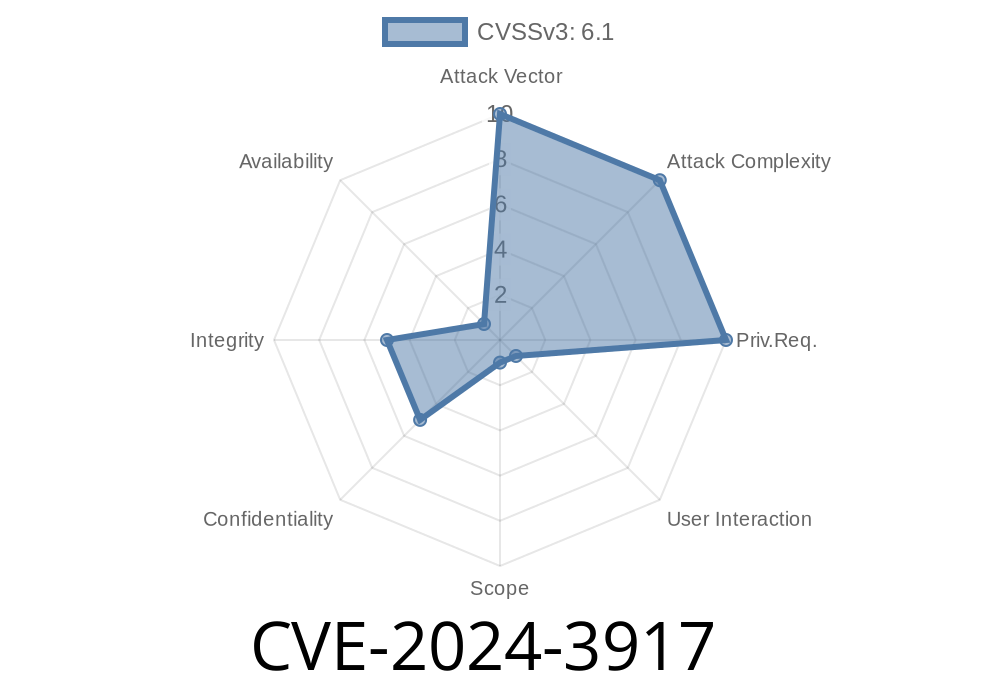
If you run a WordPress site and use the popular Pet Manager plugin, there’s a critical security issue you need to know. CVE-2024-3917 exposes a reflected cross-site scripting (XSS) bug in the plugin right up through version 1.4. This isn’t just any bug—it’s one that could let attackers target high-privilege users like you, the site admin, leading to site takeover, data theft, or worse.
In this guide, I’ll show you what’s wrong, how it works, and what you should do right now.
What is CVE-2024-3917?
Short answer:
It’s a security flaw in Pet Manager for WordPress, which fails to sanitize and escape a certain GET parameter before printing it back on the web page. This lets attackers inject malicious JavaScript that runs in the browser of anyone clicking a tainted link—including admins.
Inject malware throughout the site
All of this can happen silently, without you knowing.
This is a simplified snippet from the plugin’s PHP code
<?php
// Inside pet-manager/public/class-pet-manager-public.php
if ( isset($_GET['pet_name']) ) {
echo "<div>Welcome " . $_GET['pet_name'] . "</div>";
}
?>
What’s wrong with this?
There’s no sanitization or escaping! If someone provides malicious input in pet_name, it gets printed right into the page—with the browser executing it as HTML/JS.
Attackers craft a special URL and send it to a target (for example, an admin)
https://yourwordpresssite.com/pet-manager?pet_name=%3Cscript%3Ealert(document.cookie)%3C%2Fscript%3E
%3Cscript%3E is URL encoding for <script>
- When the admin clicks the link, the page will show a pop-up with their cookies (in this demo, but it could also silently steal their session!)
In a real attack, the injected code would send cookies or authentication tokens to a remote server or even execute backend commands using the admin’s credentials.
Try adding this to your URL (do NOT test this on a live site!)
?pet_name=%3Cscript%3Ealert("XSS!")%3C%2Fscript%3E
When the page loads, you’ll see a pop-up saying “XSS!”. That means JavaScript is running directly from the GET parameter without any safety checks—a textbook reflected XSS.
How to Fix It
For Developers:
ALWAYS sanitize and escape all user input before printing it out. Here’s a fix using WordPress’s built-in escaping functions:
<?php
if ( isset($_GET['pet_name']) ) {
echo "<div>Welcome " . esc_html($_GET['pet_name']) . "</div>";
}
?>
This way, if someone tries to inject a script, it’s displayed as text and not executed.
For Site Owners:
References
- WPScan Advisory - CVE-2024-3917
- Pet Manager Plugin (WordPress.org)
- OWASP: Cross-Site Scripting (XSS)
Final Words
CVE-2024-3917 is a reminder that even a single unsanitized parameter can give attackers the keys to your kingdom. If you use Pet Manager on WordPress, check your plugin version and update it immediately once a patch is released. Until then, staying informed is your best defense.
Timeline
Published on: 05/23/2024 06:15:10 UTC
Last modified on: 07/03/2024 02:06:53 UTC