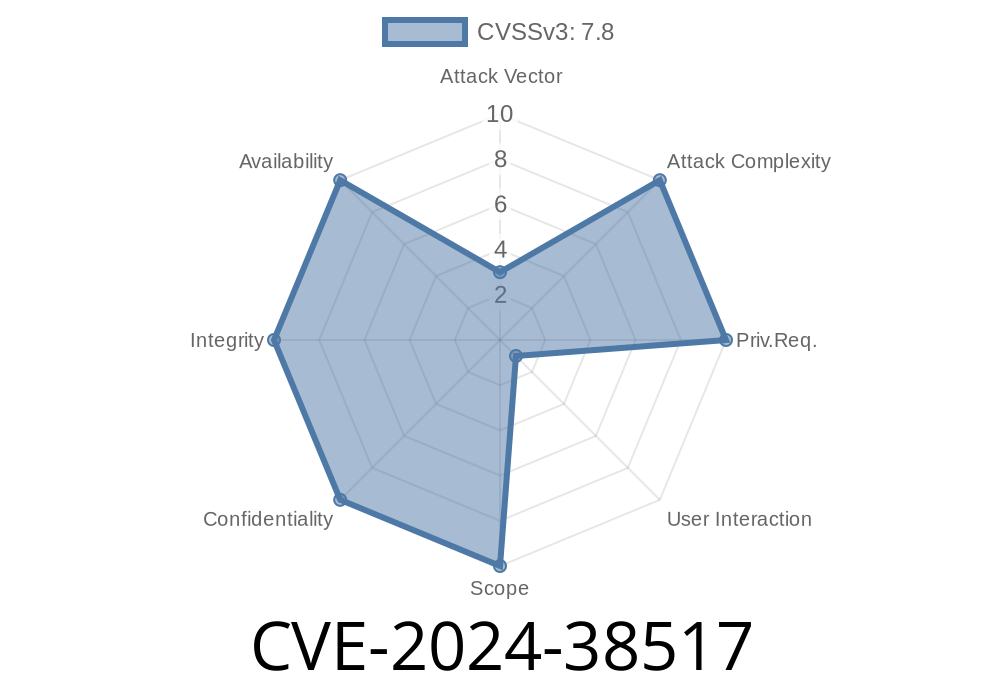
Tencent RapidJSON is a fast, popular C++ library for parsing and generating JSON. It's used across many projects and by millions of developers due to its speed and reliability. But recently, a new vulnerability was discovered that can let attackers elevate privileges on systems using RapidJSON. This post will break down CVE-2024-38517 in simple language, show you what's wrong in the code, explain how an attacker would exploit it, and provide links to original sources.
Library: RapidJSON (Tencent)
- Location: include/rapidjson/reader.h, inside the GenericReader::ParseNumber() function
Impact: Privilege escalation
- How triggered: A user opens a crafted JSON file from an attacker; RapidJSON parses it and the bug is triggered
Technical Details: What Went Wrong?
At the core of this issue is an integer underflow in the function ParseNumber(). An underflow happens when code subtracts from zero and wraps around to a huge number, because that's how unsigned numbers work in C/C++.
Here’s a simplified version of what goes wrong (example based on RapidJSON 1.1.)
template <typename InputStream>
bool ParseNumber(InputStream& is) {
int length = ;
// ... skipping irrelevant code ...
// This line is simplified and for illustration
char c = is.Peek();
while (IsDigit(c)) {
++length;
c = is.Take();
c = is.Peek();
}
if (length < ) {
// Underflow: possible privilege escalation
// Some code that assumes length cannot be negative
}
// ... more parsing code ...
}
In some code paths, especially if a specially crafted input is provided, length can underflow—meaning it becomes a *huge* integer thanks to C++ rules. If later on the value of length is used to allocate memory, copy data, or check boundaries, this paves the way for attackers to get code execution, or break out of the sandbox, elevating privileges.
Original code for context:
GitHub rapidjson/reader.h#L1973-L2014
How Exploitation Works
1. Attack Setup: The attacker creates a special JSON file with very large numbers or malformed number sections that trigger the underflow. For example:
`
2. Victim Opens File: The victim uses a RapidJSON-based application to open or import this crafted JSON.
3. Trigger Point: The ParseNumber() function reads the number, miscalculates lengths, underflows the integer.
4. What Happens Next: The underflowed value causes RapidJSON to overwrite memory, especially if it allocates a buffer or copies data using the wrong, huge size value.
5. Privilege Escalation: If the application is running with elevated rights, or parses JSON in a context where extra system permissions are possible, attackers can leverage this memory corruption to run code as a higher-privileged user.
Here’s a minimal file to potentially trigger this (may need adjustment per app)
{
"exploit": 18446744073709551616
}
*Note: 18446744073709551616 is 2^64—1 more than max unsigned 64-bit int; makes the parser go weird.*
If your app does anything special (like writes parsed values to protected files, or uses them in length calculations), this can open up privilege issues.
References and Resources
- Official RapidJSON GitHub
- CVE Official Listing for CVE-2024-38517 *(May update with details)*
- Rapijson reader.h Source
Conclusion
This vulnerability shows how even tiny mistakes in number handling can enable dangerous attacks—especially in a highly popular library like RapidJSON.
If your app processes JSON from the outside world, keep it up to date and watch out for integer underflows everywhere.
*Please responsibly disclose vulnerabilities and update your dependencies regularly. Stay secure!*
Timeline
Published on: 07/09/2024 19:15:12 UTC
Last modified on: 07/11/2024 13:06:13 UTC